UAV network intrusion detection method based on spatio-temporal graph convolutional network
-
摘要:
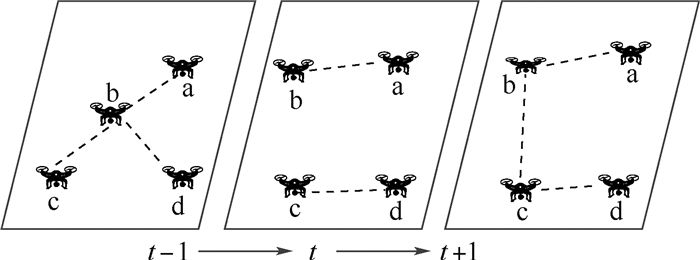
无人机网络相比地面网络具有节点快速移动、拓扑结构变换频繁和通信链路不可靠的特点,传统的针对地面网络的入侵检测方法难以适用。针对无人机网络的时空动态特性进行建模,提出了一种无人机网络的入侵检测方法——基于注意力机制的时空图卷积网络(ATGCN)。将图卷积网络和门控递归单元组合为时空图卷积网络,从复杂多变的数据中提取网络的时空演变特征,通过注意力机制提取和入侵检测最相关的特征,输入支持向量机进行分类预测。多个数据集的实验分析表明:所提方法能够适应无人机网络的动态性和不稳定性,相比传统检测方法准确率高且误报率低,具有良好的鲁棒性和适应性。
Abstract:Compared with ground networks, UAV networks have the characteristics of fast moving nodes, frequent topology changes, and unreliable communication links. Traditional intrusion detection methods are difficult to apply. Aimed at the spatio-temporal dynamic characteristics of UAV networks, an intrusion detection method:Attention-based Spatio-Temporal Graph Convolutional Network (ATGCN) is proposed, which combines graph convolutional network and gated recursive unit into spatio-temporal graph convolutional network. The spatio-temporal graph convolutional network extracts the spatio-temporal evolution characteristics of the network from complex and changeable data, attention mechanism is used to extract the features most relevant to intrusion detection, and the support vector machine is used as the last layer of the model for classification to identify network attacks. The experimental analysis of multiple datasets shows that the proposed method can adapt to the dynamics and instability of UAV networks, has higher accuracy and lower false positive rate than traditional detection methods, and has good robustness and adaptability.
-
表 1 数据集相关信息
Table 1. Relevant information of datasets
数据集 网络攻击类别 WSN-DS 黑洞攻击,灰洞攻击,泛洪攻击,调度攻击 NSL-KDD 拒绝服务攻击,监视和其他探测活动,远程机器的非法访问,普通用户对本地超级用户特权的非法访问 CICIDS2017 FTP暴力破解、SSH暴力破解,拒绝服务攻击,心血漏洞,网页攻击,渗透攻击,僵尸网络 表 2 仿真参数
Table 2. Simulation parameters
参数 数值 仿真区域/(m×m) 1 000×1 000 节点数量 50 节点移动模型 随机路径模型 信道容量/(Mbit·s-1) 5 最大移动速度/(m·s-1) 20 攻击节点比例/% 10、20、30 路由协议类型 AODV 采样周期/s 15 表 3 UAV_set数据集相关信息
Table 3. Relevant information of UAV_set dataset
流量类别 数量 正常 2 000 窃听攻击 500 DDoS攻击 700 黑洞攻击 110 表 4 不同方法的实验结果比较
Table 4. Comparison of experimental results among different methods
方法 准确率 误报率 WSN-DS NSL-KDD CICIDS2017 UAV_set WSN-DS NSL-KDD CICIDS2017 UAV_set IF 0.457 0.916 0.735 0.855 0.368 0.145 0.235 0.124 LOF 0.435 0.536 0.669 0.892 0.134 0.127 0.168 0.125 RF 0.886 0.919 0.894 0.884 0.101 0.074 0.096 0.244 MCD 0.610 0.716 0.793 0.863 0.190 0.126 0.122 0.223 OCSVM 0.605 0.880 0.793 0.783 0.201 0.174 0.155 0.117 VAE 0.887 0.916 0.956 0.922 0.027 0.016 0.017 0.022 DAGMM 0.968 0.987 0.992 0.995 0.028 0.044 0.024 0.010 ATGCN 0.988 0.998 0.996 0.997 0.019 0.007 0.016 0.009 -
[1] 何道敬, 杜晓, 乔银荣, 等.无人机信息安全研究综述[J].计算机学报, 2019, 42(5):150-168. https://www.cnki.com.cn/Article/CJFDTOTAL-JSJX201905010.htmHE D J, DU X, QIAO Y R, et al.A survey on cyber security of unmanned aerial vehicles[J].Chinese Journal of Computers, 2019, 42(5):150-168(in Chinese). https://www.cnki.com.cn/Article/CJFDTOTAL-JSJX201905010.htm [2] JAWHAR I, MOHAMED N, AL-JAROODI J, et al.Communication and networking of UAV-based systems:Classification and associated architectures[J].Journal of Network and Computer Applications, 2017, 84:93-108. doi: 10.1016/j.jnca.2017.02.008 [3] KUMAR N, KUMAR U.Anomaly-based network intrusion detection: An outlier detection techniques[C]//International Conference on Soft Computing and Pattern Recognition.Berlin: Springer, 2016: 262-269. [4] ZIMEK A, FILZMOSER P.There and back again:Outlier detection between statistical reasoning and data mining algorithms[J].Wiley Interdisciplinary Reviews:Data Mining and Knowledge Discovery, 2018, 8(6):e1280. doi: 10.1002/widm.1280 [5] DIVYA K, KUMARAN N S.Survey on outlier detection techniques using categorical data[J].International Research Journal of Engineering and Technology, 2016, 3(12):899-904. http://www.researchgate.net/publication/289244225_A_Survey_On_Outlier_Detection_Technique_In_Streaming_Data_Using_Data_Clustering_Approach [6] DESHMUKH M M K, KAPSE A.A survey on outlier detection technique in streaming data using data clustering approach[J].International Journal of Engineering and Computer Science, 2016, 5(1):15453-15456. http://www.researchgate.net/publication/289244225_A_Survey_On_Outlier_Detection_Technique_In_Streaming_Data_Using_Data_Clustering_Approach [7] JIANG F, LIU G, DU J, et al.Initialization of K-modes clustering using outlier detection techniques[J].Information Sciences, 2016, 332:167-183. doi: 10.1016/j.ins.2015.11.005 [8] CHEN J, SATHE S, AGGARWAL C, et al.Outlier detection with autoencoder ensembles[C]//Proceedings of the 2017 SIAM International Conference on Data Mining, 2017: 90-98. [9] KWON D, KIM H, KIM J, et al.A survey of deep learning-based network anomaly detection[J].Cluster Computing, 2019, 22:949-961. doi: 10.1007/s10586-017-1117-8 [10] ZONG B, SONG Q, MIN M R, et al.Deep autoencoding Gaussian mixture model for unsupervised anomaly detection[C]//ICLR, 2018: 1-19. [11] DOMINGUES R, FILIPPONE M, MICHIARDI P, et al.A comparative evaluation of outlier detection algorithms:Experiments and analyses[J].Pattern Recognition, 2018, 74:406-421. doi: 10.1016/j.patcog.2017.09.037 [12] CHAWLA A, LEE B, FALLON S, et al.Host based intrusion detection system with combined CNN/RNN model[C]//Joint European Conference on Machine Learning and Knowledge Discovery in Databases.Berlin: Springer, 2018: 149-158. [13] SHONE N, NGOC T N, PHAI V D, et al.A deep learning approach to network intrusion detection[J].IEEE Transactions on Emerging Topics in Computational Intelligence, 2018, 2(1):41-50. doi: 10.1109/TETCI.2017.2772792 [14] TAN X, SU S, ZUO Z, et al.Intrusion detection of UAVs based on the deep belief network optimized by PSO[J].Sensors, 2019, 19(24):5529. doi: 10.3390/s19245529 [15] KIM G, YI H, LEE J, et al.LSTM-based system-call language modeling and robust ensemble method for designing host-based intrusion detection systems[EB/OL].(2016-11-06)[2020-03-01].https://arxiv.org/abs/1611.01726. [16] WANG W, SHENG Y, WANG J, et al.HAST-IDS:Learning hierarchical spatial-temporal features using deep neural networks to improve intrusion detection[J].IEEE Access, 2017, 6:1792-1806. http://ieeexplore.ieee.org/document/8171733 [17] ZHANG Z, CUI P, ZHU W.Deep learning on graphs: A survey[EB/OL].(2018-12-11)[2020-03-01].https://arxiv.org/abs/1812.04202v1. [18] ZHENG J, LI D.GCN-TC: Combining trace graph with statistical features for network traffic classification[C]//IEEE International Conference on Communications.Piscataway: IEEE Press, 2019: 1-6. [19] HSU D.Anomaly detection on graph time series[EB/OL].(2017-08-09)[2020-03-01].https://arxiv.org/abs/1708.02975. [20] ZHAO L, SONG Y, ZHANG C, et al.T-GCN:A temporal graph convolutional network for traffic prediction[J].IEEE Transactions on Intelligent Transportation Systems, 2020, 21(9):3848-3858. doi: 10.1109/TITS.2019.2935152 [21] DEY R, SALEMT F M.Gate-variants of gated recurrent unit (GRU) neural networks[C]//IEEE 60th International Midwest Symposium on Circuits and Systems.Piscataway: IEEE Press, 2017: 1597-1600. [22] LEE J B, ROSSI R A, KIM S, et al.Attention models in graphs:A survey[J].ACM Transactions on Knowledge Discovery from Data (TKDD), 2019, 13(6):1-25. [23] TAVALLAEE M, BAGHERI E, LU W, et al.A detailed analysis of the KDD CUP 99 data set[C]//IEEE Symposium on Computational Intelligence for Security and Defense Applications.Piscataway: IEEE Press, 2009: 1-6. [24] SHARAFALDIN I, LASHKARI A H, GHORBANI A A.Toward generating a new intrusion detection dataset and intrusion traffic characterization[C]//Proceedings of the 4th International Conference on Information Systems Security and Privacy, 2018: 108-116. [25] ALMOMANI I, AL-KASASBEH B, AL-AKHRAS M.WSN-DS:A dataset for intrusion detection systems in wireless sensor networks[J].Journal of Sensors, 2016, 2016:1-16. http://www.researchgate.net/publication/308751926_WSN-DS_A_Dataset_for_Intrusion_Detection_Systems_in_Wireless_Sensor_Networks?ivk_sa=1024320u [26] 张冰涛, 王小鹏, 王履程, 等.基于图论的MANET入侵检测方法[J].电子与信息学报, 2018, 40(6):1446-1452. https://www.cnki.com.cn/Article/CJFDTOTAL-DZYX201806025.htmZHANG B T, WANG X P, WANG L C, et al.Intrusion detection method for MANET based on graph theory[J].Journal of Electronics and Information Technology, 2018, 40(6):1446-1452(in Chinese). https://www.cnki.com.cn/Article/CJFDTOTAL-DZYX201806025.htm [27] SUN L, VERSTEEG S, BOZTAS S, et al.Detecting anomalous user behavior using an extended isolation forest algorithm: An enterprise case study[EB/OL].(2016-09-21)[2020-03-01].https://arxiv.org/abs/1609.06676. [28] 杨晓晖, 张圣昌.基于多粒度级联孤立森林算法的异常检测模型[J].通信学报, 2019, 40(8):133-142. https://www.cnki.com.cn/Article/CJFDTOTAL-TXXB201908013.htmYANG X H, ZHANG S C.Anomaly detection model based on multi-grained cascade isolation forest algorithm[J].Journal on Communications, 2019, 40(8):133-142(in Chinese). https://www.cnki.com.cn/Article/CJFDTOTAL-TXXB201908013.htm [29] BHARAMBE A, RAVINDRAN R, SUCHDEV R, et al.A robust anomaly detection system[C]//2014 International Conference on Advances in Engineering & Technology Research.Piscataway: IEEE Press, 2014: 1-7. [30] SHANG W, ZENG P, WAN M, et al.Intrusion detection algorithm based on OCSVM in industrial control system[J].Security and Communication Networks, 2016, 9(10):1040-1049. doi: 10.1002/sec.1398 [31] LOPEZ-MARTIN M, CARRO B, SANCHEZ-ESGUEVILLAS A, et al.Conditional variational autoencoder for prediction and feature recovery applied to intrusion detection in iot[J].Sensors, 2017, 17(9):1967. doi: 10.3390/s17091967 [32] ZHANG Y, SZABO C, SHENG Q Z.Cleaning environmental sensing data streams based on individual sensor reliability[C]//International Conference on Web Information Systems Engineering.Berlin: Springer, 2014: 405-414. -







 下载:
下载: