-
摘要:
针对轻量级杂凑函数的线性层结构单一易受统计饱和攻击的问题,提出一种以海绵结构为主体,内部置换函数为仿射变换S盒结构的轻量级杂凑函数。仿射变换后的S盒继承了原S盒良好的密码特性,同时在很大程度上弥补了线性层结构过于简单的不足。根据最优4 bit最优S盒仿射等价类的具有最大差分概率的差分对个数、具有最优线性逼近关系的掩码个数及最大分支数确定了仿射变换S盒原型;通过差分及线性密码分析、统计饱和攻击分析了内部置换结构的安全性;设计了仿射变换结构的控制逻辑及算法整体的串/并行硬件实现方案,并在Design Compiler上进行了综合验证。结果表明,基于仿射变换S盒的轻量级杂凑函数在只加入了一些简单控制逻辑的情况下,提高了统计饱和分析中追踪特定比特位扩散路径的难度,即仿射变换结构增加了线性扩散层的混淆性,优化了其抗统计饱和攻击的能力。
Abstract:Linear layer of lightweight hash functions is ordinarily too simple to resist statistical saturation attack. A novel lightweight hash function is proposed, which is based on the sponge structure and inspired by affine transformation S-box. The affine transformation S-box inherit the excellent cryptographic properties of original S-box, and offset lack of simple linear layer to a great extent as well. The original 4 bit S-box is selected by computing numbers of differential pairs with the largest differential probability, masks with the best linear approximation and maximum branch number of optimal S-box affine equivalent classes. Security of holistic and internal primitives is analyzed with differential and linear cryptanalysis, and especially statistical saturation attack.The control logic of affine transformation structure and the serial/parallel hardware architecture are designed and synthesized by Design Compiler. The results show that in case of adding a few control logic, the lightweight hash function with affine transformation S-box increases difficulty of tracing specific bit in diffusion trail, that is, structures of affine transformations increase confusion of linear diffusion layer and improve the ability against statistical saturation attack.
-
Key words:
- lightweight /
- hash function /
- S-box /
- affine transformation /
- statistical saturation analysis
-
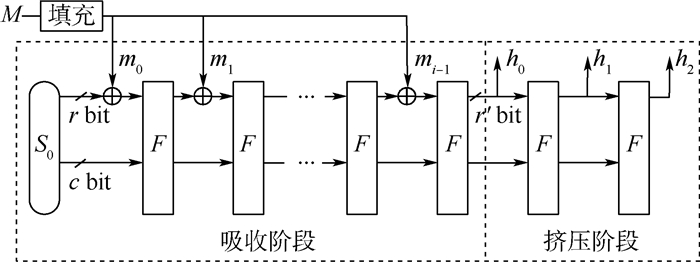
表 1 海绵结构参数
Table 1. Parameters of sponge structure
参数 含义 M 输入消息 S0 初始迭代状态 mi 第i组分组消息块 hi 输出第i组消息块 r 分组长度 F 内部置换函数 r′ 每轮输出消息长度 c 不与消息异或部分长度 b(b=r+c) 内部迭代状态长度 n 输出消息长度 表 2 同类型轻量级杂凑函数安全边界
Table 2. Security boundaries of similar lightweight hash functions
轻量级杂凑函数 安全性/bit 第一原象安全性 第二原象安全性 抗碰撞性 ATSHash-88/80/16 72 40 40 ATSHash-88/88/8 80 44 44 ATSHash-144/128/32 112 64 64 ATSHash-144/144/16 128 72 72 SPONGENT-88/80/8 80 40 40 SPONGENT-128/128/8 120 64 64 PHOTON-80/80/16 64 40 40 PHOTON-128/128/16 112 64 64 S盒 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, F G0 0, 1, 2, D, 4, 7, F, 6, 8, B, C, 9, 3, E, A, 5 G1 0, 1, 2, D, 4, 7, F, 6, 8, B, E, 3, 5, 9, A, C G2 0, 1, 2, D, 4, 7, F, 6, 8, B, E, 3, A, C, 5, 9 G3 0, 1, 2, D, 4, 7, F, 6, 8, C, 5, 3, A, E, B, 9 G4 0, 1, 2, D, 4, 7, F, 6, 8, C, 9, B, A, E, 5, 3 G5 0, 1, 2, D, 4, 7, F, 6, 8, C, B, 9, A, E, 3, 5 G6 0, 1, 2, D, 4, 7, F, 6, 8, C, B, 9, A, E, 5, 3 G7 0, 1, 2, D, 4, 7, F, 6, 8, C, E, B, A, 9, 3, 5 G8 0, 1, 2, D, 4, 7, F, 6, 8, E, 9, 5, A, B, 3, C G9 0, 1, 2, D, 4, 7, F, 6, 8, E, B, 3, 5, 9, A, C G10 0, 1, 2, D, 4, 7, F, 6, 8, E, B, 5, A, 9, 3, C G11 0, 1, 2, D, 4, 7, F, 6, 8, E, B, A, 5, 9, C, 3 G12 0, 1, 2, D, 4, 7, F, 6, 8, E, B, A, 9, 3, C, 5 G13 0, 1, 2, D, 4, 7, F, 6, 8, E, C, 9, 5, B, A, 3 G14 0, 1, 2, D, 4, 7, F, 6, 8, E, C, B, 3, 9, 5, A G15 0, 1, 2, D, 4, 7, F, 6, 8, E, C, B, 9, 3, A, 5 表 4 最优4 bit S盒的密码特性
Table 4. Cryptographic properties of optimal 4 bit S-box
S盒 ND(S) NL(S) B G0 24 36 3 G1 24 36 3 G2 24 36 3 G3 15 30 2 G4 15 30 2 G5 15 30 2 G6 15 30 2 G7 15 30 2 G8 24 36 2 G9 18 32 3 G10 18 32 3 G11 15 30 2 G12 15 30 2 G13 15 30 2 G14 18 32 3 G15 18 32 3 表 5 仿射变换S盒
Table 5. Affine transformation S-boxes
SS 输出 仿射变换S盒 00 y3‖y0‖y2‖y1 S(0):0, 4, 1, E, 2, 7, F, 3, 8, B, D, 5, 6, C, 9, A 01 y1‖y0‖y3‖y2 S(1):0, 1, 8, 7, 4, D, F, 9, 2, B, E, C, 5, 6, A, 3 10 y1‖y2‖y3‖y0 S(2):0, 1, 8, 7, 4, D, F, C, 2, E, B, 9, 5, 3, A, 6 11 y2‖y0‖y3‖y1 S(3):0, 4, 1, E, 8, D, F, 9, 2, B, 7, 5, C, 6, 3, A 表 6 差分活动S盒数量下界
Table 6. Lowest numbers of differentially active S-box
轮数 差分活动S盒数量 ATSHash-96 ATSHash-160 5 10 10 10 21 24 15 31 41 20 42 56 表 7 同类型轻量级杂凑函数族的硬件实现
Table 7. Hardware implementation of similar lightweight hash functions
轻量级杂凑函数 位宽/
bit轮数 面积/GE UMC180 nm 吞吐率/(kb·s-1)@100 kHz ATSHash-88/80/16 4 1 152 832 1.02(0.18 μm) 96 48 1 334 19.26(0.18 μm) ATSHash-144/128/32 4 3 200 1 260 0.48(0.18 μm) 160 80 2 129 16.62(0.18 μm) SPONGENT-88/80/8 4 990 759 0.81(0.13 μm) 88 45 1 232 17.78(0.13 μm) SPONGENT-160/160/16 4 3 960 1 367 0.40(0.13 μm) 176 90 2 241 17.78(0.13 μm) PHOTON-80/80/16 4 708 856 2.82(0.18 μm) 20 132 1 151 15.15(0.18 μm) PHOTON-128/128/16 4 996 1 394 1.61(0.18 μm) 24 156 2 172 10.26(0.18 μm) -
[1] MURAMATSU J, MIYAKE S.Hash property and fixed-rate universal coding theorems[J].IEEE Information Theory Society, 2010, 56(6):2688-2698. doi: 10.1109/TIT.2010.2046214 [2] SAM L, SAM A, PATRICK V T, et al.Wearable flexible lightweight modular RFID tag with intergrated energy harvester[J].IEEE Transactions on Microwave Theory and Techniques, 2016, 64(7):2304-2314. doi: 10.1109/TMTT.2016.2573274 [3] IGNACIO A B, CLAUDIA F U, RENE C, et al.Design and implementation of a non-pipelined MD5 hardware architecture using a new functional description[J].IEICE Transactions on Information and Systems, 2008, E91-D(10):2519-2523. doi: 10.1093/ietisy/e91-d.10.2519 [4] HILARIE O.Recent parables in cryptography[J].IEEE Internet Computing, 2014, 18(1):82-86. doi: 10.1109/MIC.2014.13 [5] WILLIAM E B.A new hash competition[J].IEEE Security & Privacy, 2008, 6(3):60-62. http://ieeexplore.ieee.org/document/4530402/ [6] AUMASSON J P, HENZEN L, MEIER W, et al.Quark:A lightweight hash[J].Journal of Cryptology, 2013, 26(2):313-339. doi: 10.1007/s00145-012-9125-6 [7] DING L, JIN C H, GUAN J.New state recovery attacks on the Grain v1 stream cipher[J].China Communication, 2016, 13(11):180-188. doi: 10.1109/CC.2016.7781728 [8] CANNIōRE D, DUNKELMAN O, KNEŽEVIC'M. KATAN and KTANTAN: A family of small and efficient hardware-oriented block ciphers[C]//Proceedings of 11th International Workshop on Cryptographic Hardware and Embedded Systems. Berlin: Springer, 2009: 272-288. [9] GUO J, PEYRIN T, POSCHMANN A, et al. The PHOTON family of lightweight hash functions[C]//Advances in Cryptology-CRYPTO. Berlin: Springer, 2011: 222-239. [10] ISSAM H, KAMAL E S, EZZ E M, et al.High-speed AES encryptor with efficient merging techniques[J].IEEE Embedded Systems Letters, 2010, 2(3):67-71. doi: 10.1109/LES.2010.2052401 [11] BOGDANOV A, KNEZENIV M, LEANDER G.SPONGENT:The design space of lightweight cryptographic hashing[J].IEEE Transactions on Computers, 2013, 62(10):2041-2053. doi: 10.1109/TC.2012.196 [12] BOGDANOV A, KNEZENIV M, LEANDER G. PRESENT: An ultra lightweight block cipher[C]//Proceedings of 9th International Workshop on Cryptographic Hardware and Embedded Systems. Berlin: Springer, 2007: 450-466. [13] COLLARD B, STANDAERT F X. A statistical saturation attack against the block cipher PRESENT[C]//The Cryptographers Track at RSA Conference 2009. Berilin: Springer, 2009: 195-211. [14] CHARANJIT S J, ANINDYA C P.Provably good codes for Hash function design[J].IEEE Transactions on Information Theory, 2009, 55(1):33-45. http://ieeexplore.ieee.org/document/4729745/ [15] BERTONI G, DAEMEN J, PEETERS M. Sponge based pseudo-random number generators[C]//Proceedings of 12th International Conference Cryptographic Hardware and Embedded Systems. Berlin: Springer, 2010: 33-47. [16] LIM C, KORKISHKO T. MCrypton: A lightweight block cipher for security of low-cost RFID tags and sensors[C]//Information Security Applications: 6th International Workshop, WISA 2005. Berlin: Springer, 3786: 243-258. [17] LEANDER G, POSCHMANN A. On the classification of 4 bit S-BOX[C]//Arithmetic of Finite Fields: First International Workshop, WAIFI 2007. Berlin: Springer, 2007: 159-176. -







 下载:
下载: