A satellite anomaly detection method based on distance correlation coefficient and GPR model
-
摘要:
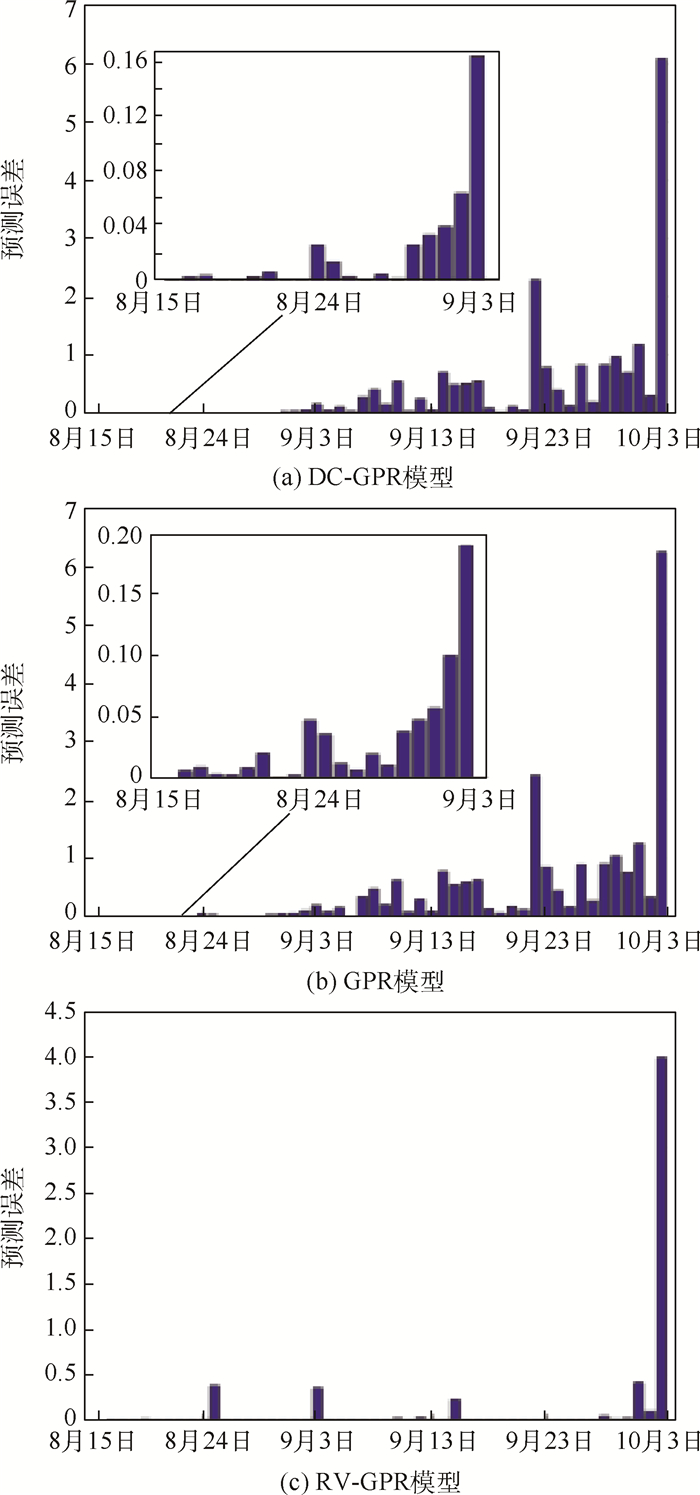
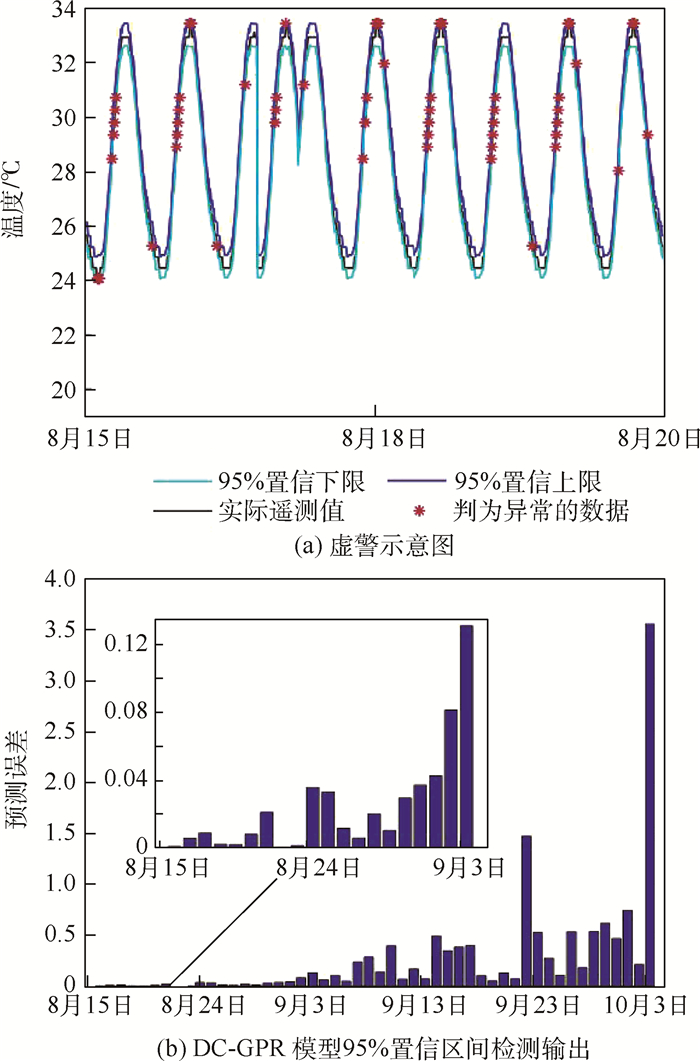
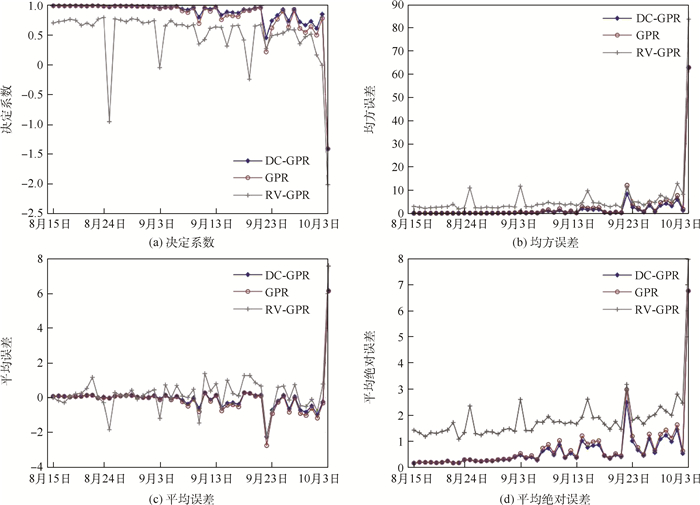
卫星在轨运行期间,遥测数据表现形式通常为多维时间序列。高斯过程回归(GPR)模型可以为重要的遥测参数提供动态门限,及时发现隐藏在工程阈值内的故障征兆,但是高维卫星数据使得GPR模型具有局限性。因此,为获取与多个遥测参数相关的动态门限,在GPR模型的基础上,融合距离相关系数对预测变量进行选择,减少信息冗余和计算量,提高模型的可解释性,并估计模型的泛化误差以设置更合理的预测区间,提高模型的泛化能力,检测数据流的持续异常。对实际在轨卫星数据进行仿真实验,验证了距离相关系数融合GPR模型的卫星异常检测方法可以在卫星故障早期检测到数据异常,而且提高了模型的预测性能,降低了虚警率。
-
关键词:
- 卫星异常检测 /
- 高斯过程回归(GPR) /
- 距离相关系数 /
- 变量选择 /
- 泛化误差
Abstract:During the orbital operation of the satellite, the telemetry data is usually represented by multidimensional time series. The Gaussian Process Regression (GPR) model can provide dynamic thresholds for important telemetry parameters and timely discover failure symptoms hidden within the engineering threshold. However, high dimensional satellite data makes GPR model limited. Therefore, in order to obtain the dynamic threshold related to multiple telemetry parameters, based on the GPR model, the distance correlation coefficient is combined to select predictive variables, reduce the information redundancy and the amount of calculation, and improve the interpretability of the model.The generalization error of the model is estimated to set a more reasonable prediction interval, to improve the generalization ability and detect the continuous abnormality of the data stream. Simulation experiments on actual orbiting satellite data verify that this method can detect data anomalies in the early failure of the satellite, improve the prediction performance of the model and reduce the false alarm rate.
-
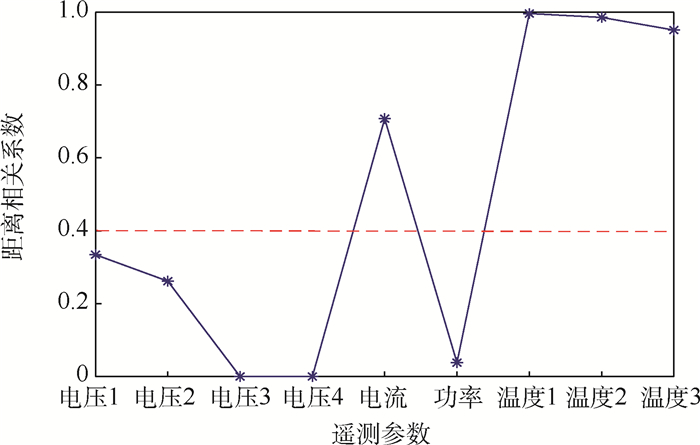
表 1 相关程度度量
Table 1. Relevance measure
相关性 距离相关系数 极强相关 0.8~1.0 强相关 0.6~0.8 中相关 0.4~0.6 弱相关 0.2~0.4 极弱或无相关 0~0.2 表 2 不同模型的检测评估
Table 2. Detection evaluation of different models
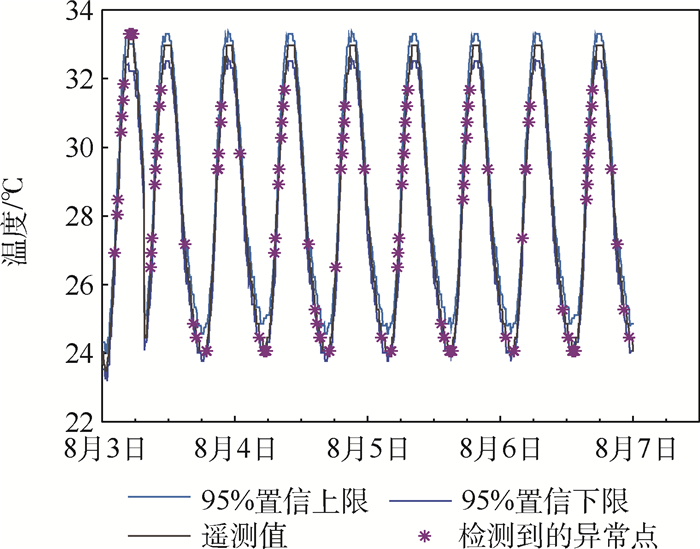
模型 DR/% FA/% MA/% DC-GPR 86.67 5.41 0 DC-GPR(95%置信区间) 52.94 19.51 0 GPR 60 14.63 0 RV-GPR 86.67 11.76 57.14 -
[1] BELCASTRO C M.Aviation safety program: Integrated vehicle health management technical plan summary[R].Washington, D.C.: NASA Technology Report, 2006. [2] 彭喜元, 庞景月, 彭宇, 等. 航天器遥测数据异常检测综述[J]. 仪器仪表学报, 2016, 37(9): 1929-1945. doi: 10.3969/j.issn.0254-3087.2016.09.003PENG X Y, PANG J Y, PENG Y, et al. Review on anomaly detection of spacecraft telemetry data[J]. Chinese Journal of Scientific Instrument, 2016, 37(9): 1929-1945(in Chinese). doi: 10.3969/j.issn.0254-3087.2016.09.003 [3] CHANDOLA V, BANERJEE A, KUMAR V.Anomaly detection: A survey[J]. ACM Computing Surveys, 2009, 41(3): 1-58. [4] 张克明, 蔡远文, 任元. 基于生成对抗网络的航天异常事件检测方法[J]. 北京航空航天大学学报, 2019, 45(7): 1329-1336. doi: 10.13700/j.bh.1001-5965.2018.0682ZHANG K M, CAI Y W, REN Y.Space anomaly events detection approach based on generative adversarial nets[J]. Journal of Beijing University of Aeronautics and Astronautics, 2019, 45(7): 1329-1336(in Chinese). doi: 10.13700/j.bh.1001-5965.2018.0682 [5] 吕军晖, 周刚, 金毅. 一种基于时间序列的自适应网络异常检测算法[J]. 北京航空航天大学学报, 2009, 35(5): 636-639. https://bhxb.buaa.edu.cn/CN/Y2009/V35/I5/636LÜ J H, ZHOU G, JIN Y.Adaptive aberrant network traffic detection algorithm based on time series forecast[J]. Journal of Beijing University of Aeronautics and Astronautics, 2009, 35(5): 636-639(in Chinese). https://bhxb.buaa.edu.cn/CN/Y2009/V35/I5/636 [6] 张妮, 车立志, 吴小进. 基于数据驱动的故障诊断技术研究现状及展望[J]. 计算机科学, 2017, 44(6A): 37-42. doi: 10.11896/j.issn.1002-137X.2017.6A.008ZHANG N, CHE L Z, WU X J.Present situation and prospect of data-driven based fault diagnosis technique[J]. Computer Science, 2017, 44(6A): 37-42(in Chinese). doi: 10.11896/j.issn.1002-137X.2017.6A.008 [7] 彭宇, 刘大同. 数据驱动故障预测和健康管理综述[J]. 仪器仪表学报, 2014, 35(3): 481-495.PENG Y, LIU D T.Data-driven prognostics and health management: A review of recent advances[J]. Chinese Journal of Scientific Instrument, 2014, 35(3): 481-495(in Chinese). [8] AZEVEDO D R, AMBROSIO A M, VIEIRA M, et al.Applyingdata mining for detecting anomalies in satellites[C]//European Dependable Computing Conference, 2012: 212-217. [9] HAWKINS S, HE H, WILLIAMS G J, et al.Outlier detection using replicator neural networks[C]//International Conference on Data Warehousing and Knowledge Discovery.Berlin: Springer, 2002: 170-180. [10] WILLIAMS G, BAXTER R, HE H, et al.A comparative study of RNN for outlier detection in data mining[C]//IEEE International Conference on Data Mining.Piscataway: IEEE Press, 2002: 709-712. [11] SCHOLKOPF B, PLATT J C, SHAWE T J, et al. Estimating the support of a high-dimensional distribution[J]. Neural Computation, 2014, 13(7): 1443-1471. [12] DAS K, BHADURI K, VOTAVA P, et al. Distributed anomaly detection using 1-class SVM for vertically partitioned data[J]. Statistical Analysis and Data Mining, 2011, 4(4): 393-406. doi: 10.1002/sam.10125 [13] ANAISSI A, KHO N L, WANG Y, et al. Automated parameter tuning in one-class support vector machine: An application for damage detection[J]. Journal of Data Science, 2018, 6(4): 311-325. doi: 10.1007/s41060-018-0151-9 [14] ESTER M.A density-based algorithm for discovering clusters in large spatial databases with noise[C]//Proceedings of the Second International Conference on Knowledge Discovery and Data Mining, 1996: 226-231. [15] RAMASWAMY S, RASTOGI R, SHIM K, et al. Efficient algorithms for mining outliers from large data sets[J]. International Conference on Management of Data, 2000, 29(2): 427-438. [16] YIN C, ZHANG S, YIN Z, et al. Anomaly detection model based on data stream clustering[J]. Cluster Computing, 2019, 22(1): 1729-1738. doi: 10.1007/s10586-017-1066-2 [17] ALGULIYEV R M, ALIGULIYEV R M, SUKHOSTAT L, et al. Anomaly detection in big data based on clustering[J]. Statistics, Optimizationand Information Computing, 2017, 5(4): 325-340. [18] QIU H, EKLUND N H, HU X, et al.Anomaly detection using data clustering and neural networks[C]//International Joint Conference on Neural Network, 2008: 3627-3633. [19] AGGARWAL C C, YU P S.Outlier detection with uncertain data[C]//SIAM International Conference on Data Mining, 2008: 483-493. [20] THATTE G, MITRA U, HEIDEMANN J, et al. Parametric methods for anomaly detection in aggregate traffic[J]. IEEE ACM Transactions on Networking, 2011, 19(2): 512-525. doi: 10.1109/TNET.2010.2070845 [21] PATCHA A, PARK J.An overview of anomaly detection techniques: Existing solutions and latest technological trends[J]. Computer Networks, 2007, 51(12): 3448-3470. doi: 10.1016/j.comnet.2007.02.001 [22] PAN D W, LIU D T, ZHOU J, et al. Anomaly detection for satellite power subsystem with associated rules based on kernel principal component analysis[J]. Microelectronics Reliability, 2015, 55(9): 2082-2086. [23] COHEN G, HILARIO M, PELLEGRINI C, et al. One-class support vector machines with a conformal kernel. A case study in handling class imbalance[J]. Lecture Notes in Computer Science, 2004, 3138: 850-858. doi: 10.1007/978-3-540-27868-9_93 [24] TARIQ S, LEE S, SHIN Y, et al.Detecting anomalies in space using multivariate convolutional LSTM with mixtures of probabilistic PCA[C]//Knowledge Discovery and Data Mining, 2019: 2123-2133. [25] DONG D.Mine gas emission prediction based on Gaussian process model[J]. Procedia Engineering, 2012, 45: 334-338. doi: 10.1016/j.proeng.2012.08.167 [26] ANOGARAN G, LOPEZ D.A Gaussian process based big data processing framework in cluster computing environment[J]. Cluster Computing, 2018, 21(1): 189-204. doi: 10.1007/s10586-017-0982-5 [27] SZEKELY G J, RIZZO M L, BAKIROV N K, et al. Measuring and testing dependence by correlation of distances[J]. Annals of Statistics, 2007, 35(6): 2769-2794. [28] 葛芳君, 赵磊, 刘俊, 等. 基于Pearson相关系数的老年人社会支持与心理健康相关性研究的Meta分析[J]. 中国循证医学杂志, 2012, 12(11): 1320-1329. doi: 10.7507/1672-2531.20120207GE F J, ZHAO L, LIU J, et al. Correlation between social support andmental health of the aged based on Pearson correlation coefficient: A meta-analysis[J]. Chinese Journal of Evidence-Based Medicine, 2012, 12(11): 1320-1329(in Chinese). doi: 10.7507/1672-2531.20120207 [29] 张建勇, 高冉, 胡骏, 等. 灰色关联度和Pearson相关系数的应用比较[J]. 赤峰学院学报(自然科学版), 2014, 30(11): 1-2. doi: 10.3969/j.issn.1673-260X.2014.11.001ZHANG J Y, GAO R, HU J, et al. Application comparison of gray correlation degree and Pearson correlation coefficient[J]. Journal of Chifeng University(Natural Science Edition), 2014, 30(11): 1-2(in Chinese). doi: 10.3969/j.issn.1673-260X.2014.11.001 [30] NADEAU C, BENGIO Y.Inference for the generalization error[J]. Neural Information Processing Systems, 1999, 52(3): 307-313. [31] PANG J Y, LIU D T, PENG Y, et al. Anomaly detection based on uncertainty fusion for univariate monitoring series[J]. Measurement, 2017, 95: 280-292. doi: 10.1016/j.measurement.2016.10.031 期刊类型引用(1)
1. 马鸣宇,董朝阳,王青,周敏. 基于时变增益ESO的多航天器SO(3)姿态协同控制. 北京航空航天大学学报. 2018(09): 1797-1807 .  本站查看
本站查看其他类型引用(0)
-







 下载:
下载: