-
摘要:
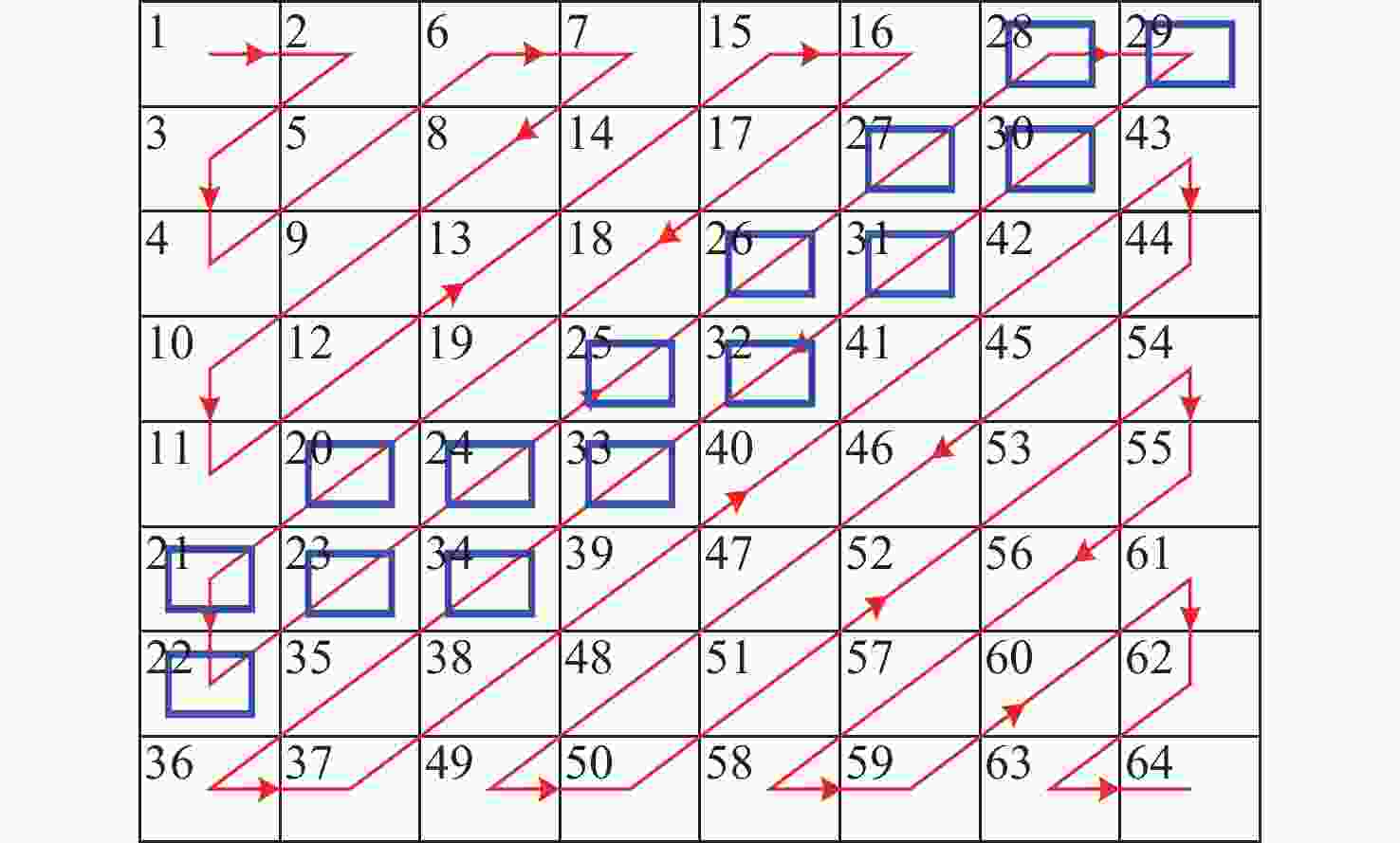
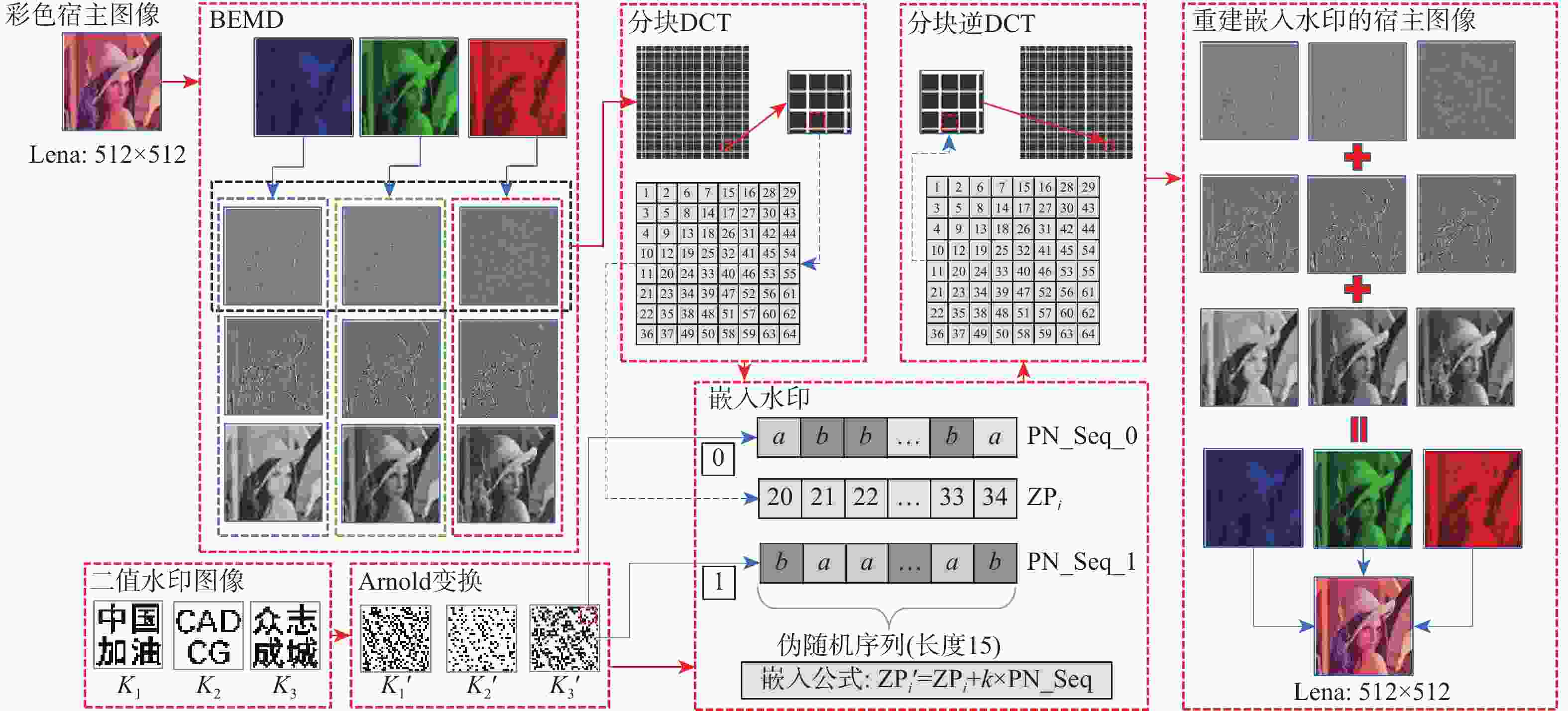
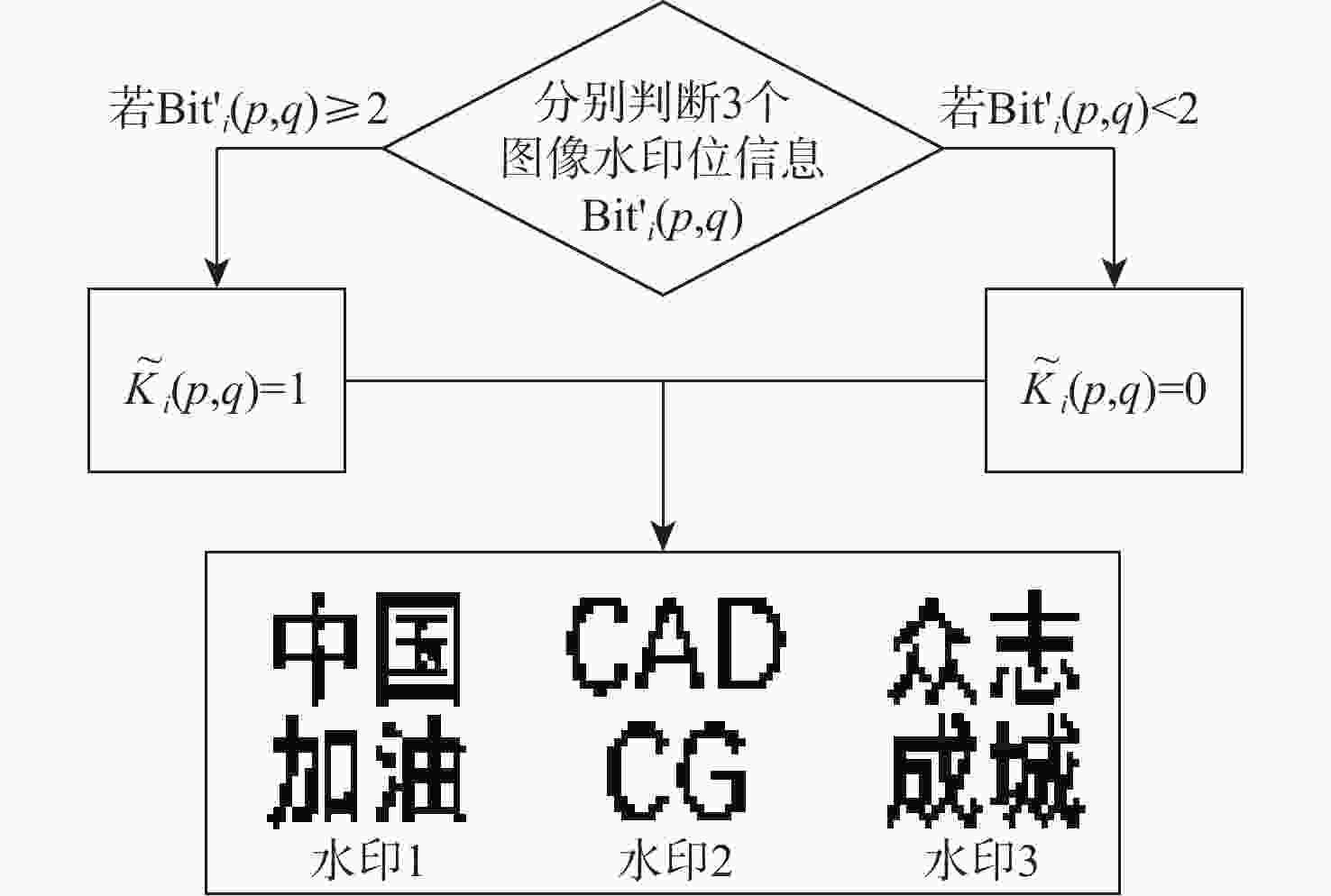
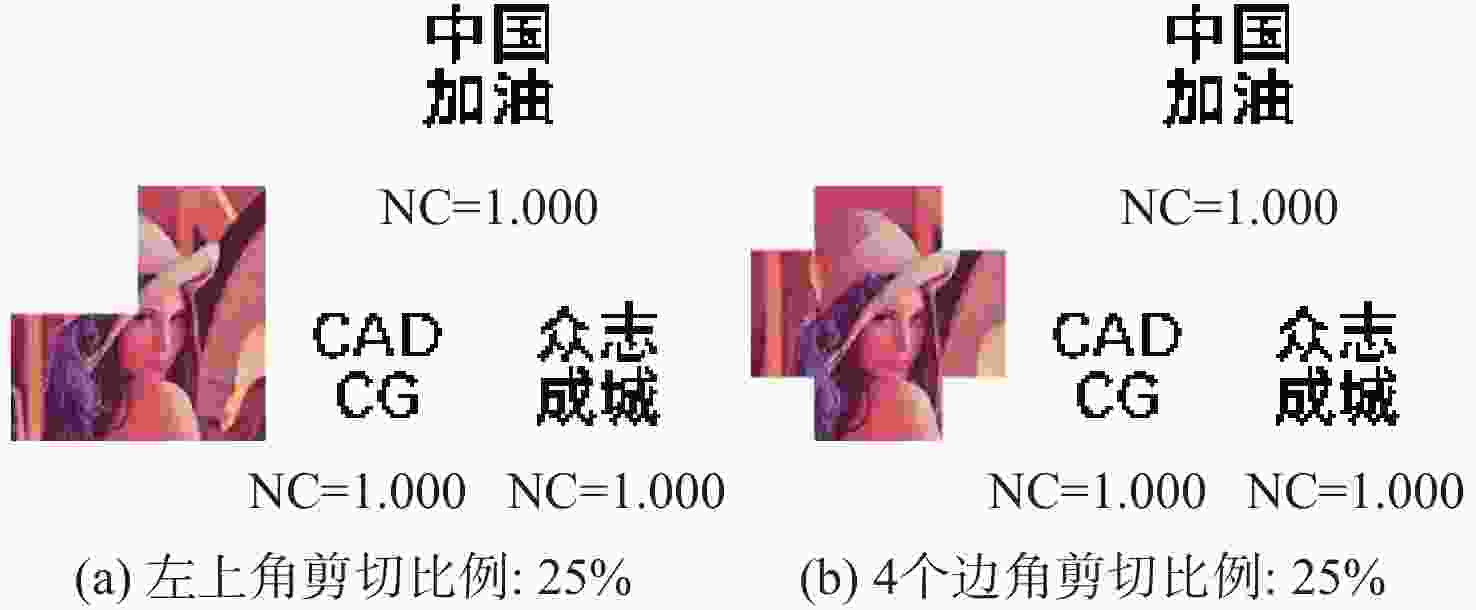
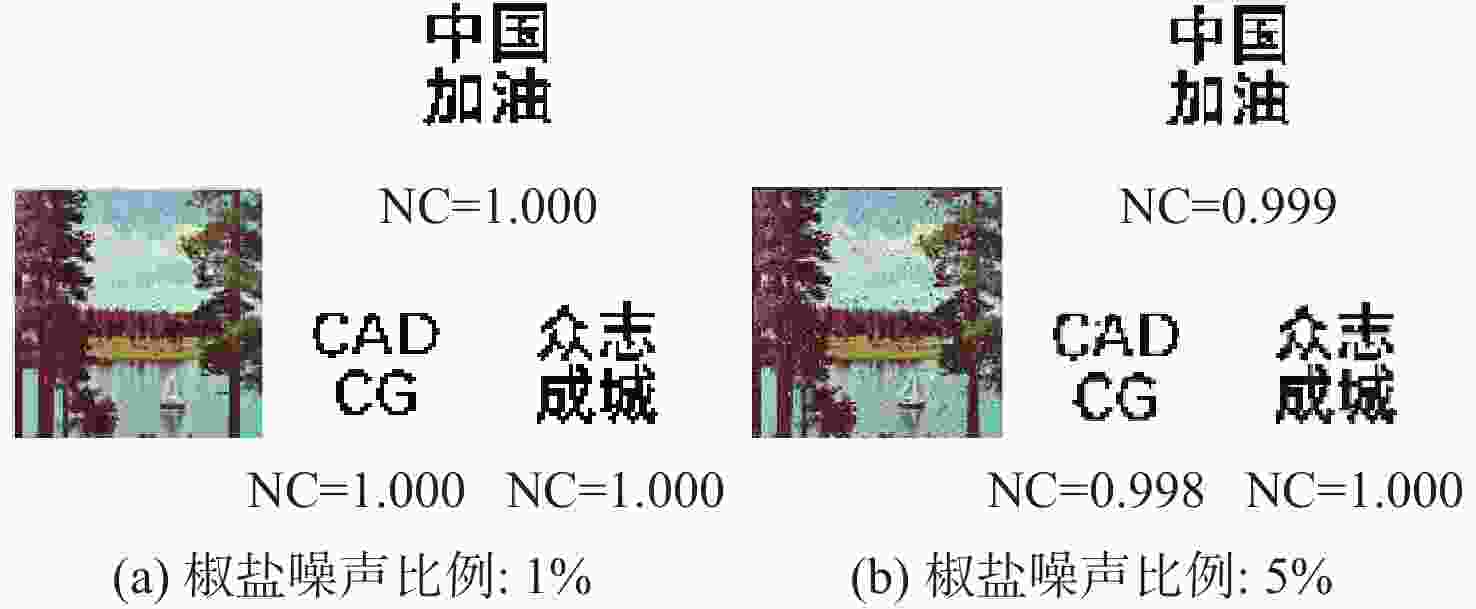
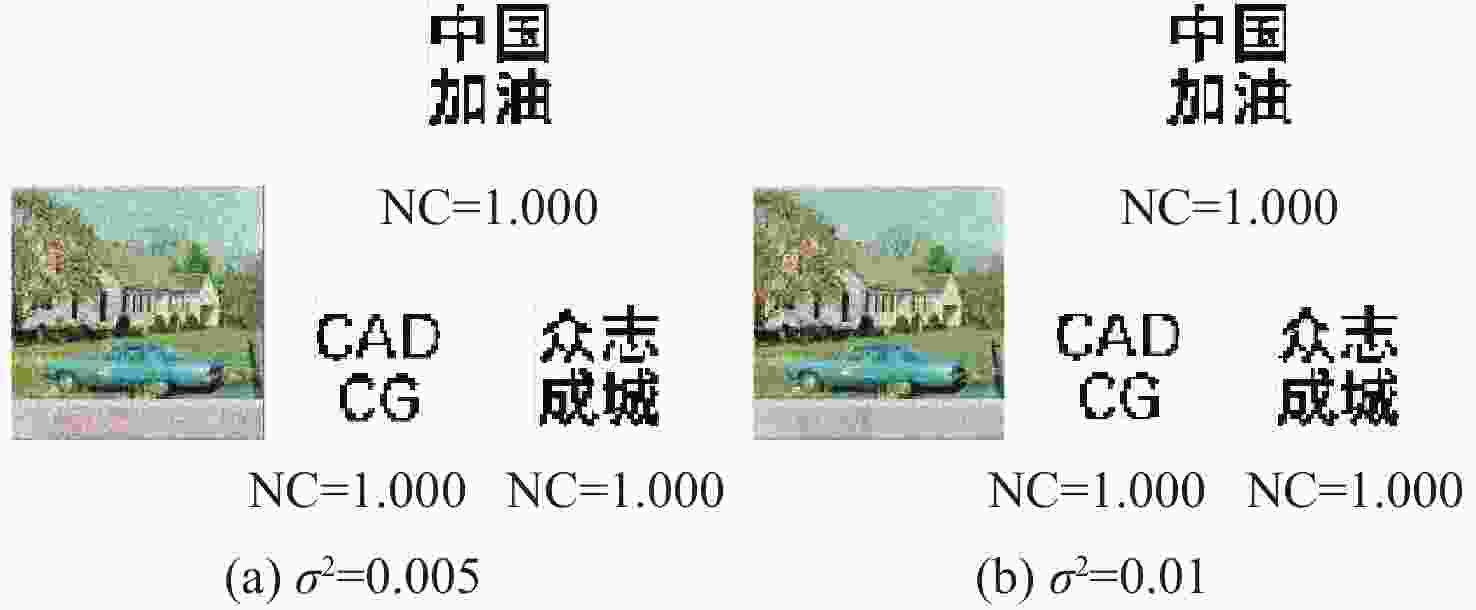
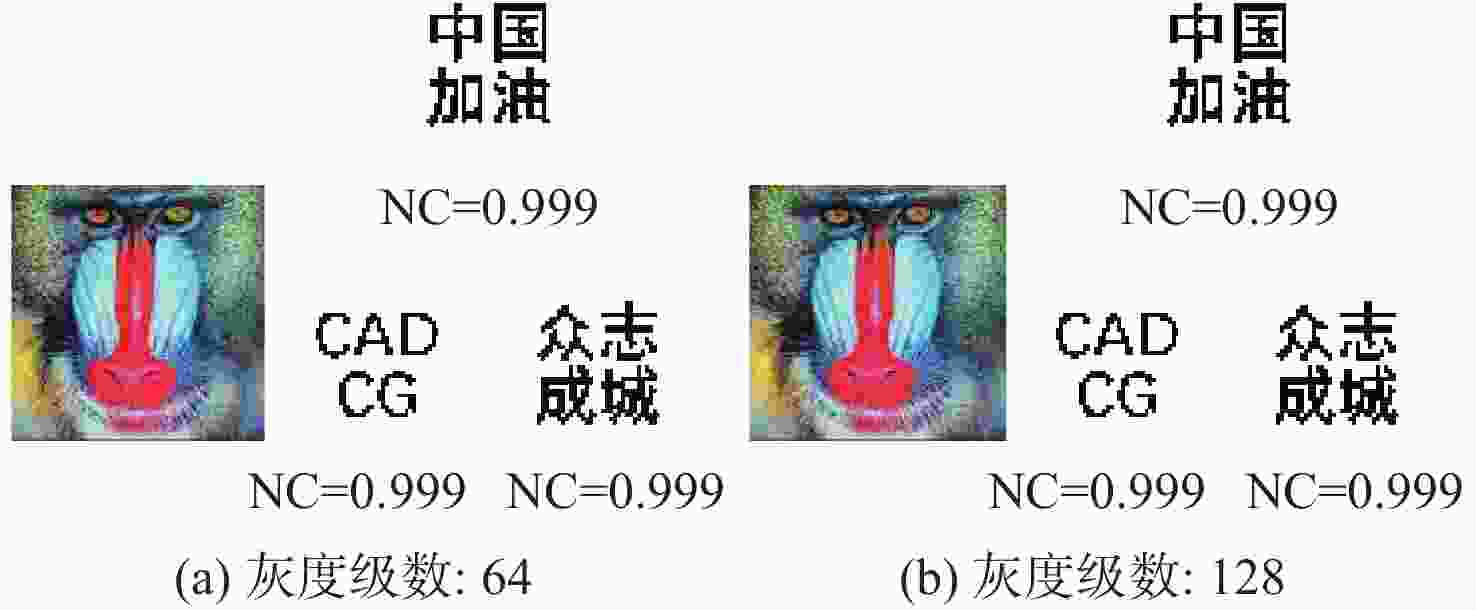
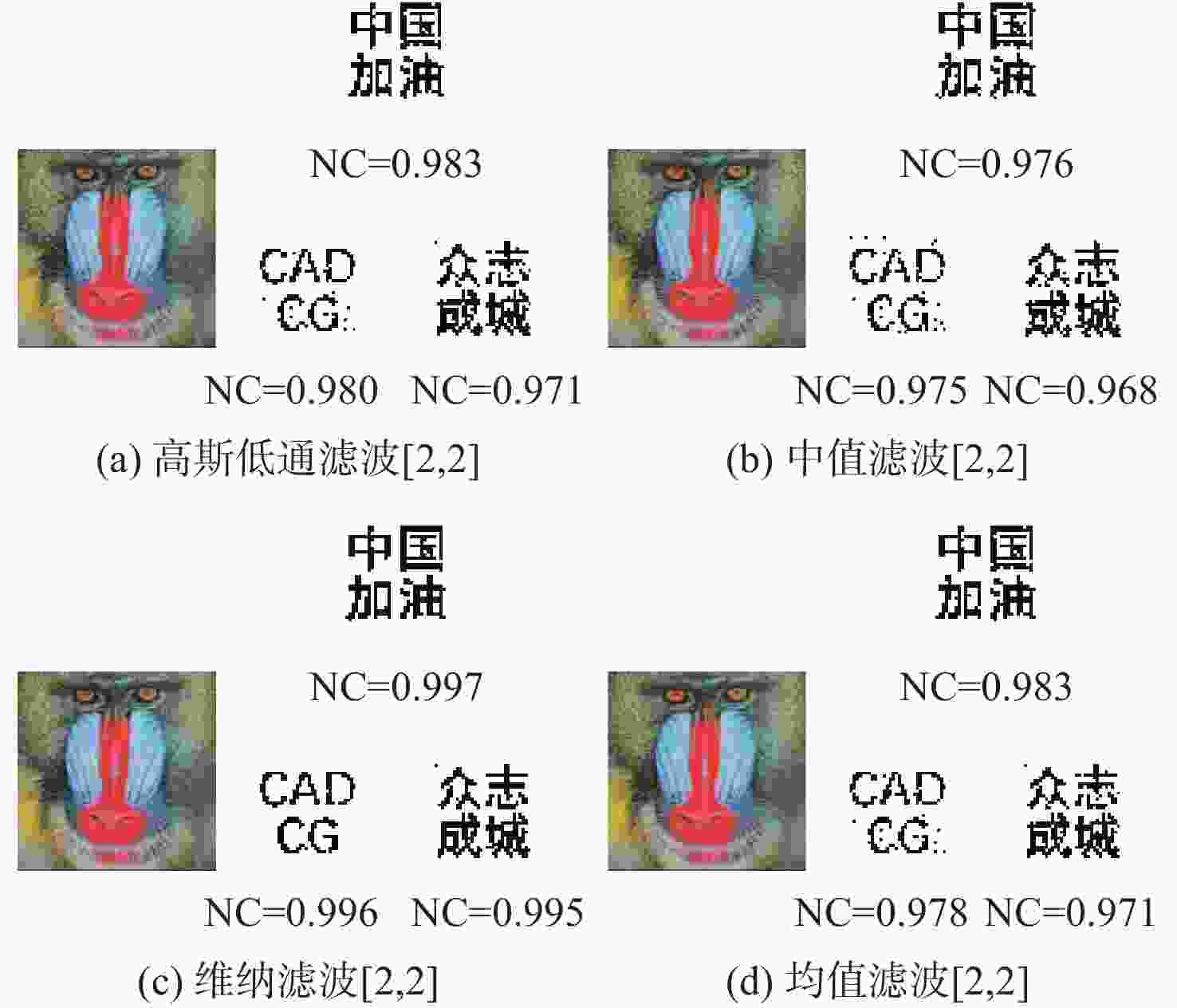
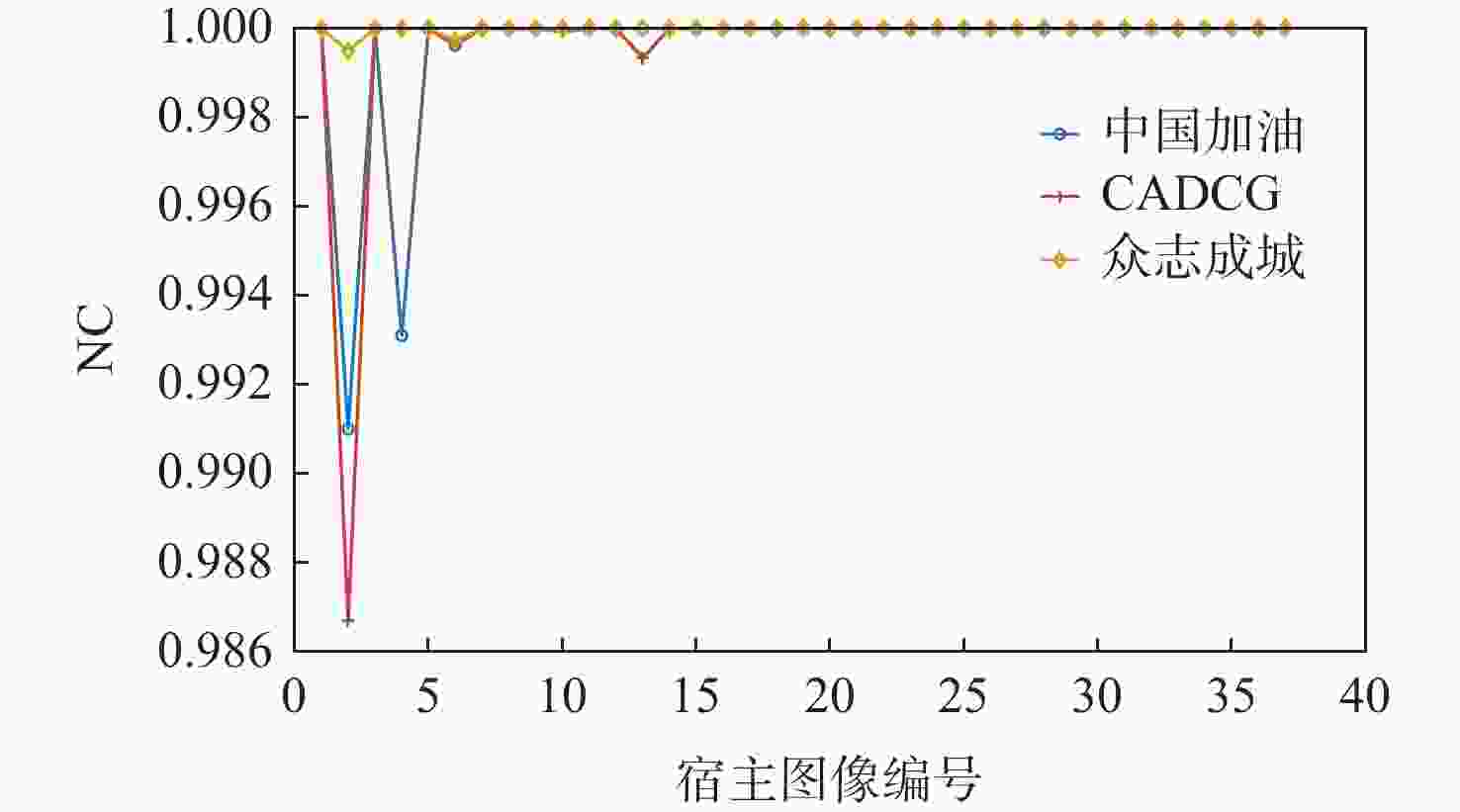
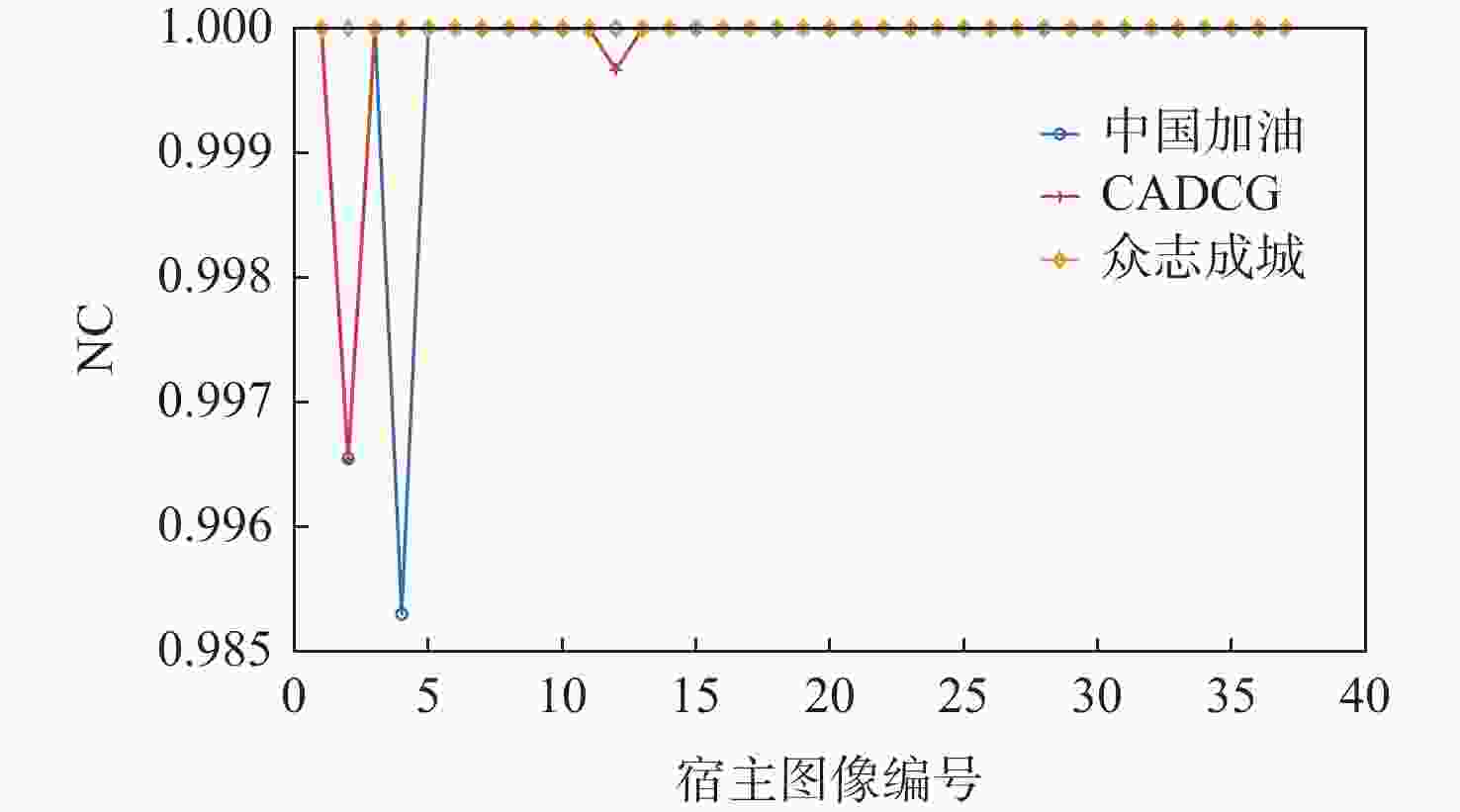
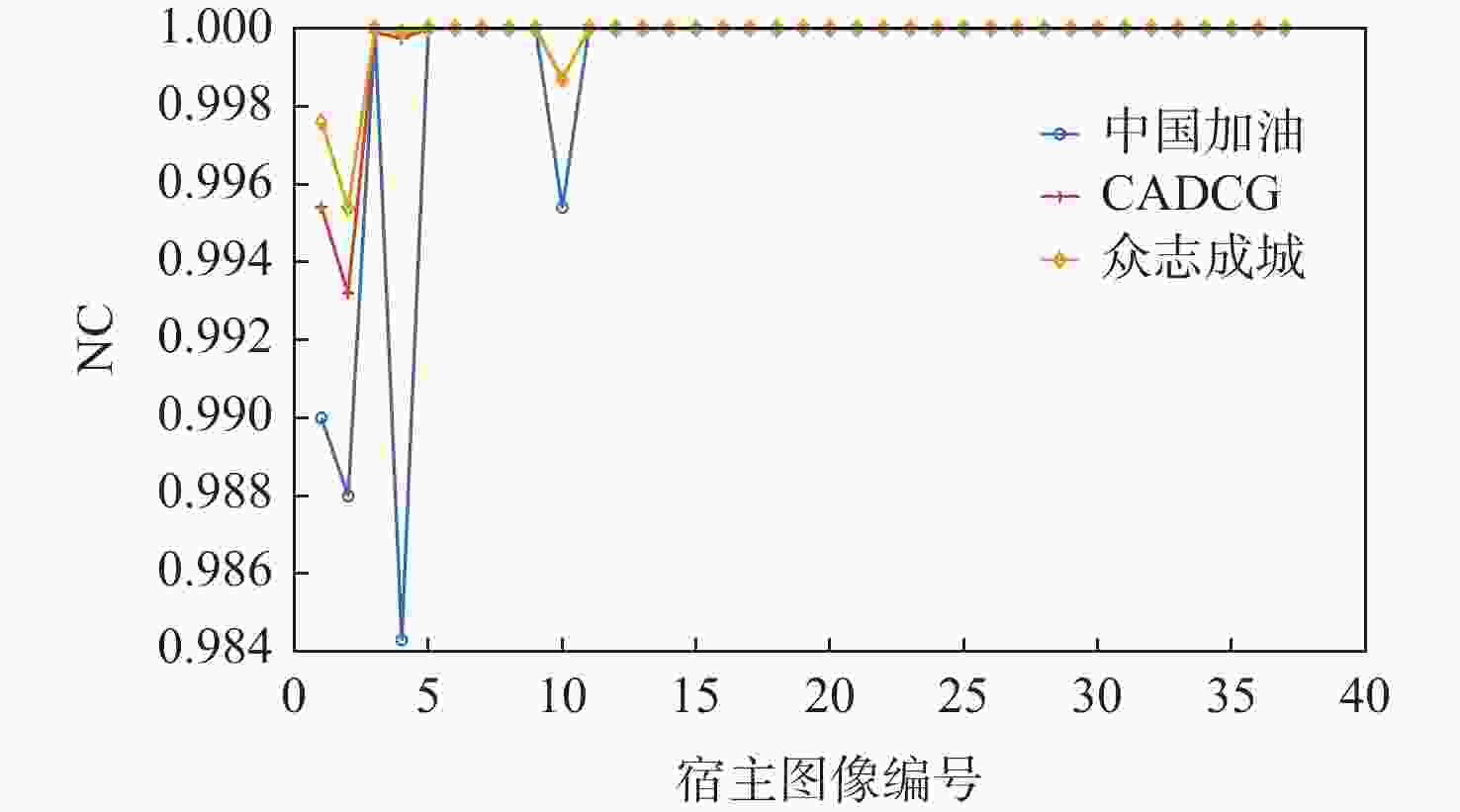
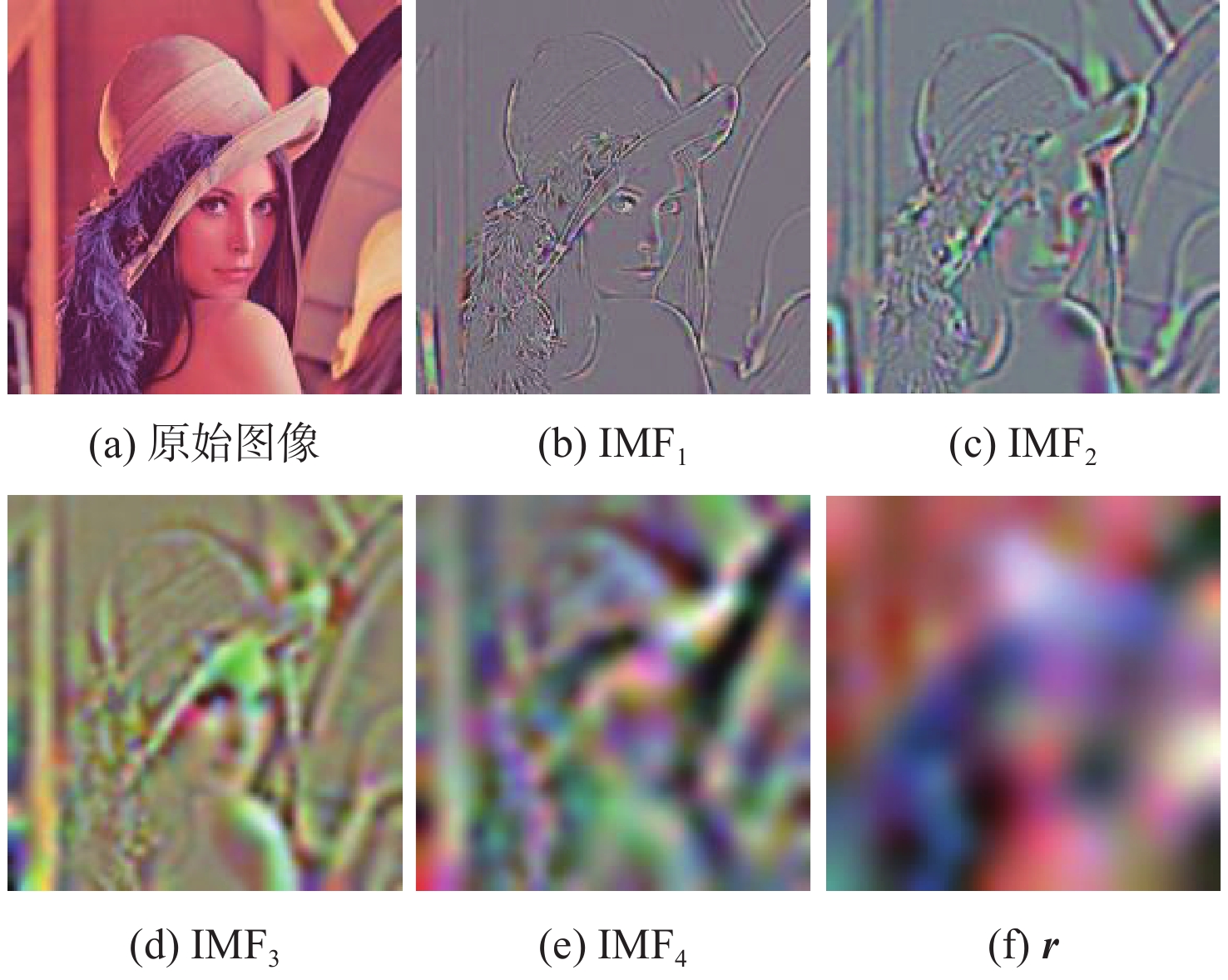
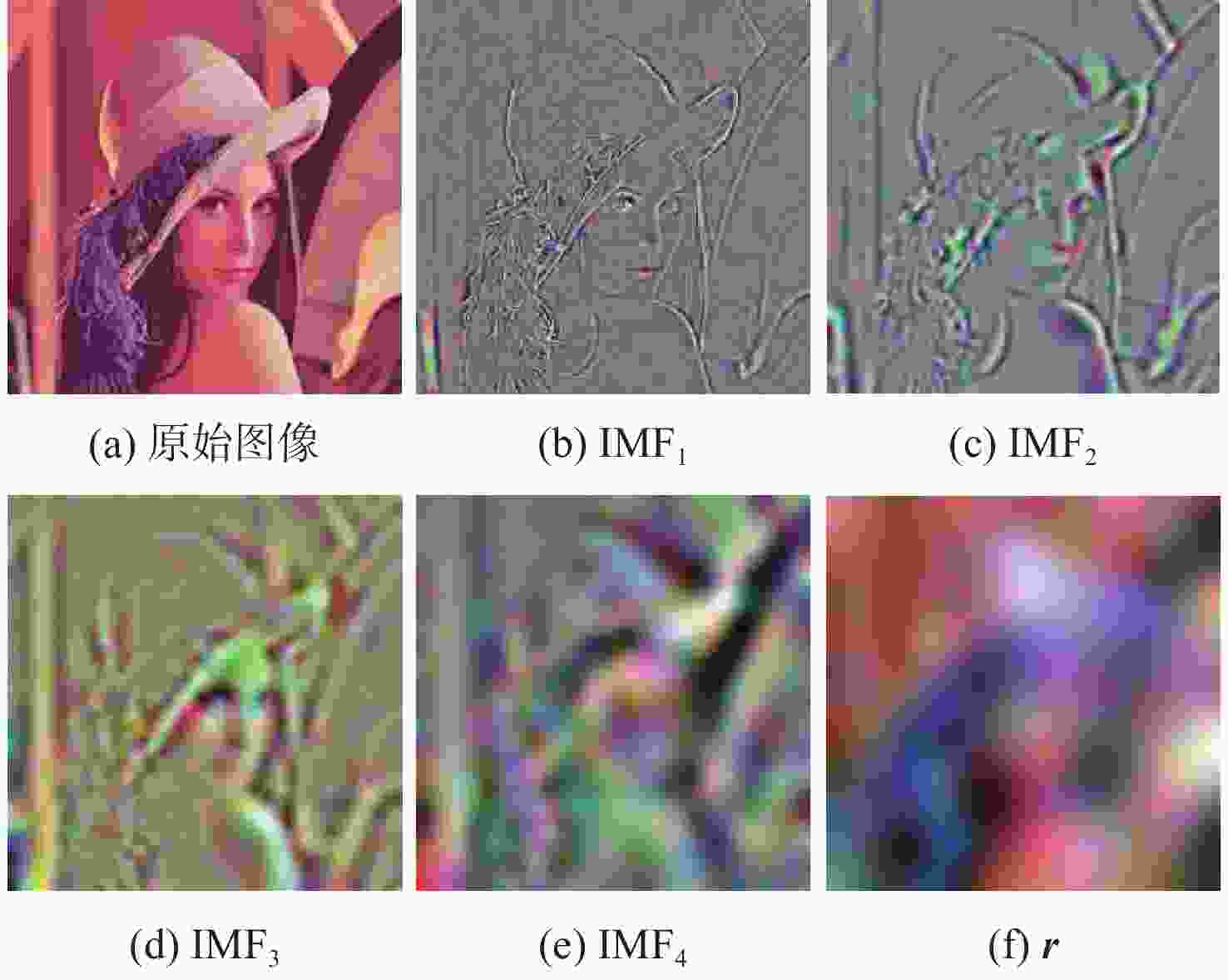
为解决现有彩色图像水印算法容错性低及宿主图像与水印图像在嵌入时尺寸匹配问题,并提高算法抵御各种攻击的鲁棒性,提出一种基于二维经验模态分解(BEMD)和离散余弦变换(DCT)的彩色图像多重水印鲁棒算法。使用Arnold变换对3幅二值水印图像进行置乱,分别对彩色宿主图像的三通道进行BEMD,得到各通道的内蕴模态函数(IMF)和余量信息,选择各通道的第1个IMF(记作IMF1)作为水印嵌入层,对每个通道的IMF1分割成不重叠子块后进行DCT;再将置乱后的二值水印图像依次重复嵌入在各通道子块经过之字形(Zigzag)扫描后的中频系数中,使用逆Zigzag扫描和逆DCT得到各通道嵌入水印信息后的IMF1,并与每个通道其余的IMF及余量重建得到嵌入水印后的彩色图像。水印提取为嵌入过程的逆过程,算法可以实现彩色图像嵌入水印的盲提取。在水印提取过程中对重复嵌入提取到的水印图像使用投票策略,增强了算法的容错性。大量实验结果表明:嵌入水印后的图像峰值信噪比(PSNR)在34 dB以上,水印信息具有较高的不可见性;对嵌入多重水印后的宿主图像进行大尺寸剪切、椒盐噪声等攻击实验,提取到的水印图像与原始图像的归一化系数均在0.96以上,且可达到1,水印信息提取完整清晰可辨。与现有大量彩色图像水印算法相比,所提算法具有较强抵御各种攻击的能力,同时嵌入水印后图像具有较高的不可见性。
Abstract:In order to solve the problem that the color image watermarking algorithm has low algorithm fault tolerance, and the size matching problem between the host image and the watermark image during embedding, and to improve the robustness of the algorithm in attack resistance, this paper proposes a robust multiple water-marking algorithm for color images based on bi-dimensional empirical mode decomposition (BEMD) and discrete cosine transform (DCT). Firstly, Arnold transform is used to scramble three binary watermark images. Then, the RGB channels of the color host image are then decomposed using BEMD in addition to derive the intrinsic modal functions (IMFs) and residues for each channel. The first IMF of each channel is selected as the watermark embedding layer and recorded as IMF1. After that, each channel is divided into non-overlapping sub-blocks, and DCT is performed on each sub-blocks. Finally, the scrambled binary watermark image is repeatedly embedded in the middle bands coefficients of each channel sub-block after a Zigzag scan, and the inverse Zigzag scan and inverse DCT are adopted to obtain the IMF1 after embedding watermark information in each channel, and then the remaining intrinsic modal functions and residues of each channel are used to reconstruct the color image after the watermark embedding. The watermark extraction is the inverse of the watermark embedding process. The algorithm in this paper can implement blind extraction of embedded watermarks. In the process of watermark extraction, the voting strategy is used to extract the repeatedly embedded watermarks, which enhances the fault tolerance of the algorithm. A large number of experimental results show that the peak signal-to-noise ratio (PSNR) of the host images is above 34 dB after several watermarks have been embedded on various sets of host photos, according to a vast number of experimental results, and the watermark images have a high degree of invisibility. The host images after embedding can be against various attacks such as large-scale cropping, salt and pepper noise, etc. The values of the extracted watermark images are all above 0.96, and some can reach 1, watermark images can be completely extracted and precisely recognized. Compared with a large number of existing color image watermarking algorithms, the color image watermarking algorithm proposed in this paper has a strong ability to resist various attacks, and the images after embedding watermarks have higher invisibility.
-
表 1 本文算法与彩色图像水印算法[6 , 28]在不同攻击下的NC值对比
Table 1. Comparison with color image watermarking algorithm[6 , 28] under different attacks NC values
攻击类型 攻击强度 Lena图像NC值
(文献[6])Lena图像NC值
(文献[28])Lena图像NC值
(所提算法)Baboon图像NC值
(所提算法)Airplane图像NC值
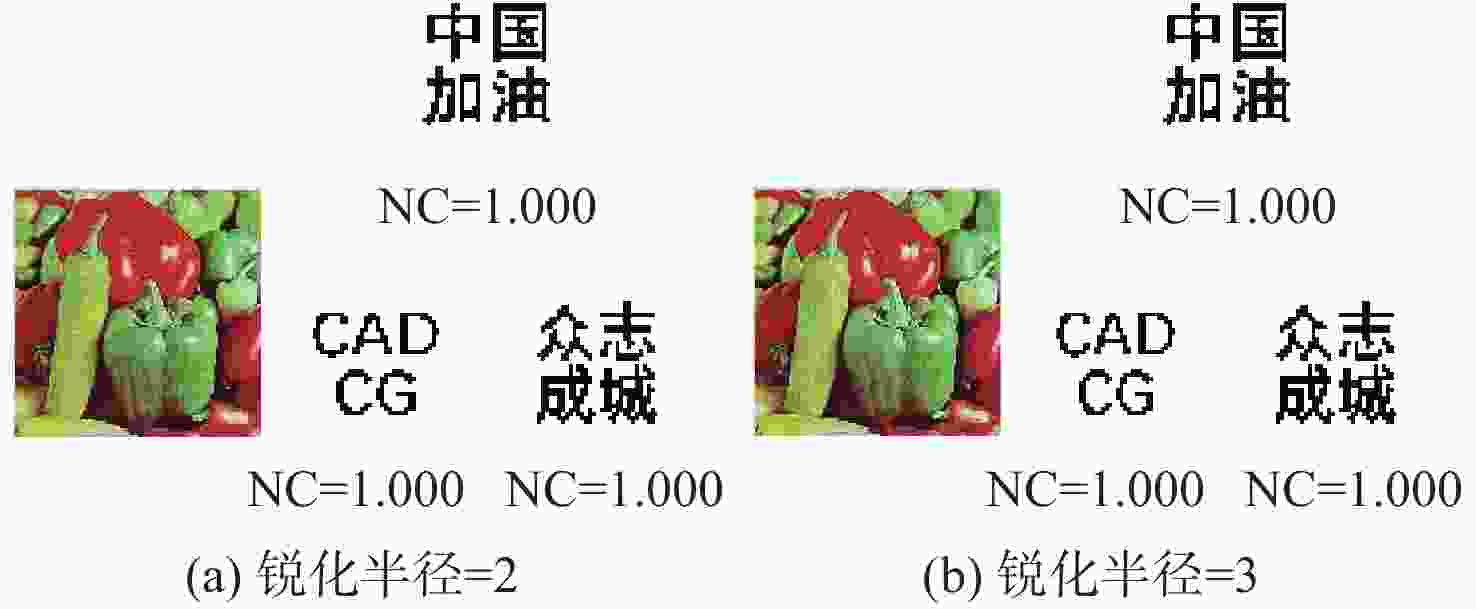
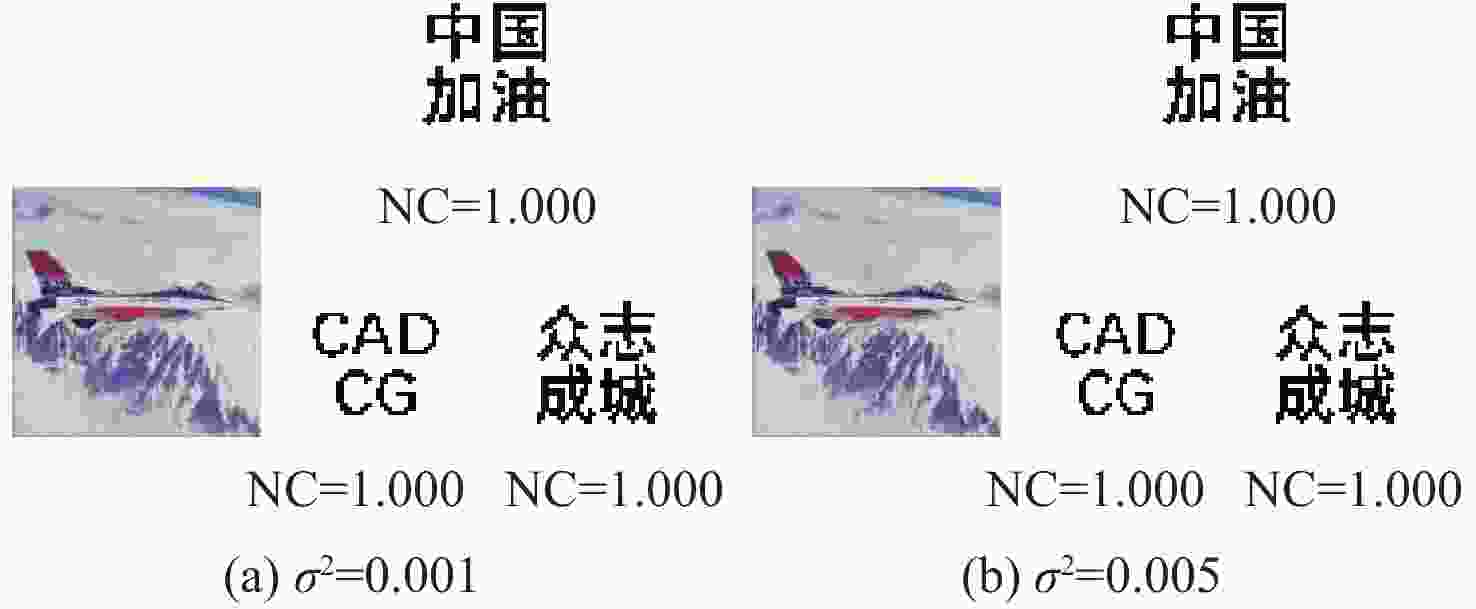
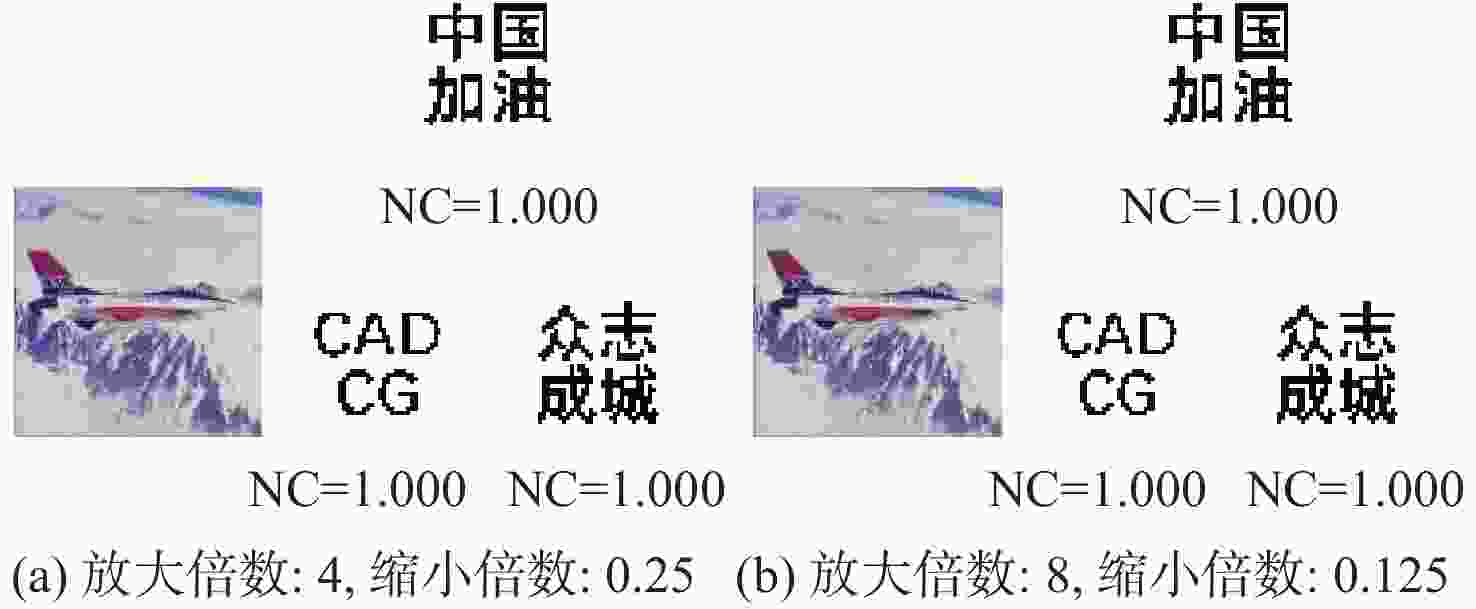
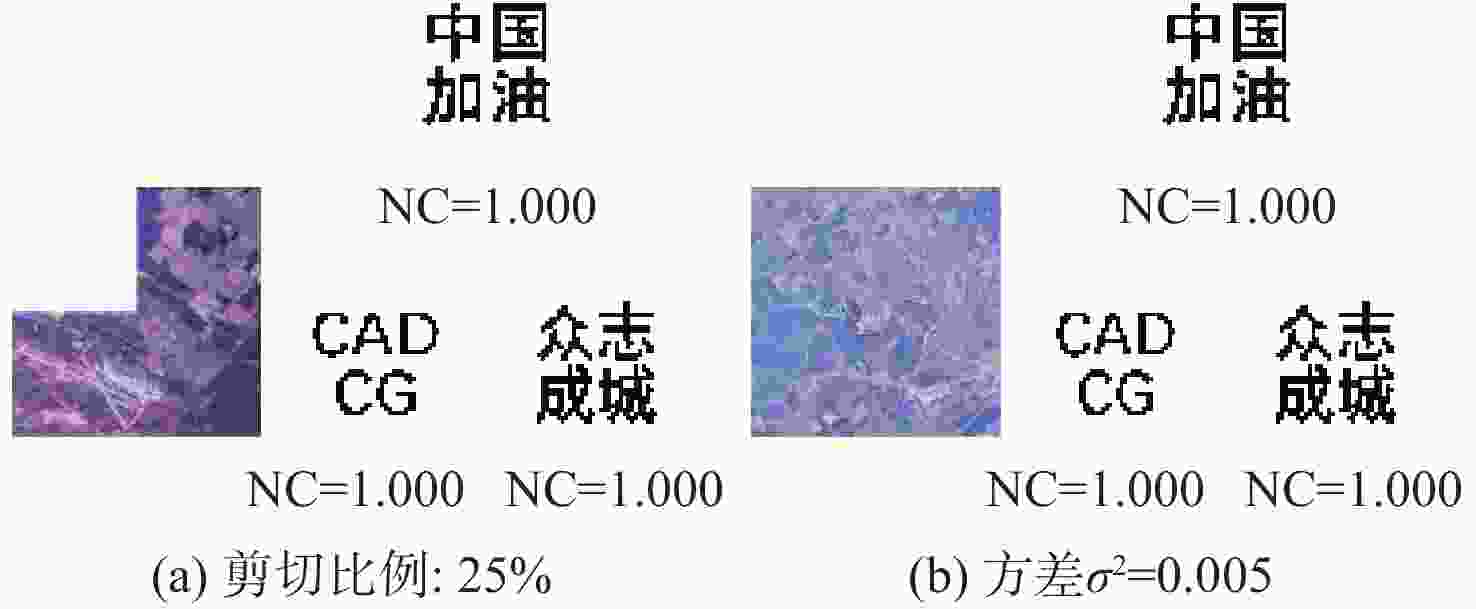
(所提算法)水印1 水印2 水印1 水印1 水印2 水印3 水印1 水印2 水印3 水印1 水印2 水印3 剪切攻击 25% 0.992 1.000 0.873 1.000 1.000 1.000 1.000 1.000 1.000 1.000 1.000 1.000 高斯低通滤波 [2,2] 0.938 0.972 0.855 1.000 1.000 0.999 0.983 0.980 0.971 1.000 1.000 1.000 中值滤波 [3,3] 0.995 0.997 0.410 0.948 0.962 0.907 0.860 0.907 0.856 0.936 0.956 0.921 图像锐化 R=2 0.998 1.000 0.990 1.000 1.000 1.000 1.000 1.000 1.000 1.000 1.000 1.000 椒盐噪声 3% 0.897 0.951 0.984 1.000 1.000 1.000 1.000 0.998 0.999 1.000 1.000 1.000 高斯噪声 0.005 0.912 0.926 0.765 1.000 1.000 1.000 0.996 0.998 0.995 0.998 1.000 1.000 JPEG压缩 Q=60 1.000 1.000 0.906 1.000 1.000 1.000 1.000 0.999 1.000 1.000 1.000 1.000 图像缩放 0.25~4 0.990 0.995 0.938 1.000 1.000 1.000 1.000 0.999 1.000 1.000 1.000 1.000 表 2 本文算法与彩色图像水印算法[7-10]在不同宿主图像下进行不同攻击的NC值对比
Table 2. Comparison with color image watermarking algorithms[7-10] for different attacks NC values under different host images
攻击类型 攻击强度 Lena图像NC值 文献[7] 文献[8] 文献[9] 文献[10] 本文所提算法 水印1 水印2 水印3 JPEG压缩 30 0.758 3 0.93~0.94 0.91~0.92 0.905 1 0.847 1 0.939 6 0.875 9 JPEG压缩 90 0.958 6 1.000 0 1.000 0 0.995 9 1.000 0 1.000 0 1.000 0 椒盐噪声 0.02 0.998 0.96~0.97 0.99~1 0.991 1 1.000 0 1.000 0 1.000 0 椒盐噪声 0.1 0.991 7 0.94~0.95 0.97~0.98 0.960 7 0.993 8 0.998 1 0.997 6 高斯噪声 0.1 0.874 3 1.000 0 0.73~0.75 0.940 6 1.000 0 1.000 0 1.000 0 高斯噪声 0.6 0.790 5 0.95~0.96 0.55~0.56 0.828 3 1.000 0 1.000 0 1.000 0 缩放 4~0.25 0.999 8 0.79~0.80 0.67~0.68 0.870 2 1.000 0 1.000 0 1.000 0 剪切 25% 0.889 5 0.73~0.75 0.8~0.81 0.772 5 1.000 0 1.000 0 1.000 0 剪切 50% 0.833 5 0.600 0 0.52~0.53 0.514 1 1.000 0 1.000 0 1.000 0 攻击类型 攻击强度 Airplane图像NC值 文献[7] 文献[8] 文献[9] 文献[10] 本文所提算法 水印1 水印2 水印3 JPEG压缩 30 0.778 8 0.94~0.95 0.90~0.91 0.920 4 0.853 4 0.931 4 0.842 8 JPEG压缩 90 0.967 5 1.000 1.000 0.998 6 1.000 0 1.000 0 1.000 0 椒盐噪声 0.02 0.999 0.94~0.95 0.99~1 0.995 8 1.000 0 1.000 0 1.000 0 椒盐噪声 0.1 0.987 5 0.92~0.93 0.98~0.99 0.978 7 0.997 6 0.998 1 0.995 3 高斯噪声 0.1 0.888 2 1.000 0 0.78~0.79 0.957 7 1.000 0 1.000 0 1.000 0 高斯噪声 0.6 0.592 8 0.92~0.93 0.57~0.58 0.855 0 1.000 0 1.000 0 1.000 0 缩放 4~0.25 0.926 5 0.78~0.79 0.69~0.70 0.877 3 1.000 0 1.000 0 1.000 0 剪切 25% 0.889 5 0.74~0.76 0.8~0.81 0.772 5 1.000 0 1.000 0 1.000 0 剪切 50% 0.833 5 0.600 0 0.52~0.53 0.514 1 1.000 0 1.000 0 1.000 0 -
[1] ATTAULLAH, SHAH T, JAMAL S S. An improved chaotic cryptosystem for image encryption and digital watermarking[J]. Wireless Personal Communications, 2020, 110(3): 1429-1442. doi: 10.1007/s11277-019-06793-1 [2] THANKI R, DWIVEDI V, BORISAGAR K. A hybrid watermarking scheme with CS theory for security of multimedia data[J]. Journal of King Saud University-Computer and Information Sciences, 2019, 31(4): 436-451. doi: 10.1016/j.jksuci.2017.05.005 [3] KARAJEH H, KHATIB T, RAJAB L, et al. A robust digital audio watermarking scheme based on DWT and Schur decomposition[J]. Multimedia Tools and Applications, 2019, 78(13): 18395-18418. doi: 10.1007/s11042-019-7214-3 [4] LAKRISSI Y, SAAIDI A, ESSAHLAOUI A. Novel dynamic color image watermarking based on DWT-SVD and the human visual system[J]. Multimedia Tools and Applications, 2018, 77(11): 13531-13555. doi: 10.1007/s11042-017-4974-5 [5] ABDULRAHMAN A K, OZTURK S. A novel hybrid DCT and DWT based robust watermarking algorithm for color images[J]. Multimedia Tools and Applications, 2019, 78(12): 17027-17049. doi: 10.1007/s11042-018-7085-z [6] ROY S, PAL A K. A blind DCT based color watermarking algorithm for embedding multiple watermarks[J]. AEU-International Journal of Electronics and Communications, 2017, 72: 149-161. [7] SU Q T, LIU Y H, LIU D C, et al. A new watermarking scheme for colour image using QR decomposition and ternary coding[J]. Multimedia Tools and Applications, 2019, 78(7): 8113-8132. doi: 10.1007/s11042-018-6632-y [8] SU Q T, YUAN Z H, LIU D C. An approximate schur decomposition-based spatial domain color image watermarking method[J]. IEEE Access, 2019, 7: 4358-4370. doi: 10.1109/ACCESS.2018.2888857 [9] LIU D C, YUAN Z H, SU Q T. A blind color image watermarking scheme with variable steps based on Schur decomposition[J]. Multimedia Tools and Applications, 2020, 79(11-12): 7491-7513. doi: 10.1007/s11042-019-08423-1 [10] SU Q T, ZHANG X F, WANG G. An improved watermarking algorithm for color image using Schur decomposition[J]. Soft Computing, 2020, 24(1): 445-460. doi: 10.1007/s00500-019-03924-5 [11] HUANG N E, SHEN Z, LONG S R, et al. The empirical mode decomposition and the Hilbert spectrum for nonlinear and non-stationary time series analysis[J]. Proceedings of the Royal Society of London Series A:Mathematical, Physical and Engineering Sciences, 1998, 454(1971): 903-995. doi: 10.1098/rspa.1998.0193 [12] 李翠芸, 曹潇男, 姬红兵, 等. 基于偏微分方程的快速二维经验模态分解方法及其应用[J]. 计算机辅助设计与图形学学报, 2014, 26(7): 1143-1150.LI C Y, CAO X N, JI H B, et al. A fast bidimensional empirical mode decomposition based on partial differential equation and its application on image processing[J]. Journal of Computer-Aided Design & Computer Graphics, 2014, 26(7): 1143-1150(in Chinese). [13] DING S F, DU P, ZHAO X Y, et al. BEMD image fusion based on PCNN and compressed sensing[J]. Soft Computing, 2019, 23(20): 10045-10054. doi: 10.1007/s00500-018-3560-8 [14] CHEN Y Q, ZHANG L N, ZHAO B B. Identification of the anomaly component using BEMD combined with PCA from element concentrations in the Tengchong tin belt, SW China[J]. Geoscience Frontiers, 2019, 10(4): 1561-1576. doi: 10.1016/j.gsf.2018.09.015 [15] AN F P, LIU Z W. Bi-dimensional empirical mode decomposition (BEMD) algorithm based on particle swarm optimization-fractal interpolation[J]. Multimedia Tools and Applications, 2019, 78(12): 17239-17264. doi: 10.1007/s11042-018-7097-8 [16] MA X M, ZHOU X W, AN F P. Bi-dimensional empirical mode decomposition (BEMD) and the stopping criterion based on the number and change of extreme points[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 11(2): 623-633. doi: 10.1007/s12652-018-0955-4 [17] NUNES J C, BOUAOUNE Y, DELECHELLE E, et al. Image analysis by bidimensional empirical mode decomposition[J]. Image and Vision Computing, 2003, 21(12): 1019-1026. doi: 10.1016/S0262-8856(03)00094-5 [18] REN G H, HAN J N, FU J H, et al. Asymmetric multiple-image interference cryptosystem using discrete cosine transform and conditional decomposition[J]. Optical Review, 2020, 27(1): 1-8. doi: 10.1007/s10043-019-00552-0 [19] MOGHADDASI Z, JALAB H A, NOOR R M. Image splicing forgery detection based on low-dimensional singular value decomposition of discrete cosine transform coefficients[J]. Neural Computing and Applications, 2019, 31(11): 7867-7877. doi: 10.1007/s00521-018-3586-y [20] ZHANG L N, WEI D Y. Dual DCT-DWT-SVD digital watermarking algorithm based on particle swarm optimization[J]. Multimedia Tools and Applications, 2019, 78(19): 28003-28023. doi: 10.1007/s11042-019-07902-9 [21] ABBAS N A. Image encryption based on independent component analysis and arnold’s cat map[J]. Egyptian Informatics Journal, 2016, 17(1): 139-146. doi: 10.1016/j.eij.2015.10.001 [22] LI X S, LI T Y, WU J, et al. Joint image compression and encryption based on sparse Bayesian learning and bit-level 3D Arnold cat maps[J]. PLoS One, 2019, 14(11): 0224382. doi: 10.1371/journal.pone.0224382 [23] XIE J H, WU D L, WANG J, et al. The analysis of additive noise of thermal test low-frequency cable fault detection based on M sequence correlation algorithm[J]. Cluster Computing, 2019, 22(4): 9303-9312. [24] 王小超, 胡坤, 胡建平. 结合BEMD与Hilbert曲线的重复嵌入图像水印算法[J]. 计算机辅助设计与图形学学报, 2020, 32(2): 287-296.WANG X C, HU K, HU J P. Repeated embedding algorithm for image watermarking based on BEMD and Hilbert curve[J]. Journal of Computer-Aided Design & Computer Graphics, 2020, 32(2): 287-296(in Chinese). [25] WANG X C, HU K, HU J P, et al. Robust and blind image watermarking via circular embeddingand bidimensional empirical mode decomposition[J]. The Visual Computer, 2020, 36(10-12): 2201-2214. doi: 10.1007/s00371-020-01909-2 [26] HONG D, CHO H, LEE S, et al. Volumetric image reconstruction in a dental panoramic imaging system with a limited-angle zigzag scan geometry[J]. Journal of the Korean Physical Society, 2013, 62(2): 333-338. doi: 10.3938/jkps.62.333 [27] HUYNH-THU Q, GHANBARI M. Scope of validity of PSNR in image/video quality assessment[J]. Electronics Letters, 2008, 44(13): 800. doi: 10.1049/el:20080522 [28] SU Q T, WANG G, JIA S L, et al. Embedding color image watermark in color image based on two-level DCT[J]. Signal, Image and Video Processing, 2015, 9(5): 991-1007. doi: 10.1007/s11760-013-0534-2 -






 下载:
下载: