UAV network intrusion detection method based on spatio-temporal graph convolutional network
-
摘要:
无人机网络相比地面网络具有节点快速移动、拓扑结构变换频繁和通信链路不可靠的特点,传统的针对地面网络的入侵检测方法难以适用。针对无人机网络的时空动态特性进行建模,提出了一种无人机网络的入侵检测方法——基于注意力机制的时空图卷积网络(ATGCN)。将图卷积网络和门控递归单元组合为时空图卷积网络,从复杂多变的数据中提取网络的时空演变特征,通过注意力机制提取和入侵检测最相关的特征,输入支持向量机进行分类预测。多个数据集的实验分析表明:所提方法能够适应无人机网络的动态性和不稳定性,相比传统检测方法准确率高且误报率低,具有良好的鲁棒性和适应性。
Abstract:Compared with ground networks, UAV networks have the characteristics of fast moving nodes, frequent topology changes, and unreliable communication links. Traditional intrusion detection methods are difficult to apply. Aimed at the spatio-temporal dynamic characteristics of UAV networks, an intrusion detection method:Attention-based Spatio-Temporal Graph Convolutional Network (ATGCN) is proposed, which combines graph convolutional network and gated recursive unit into spatio-temporal graph convolutional network. The spatio-temporal graph convolutional network extracts the spatio-temporal evolution characteristics of the network from complex and changeable data, attention mechanism is used to extract the features most relevant to intrusion detection, and the support vector machine is used as the last layer of the model for classification to identify network attacks. The experimental analysis of multiple datasets shows that the proposed method can adapt to the dynamics and instability of UAV networks, has higher accuracy and lower false positive rate than traditional detection methods, and has good robustness and adaptability.
-
近年来,无人机在军事和民用领域的网络化应用日益广泛。无人机网络多部署和应用于恶劣、无人值守的环境中,更易遭受各种网络攻击,如虫洞攻击、拒绝服务攻击和泛洪攻击等[1]。网络入侵检测技术作为一种主动网络防御技术,通过监视网络运行状态,能够识别并有效应对各种网络攻击行为,确保网络可靠运行[2]。
传统的网络入侵检测方法包括基于签名的检测和基于异常的检测。基于签名的检测方法对已知入侵行为建立知识库,通过与知识库的记录对比来确认攻击,是检测常见网络攻击的有效方法,但不适用于检测未知的新型攻击。基于异常的检测方法通过网络流量的正常行为特征建立入侵检测模型[3],将与正常行为有较大偏差的异常活动判定为网络攻击,因而无需具体定义每种入侵行为,能够有效检测未知攻击且适应网络的变化。入侵检测模型的构建有统计[4-5]、聚类[6-7]、分类等不同方法[8-9]。统计方法需要根据流量特征的历史数据建立统计模型,因此检测的时效性差。聚类方法通常使用K均值等聚类算法建模,但流量特征复杂时存在难以确认聚类中心的问题[10]。分类方法通常使用支持向量机(SVM)等算法构建入侵检测分类模型[9],不仅能快速检测出异常流量,还能识别具体攻击类别,但分类准确率通常取决于从网络流量中挖掘的特征(能否准确描述网络)。
由于深度学习具有从复杂多维数据中挖掘隐含数据特征的特点,近年来深度神经网络被大量应用于入侵检测分类模型的构建,效果远优于依靠人工主观设计特征参数[11-12]。文献[13]>论述了深度学习在入侵检测特征提取方面的优势,文献[14]>指出采用深度学习方法的无人机网络入侵检测准确率较传统方法明显提高。
传统的入侵检测方法多数针对拓扑固定的地面网络,研究人员更多关注网络流量的时序特征。例如,Kim等[15]将网络流量数据建模为时间序列来提高入侵检测模型性能,Wang等[16]使用卷积神经网络(CNN)和递归神经网络(RNN)来学习网络流量的时间特征用于入侵检测。基于网络拓扑结构的入侵检测研究相对较少,少有针对网络拓扑的时空特征进行整体建模。Kwon等[9]指出从网络拓扑中挖掘空间特征能进一步获得更高的检测精度。
节点的移动性及链路质量的不稳定性使无人机网络的拓扑结构动态变化,采用传统的入侵检测方法存在无法捕获网络空间动态特征的问题。针对该问题,本文使用深度学习方法提出了一种入侵检测方法——基于注意力机制的时空图卷积网络(Attention-based Spatio-Temporal Graph Convolutional Network,ATGCN),引入图数据结构来描述网络的空间特征,通过构造时空图卷积网络捕获无人机网络的时空演变特征,引入注意力机制提升模型分类效果。在多个数据集上的实验表明,ATGCN相比于其他方法具有更高的检测准确率和更低的误报率,并且在通信质量较差或噪声干扰的网络环境下,仍然具有较好的适应性。
1. 相关工作
图是对实际应用中复杂多变的通信网络的抽象描述,由网络拓扑结构特征和网络节点特征的数据信息组成,实现网络特征的直观数学表达。
图卷积网络(Graph Convolutional Network,GCN)是一种能够对图数据进行深度学习的方法,其将卷积运算从传统数据推广到了图数据,并被证明可以用于网络节点分类和入侵检测[17]。图卷积网络将拓扑结构和节点特征信息作为输入,通过堆叠多层线性单元和非线性激活函数来学习节点深层特征,其核心思想是:将节点之间的关系转换为图的邻接矩阵,通过聚合邻居结点的信息来提取空间特征。Zheng和Li[18]使用图神经网络来提取网络的拓扑结构和节点属性特征,在得到的图表示向量上运行异常检测算法,判断网络是否异常,证明了提取图的演变特征在图网络的节点分类任务上具有明显的提升效果。Hsu[19]通过图卷积网络获取空间特征,结合变分递归神经网络研究图时间序列上的异常检测问题,在传感器数据和交通流量数据的实验上证明了模型的检测能力。
受文献[20]>的影响,本文使用图卷积网络建模获取无人机网络的空间特征,结合门控递归单元(Gated Recurrent Unit,GRU)组成时空图卷积网络来挖掘深层的时空演变特征,从而更准确地描述无人机网络。
2. 问题定义
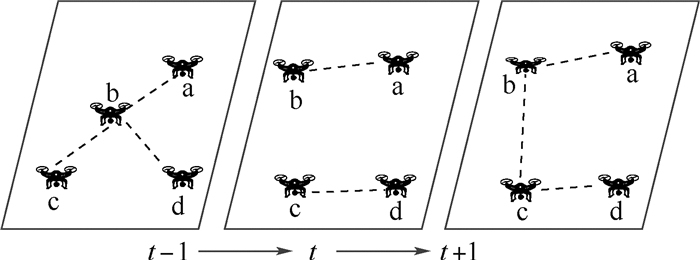
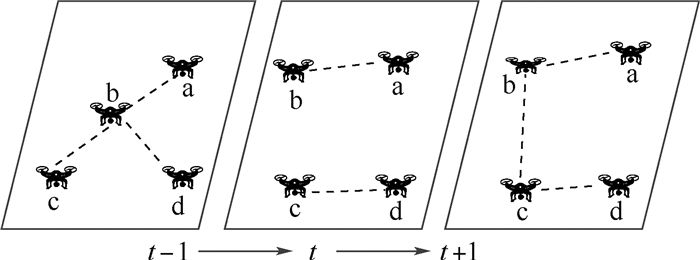
在实际场景中,无人机网络拓扑结构会随着时间的推移而变化。例如,由于通信质量或者网络攻击而导致的链路故障,因事故或人为因素而导致的无人机故障。因此,将无人机网络建模为一个随时间变化的动态图,该图由一段时间内的一系列图快照(Snapshot)组成,如图 1所示。
图的节点对应无人机网络的通信节点(无人机、传感器),一个边缘代表一条通信链路。
定义1用G描述网络的拓扑结构,动态网络可以定义为一系列图快照G={G1, G2, …, Gs},Gt={V, Et, At},V={V1, V2, …, VN}表示网络中的节点,N为节点的数量,Et为边集,邻接矩阵At用于表示节点之间的连接,At中的元素0和1分别表示节点之间是否连接。
定义2用X∈Rn×d描述特征矩阵,n表示节点数,d为每个节点的特征维度。将网络上的时间序列观测值视为网络中节点的属性特征,节点属性特征可以是任何流量的相关信息,如传输速率、接收速率、发送消息数目、接收消息数目等。
复杂的时间依赖性和动态拓扑构成了巨大的挑战。一方面,对节点的观测显示出非线性的时间动态性,如不同的时间段内网络流量的峰值变化或者黑客攻击发起的时间范围。另一方面,节点之间复杂的空间依赖性,每个节点都受到相邻节点的强烈影响。拓扑结构的演变可能导致节点上观测值的突然且剧烈的变化,如节点链路突然中断的情况下,节点接收的数据包突然下降。
本文的入侵检测目标是:充分利用一段时间内的拓扑结构信息和节点属性特征信息,挖掘节点之间隐含的时空特征信息和时空依赖性,最终用来对节点进行分类。
3. 无人机网络入侵检测模型
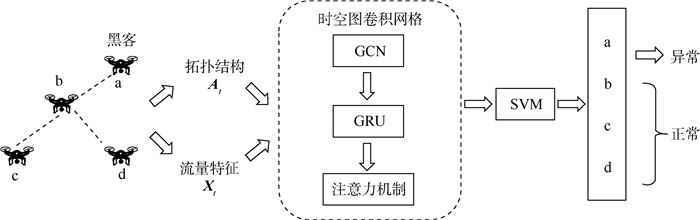
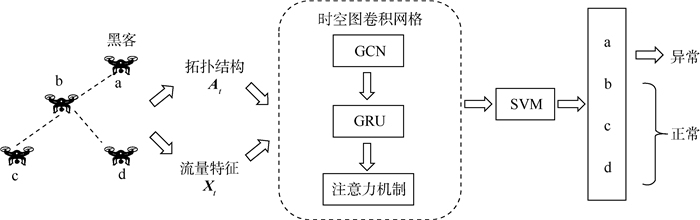
本文的网络入侵检测模型框架如图 2所示。为了建模拓扑关系和时空依赖性,将图快照中的节点相关性和节点属性特征的变化视为时间内关系。首先,通过图卷积网络对网络中节点的空间依赖性进行建模,获得空间特征;然后,将含有空间特征的历史时间序列信息输入GRU中,通过单元间的信息传递捕获时间特征,从而获得无人机网络的时空演变特征,基于注意力机制对获得的特征赋予不同的权重,提取与入侵检测最相关的特征信息;最后,输入SVM分类器得到检测结果。
3.1 基于图卷积网络的空间特征提取
考虑某个时间上的空间图,图的拓扑结构和节点特征分别用邻接矩阵A∈Rn×n和特征矩阵X∈Rn×d表示。在数学上,图卷积网络将卷积的运算扩展到谱域中的网络数据[17],并通过谱卷积函数学习分层地潜在表示。图卷积网络的图卷积运算可以简单地定义为

(1) 式中:H(l)为卷积层l层的输入;H(l+1)为卷积层之后的输出;W(l)为在神经网络中第l层需要训练的权重矩阵。
图卷积网络的每一层都可以用函数f表示:

(2) 式中:

本文使用Relu函数作为激活函数来提取图结构数据的非线性特征,可以避免梯度消失问题。图卷积网络的每一个卷积层仅处理一阶邻域信息,因此通过叠加若干卷积层可以有效地捕获多阶邻域(多跳)的信息传递[17],从而捕获节点间的空间关联特征。考虑到通信节点的计算能力有限,卷积层设置不宜过多,本文设置2个卷积层来构建图卷积网络,其时间复杂度为O(EdHF),E为边数,d为特征维度,H为中间层维度,F为输出层维度。两层图卷积网络堆叠起来获得两跳范围内邻居特征的汇合,从而捕获空间依赖性,节点属性特征X作为第一层的输入,相当于H(0),输出Z不仅编码每个节点的特征信息,还涉及顺序节点邻近信息。

(3) 
(4) 式中:

对于动态图任务考虑时间t,图卷积网络单元输入随时间变化的邻接矩阵At和特征矩阵Xt,输出Gt:

(5) 3.2 基于GRU的时间特征提取
通常用于处理时间序列数据的神经网络模型是递归神经网络,但是由于梯度消失和梯度爆炸等缺陷,传统的递归神经网络对长期预测具有局限性[15],LSTM模型和GRU模型[21]是递归神经网络的变体,并且已被证明可以解决上述问题。LSTM和GRU的基本原理大致相同,都使用门控机制来记忆尽可能多的长期信息,然而LSTM结构复杂,所需训练时间较长,而GRU模型具有相对简单的结构、较少的参数和较快的训练速度。因此,本文选择GRU模型从图卷积网络输出中获得时间依赖性。
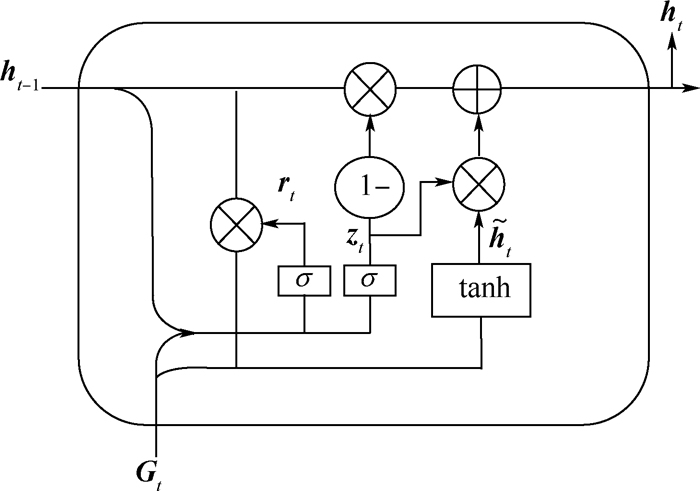
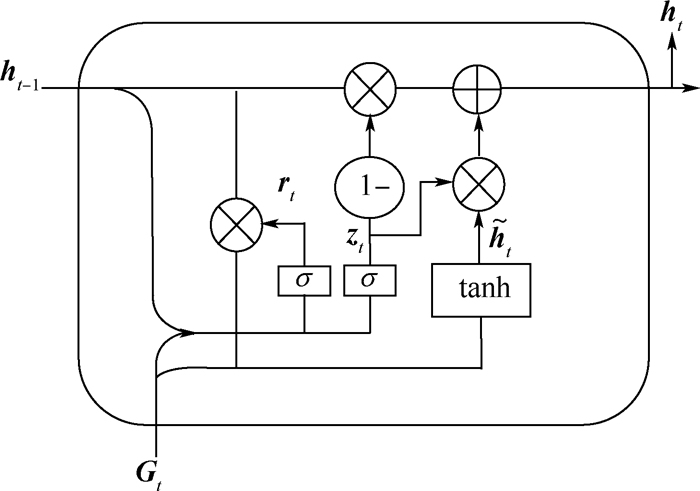
GRU的结构去除了单元状态,而使用隐藏状态来传输信息,如图 3所示。
GRU模型只有2个门结构,分别为更新门zt和重置门rt。更新门的作用类似于LSTM中的遗忘门和输入门,有助于捕捉时间序列里的长期依赖关系,使模型可以快速学习数据的新特征,实时更新调整网络,避免因流数据概念漂移问题导致的模型预测不准确。重置门用来丢弃与预测无关的历史信息,重置门越小,前一状态的信息被写入的越少,有助于捕捉短期依赖关系。

(6) 
(7) 
(8) 
(9) 式中:Gt表示图卷积网络的输出,也是GRU网络的输入;σ表示sigmoid函数;ht-1表示GRU模型中时刻t-1的输出;ht表示时刻t的输出;W为训练过程中的权重参数;GRU通过将隐藏状态ht-1和当前时刻t的节点及空间特征信息Gt作为输入,得到时刻t的节点状态ht。
因此,在捕获当前时刻节点及空间特征信息的同时,模型仍保留着历史信息,通过模型的学习从而捕获拓扑结构与节点属性特征在时间维度的特征信息及演变规律。至此,由图卷积网络和GRU组成的时空图卷积网络获得了网络拓扑结构和节点属性的时空演变特征,当无人机网络遭受网络攻击时,其通信流量行为也会发生较大变化,从而根据空间演变特性和节点属性特征来判断无人机网络是否遭受入侵。
3.3 注意力机制
注意力机制类似于人类的视觉机制,从众多信息中选择与目标最相关的信息,最初应用于图像识别和机器翻译。利用注意力机制可以更加精确地捕获与网络入侵检测最相关的时空特征,以减轻错误或者冗余特征信息带来的负面影响,并提高入侵检测模型分类性能[22]。本文使用注意力机制对时空图卷积网络的输出向量赋予不同的权重,将GRU层输出的向量集合表示为H=[h1, h2, …, ht],注意力机制将产生加权的输出表示x:

(10) 
(11) 
(12) 式中:M为经过激活函数tanh后的输出;Wm为要学习的参数矩阵。权重矩阵U=[U1, U2, …, Ut]代表了不同时间的时空特征的重要程度,所有权重之和为1,而权重越大,注意力越强,对于入侵检测越重要。
3.4 SVM分类器
大多数深度学习分类模型使用softmax激活函数作为神经网络的最后一层进行预测,并最小化交叉熵损失函数,输出所属类别的概率。

(13) 
(14) 式中:si为分类器输出;xk为分类器输入;Wki为连接倒数第二层与softmax层的权重。而本文的输出层使用分类性能更优、收敛速度更快的L2-SVM分类函数来代替常用的softmax函数,SVM的核函数选择通常有线性核、多项式核、高斯核、sigmoid核几种情况,在数据集上进行实验对比,发现线性核、多项式核和高斯核的选择对最终的分类准确率几乎没有影响,而其中线性核由于参数少速度更快,核函数最终选择线性核。使用Hinge Loss作为目标函数:

(15) 式中:wTxi+bi表示整个分类模型最终的输出,xi为输入向量,bi为神经元的偏置参数; ci为i的真实类别;w为训练权重系数;C为惩罚系数,表示对误差的宽容度,惩罚系数过大会导致过拟合,模型泛化能力差,惩罚系数过小会导致欠拟合,模型错误分类数目增多,本文通过交叉验证的方法确定合适的惩罚系数值。
决策函数为每个类生成一个得分向量,取得分最大值作为最终的预测类别class:

(16) 
(17) 式中:决策函数sign为符号函数,其形式为

(18) 3.5 模型参数
本文使用交叉验证法调整超参数,对图卷积网络卷积层数目K尝试了{1, 2, 3}3种值,发现K=2时模型的速度与准确率取得了最优平衡。图卷积层中的卷积核个数为32,GRU中的隐藏单元数为32,使用小批量梯度下降(Mini-Batch Gradient Descent)误差反向传播算法更新网络中的权值,为了在时空图卷积网络的反向传播过程中加快算法的收敛速度,使用对内存需求较小的自适应矩估计(Adam)为优化算法。每次迭代的batch size为256,学习率设置为0.001,训练轮次为300轮,设置dropout为0.3来防止模型过拟合。
4. 实验验证
4.1 数据集
使用多种基准数据集进行实验,由于每个数据集都会有不同的模式和特征,如网络拓扑结构、流量变化、攻击方式等,使用多种数据集可以综合验证模型的适应性。本文结合经典的NSL-KDD数据集[23]、加拿大网络安全研究所提供的CICIDS2017数据集[24]及无线网络的WSN-DS数据集[25]进行模型的训练和测试。表 1为数据集的相关信息。
表 1 数据集相关信息Table 1. Relevant information of datasets数据集 网络攻击类别 WSN-DS 黑洞攻击,灰洞攻击,泛洪攻击,调度攻击 NSL-KDD 拒绝服务攻击,监视和其他探测活动,远程机器的非法访问,普通用户对本地超级用户特权的非法访问 CICIDS2017 FTP暴力破解、SSH暴力破解,拒绝服务攻击,心血漏洞,网页攻击,渗透攻击,僵尸网络 为了更好地模拟无人机网络,参照文献[26]>的方法进行无人机网络的仿真实验,本文使用EXata软件模拟一个1 000 m×1 000 m的动态无人机网络环境,50个移动节点分布其中。详细仿真参数设置如表 2所示。
表 2 仿真参数Table 2. Simulation parameters参数 数值 仿真区域/(m×m) 1 000×1 000 节点数量 50 节点移动模型 随机路径模型 信道容量/(Mbit·s-1) 5 最大移动速度/(m·s-1) 20 攻击节点比例/% 10、20、30 路由协议类型 AODV 采样周期/s 15 考虑到一般无人机的续航时间,本文设置仿真时间为900 s,其中网络攻击时间设置为30 s。实验共进行40次模拟,获得总时长36 000 s的原始流量数据。对多个无人机网络节点连续采样,采样间隔5 s,每次采样后标记统计数据类型为:正常、窃听攻击、分布式拒绝服务(DDoS)攻击、黑洞攻击。最终经过数据预处理后得到无人机网络的统计数据集UAV_set,数据集具体情况如表 3所示。
表 3 UAV_set数据集相关信息Table 3. Relevant information of UAV_set dataset流量类别 数量 正常 2 000 窃听攻击 500 DDoS攻击 700 黑洞攻击 110 4.2 数据预处理
为了提高算法的精度、加快模型的收敛速度,对数据集进行预处理。
1) 检测数据集中的缺失值(Nan),由于对比的传统机器学习算法对缺失值比较敏感,将空值替换为所属特征列的均值。
2) 将处理后的数据集划分为70%的训练集、20%的测试集和10%的验证集。
3) 对数据集的类别标签进行编码。
4) 对数据集特征进行标准化处理,避免特征的尺度不同对模型训练速度和准确率造成的不利影响。
4.3 实验环境及评价指标
本文的实验平台操作系统为Windows10,处理器为Nvidia 1060 GPU,使用机器学习框架TensorFlow实现所有算法。本文采用准确率Accuracy和误报率FAR作为评估指标。

(19) 
(20) 式中:TP表示被正确分类的正样本数目;FN表示被错误分类的正样本数目;FP表示被错误分类为正样本的负样本数目;TN表示正确分类的负样本数目。
4.4 方法比较
将ATGCN方法与已有的7种基准方法进行比较:
1) 孤立森林(IF)[27]:任意选择一个特征,并通过随机选择该特征的最大值和最小值之间的区间值来检测异常。
2) 局部离群因子(LOF)[3]:通过测量给定样本附近的局部密度偏差来计算异常分数,局部密度偏差远小于其邻居的样本被归类为异常。
3) 随机森林(RF)[28]:通过组合决策树有助于解决数据不平衡时的检测问题。
4) MCD[29]:通过计算经验协方差来检测异常点,一种鲁棒性很强的位置和分布估计方法。
5) OCSVM[30]:通过创建一个复杂的边界来描述特征空间中的正常数据。如果新样本超出决策边界,则将其分类为异常。
6) VAE[31]:基于变分自动编码器构建正常数据的生成模型,将重构误差大于阈值的数据视为异常。
7) DAGMM[10]:利用深层自动编码器为每个输入数据点生成低维表示和重构误差,并将其进一步输入高斯混合模型(GMM),通过联合优化的方法减少模型的重建误差。
对于基准方法,分别按照文献中描述的参数设置。所有方法分别使用4个数据集重复独立运行20次,并计算检测结果的准确率和误报率的平均值,结果如表 4所示。可以明显看出,ATGCN方法和DAGMM方法的准确率均优于其他方法,平均稳定在0.96以上,ATGCN方法和VAE方法的误报率明显小于其他方法,平均稳定在0.027以下。证明了本文方法具有较高的检测准确率和较低的误报率,以及ATGCN、VAE和DAGMM这些深度学习方法在网络入侵检测中的有效性。
表 4 不同方法的实验结果比较Table 4. Comparison of experimental results among different methods方法 准确率 误报率 WSN-DS NSL-KDD CICIDS2017 UAV_set WSN-DS NSL-KDD CICIDS2017 UAV_set IF 0.457 0.916 0.735 0.855 0.368 0.145 0.235 0.124 LOF 0.435 0.536 0.669 0.892 0.134 0.127 0.168 0.125 RF 0.886 0.919 0.894 0.884 0.101 0.074 0.096 0.244 MCD 0.610 0.716 0.793 0.863 0.190 0.126 0.122 0.223 OCSVM 0.605 0.880 0.793 0.783 0.201 0.174 0.155 0.117 VAE 0.887 0.916 0.956 0.922 0.027 0.016 0.017 0.022 DAGMM 0.968 0.987 0.992 0.995 0.028 0.044 0.024 0.010 ATGCN 0.988 0.998 0.996 0.997 0.019 0.007 0.016 0.009 4.5 性能验证
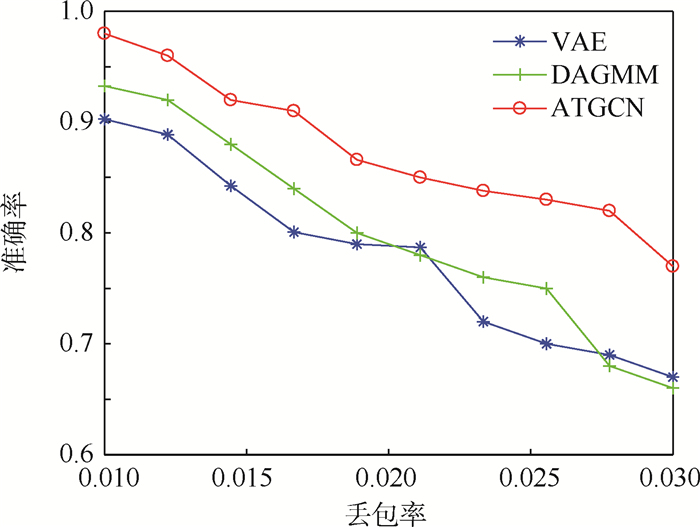
为了模拟无人机网络环境传输稳定性较差、丢包率较高的特点,对UAV_set数据集的测试集进行处理,按照0.01~0.03的丢包率,对测试集中全体样本的数据包进行随机剔除。图 4为ATGCN方法与检测效果较好的VAE方法和DAGMM方法在不同丢包率环境下的检测准确率。可以看出,本文ATGCN方法准确率稳定在0.75以上,优于VAE方法和DAGMM方法,证明了ATGCN方法在传输链路不可靠的网络环境中具有良好的适应性。
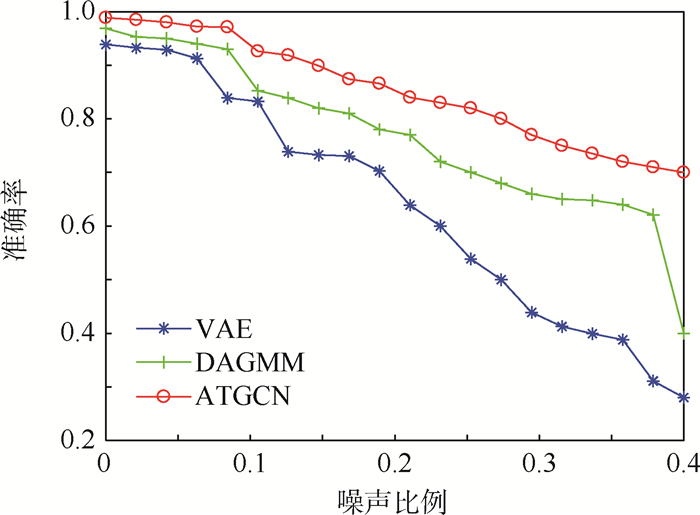
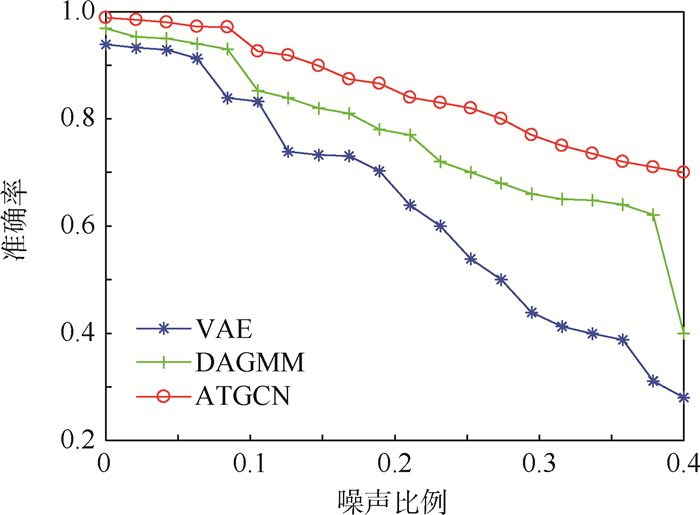
无人机的传感器数据通常包含3种噪声[32],在无线网络WSN-DS数据集的测试集中添加这3种类型噪声,并改变噪声比例来验证方法的鲁棒性。通过图 5可以看出,在噪声影响下ATGCN方法检测准确率相较于其他方法最为稳定,保持在0.7以上,而VAE方法受噪声影响最为明显,准确率最差低于0.3,DAGMM方法在噪声比例达到0.4时,准确率也只有0.4。证明了本文方法相比其他方法具有良好的抗噪声能力和鲁棒性。
4.6 方法设计对检测效果的影响
为进一步研究时空特征的提取和注意力机制对检测模型分类效果的影响,将ATGCN与以下变体进行比较:
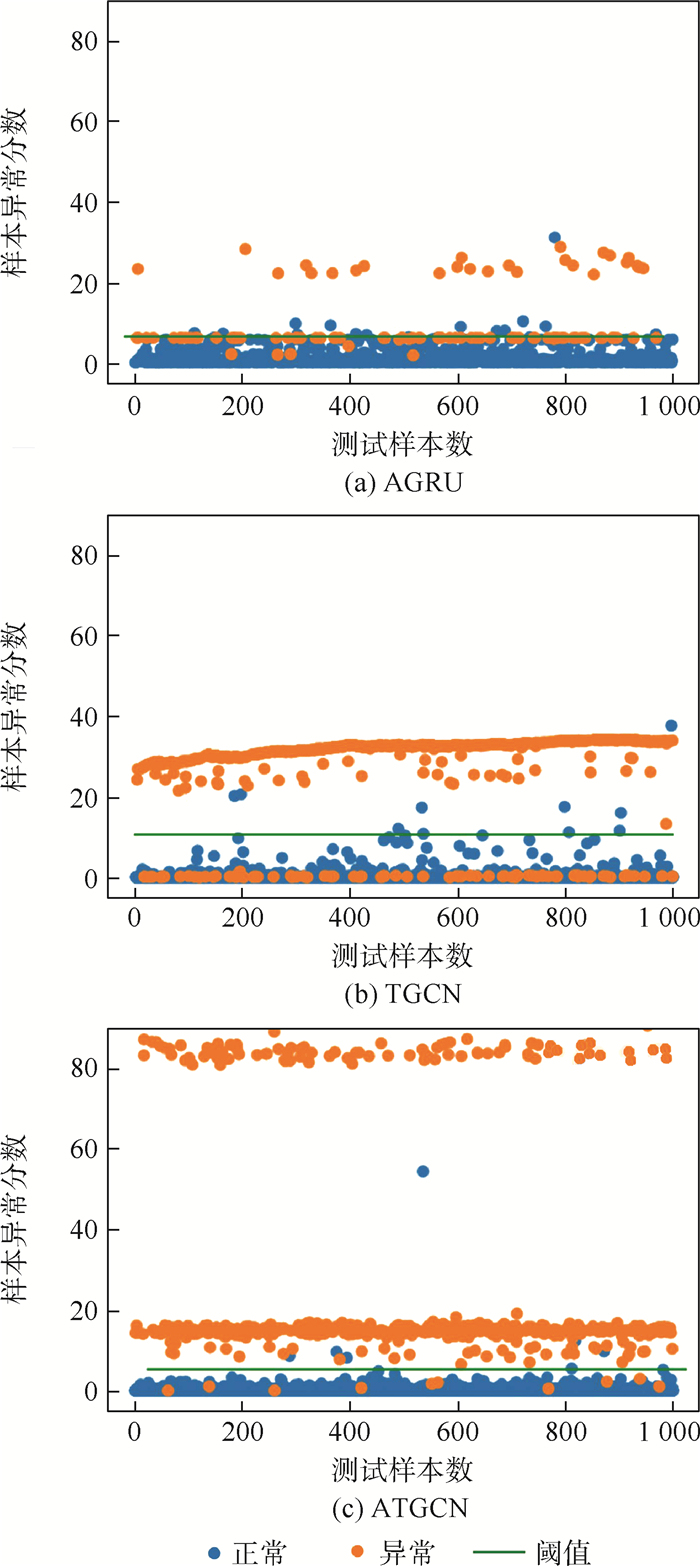
1) AGRU:去除图卷积网络,输入时间序列下的节点属性特征。模型的预测只能从节点的历史数据中推断出来,不能获取拓扑结构的空间演变特征。
2) TGCN:仅去除注意力机制,输入时间序列下的网络拓扑结构和节点属性特征,模型不能精确捕获与网络入侵检测最相关的时空特征。
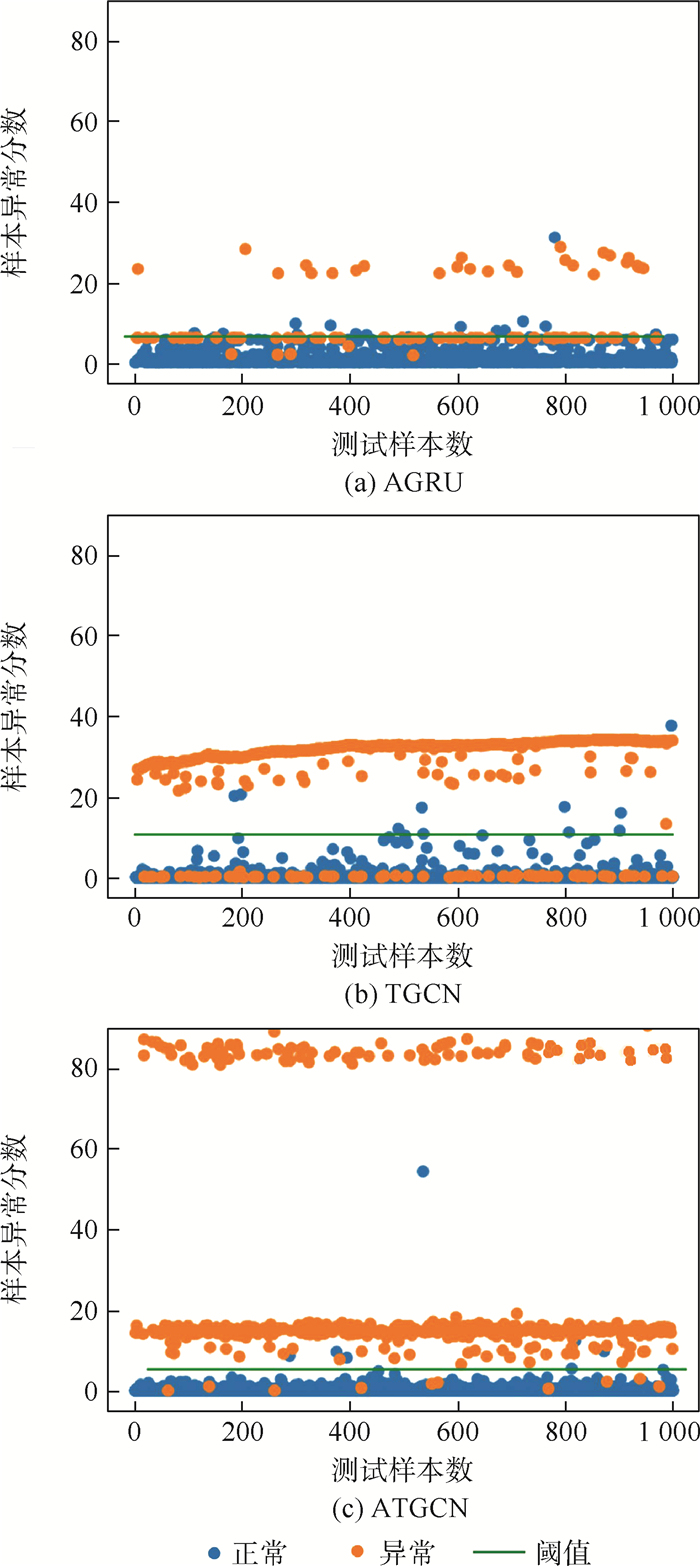
在NSL-KDD、CICIDS2017和WSN-DS这3个数据集的测试集中随机选取10 000个样本进行模型的对比实验,将模型最后一层输出的异常值得分作为纵坐标,样本数目为横坐标,使用阈值来划分正常类和异常类,类别的标签为实际标签,模型检测效果对比如图 6所示。可以明显看出,AGRU和TGCN中的一些异常值得分更接近于正常值,错误分类样本数较多;而ATGCN更能将异常值与正常值区分开来,相比AGRU和TGCN的错误分类样本数较少,只有14例,表明了时空图卷积网络所提取到的时空演变特征及注意力机制的设计对模型检测效果均有明显的提升。
5. 结论
1) 针对无人机网络具有拓扑高度动态、网络连接不稳定的特点,设计时空图卷积网络来捕获网络的时空演变特征,解决了现有方法在入侵检测问题上时空特征提取不足的问题。
2) 将无人机网络的入侵检测问题建模为图网络的节点分类问题,将时间序列观测值和动态拓扑图都纳入入侵检测模型中,证明了提取时空演变特征和引入注意力机制对模型分类效果的提升。
3) 在多个数据集上的实验表明,本文方法的检测准确率平均为0.99,而误报率平均为0.01,检测效果优于传统的入侵检测方法,并且验证了时空演变特征的提取和注意力机制的设计对模型检测效果有明显的提升。模拟丢包率高和噪声干扰的无人机网络环境,ATGCN依然具有良好的适应性。
-
表 1 数据集相关信息
Table 1. Relevant information of datasets
数据集 网络攻击类别 WSN-DS 黑洞攻击,灰洞攻击,泛洪攻击,调度攻击 NSL-KDD 拒绝服务攻击,监视和其他探测活动,远程机器的非法访问,普通用户对本地超级用户特权的非法访问 CICIDS2017 FTP暴力破解、SSH暴力破解,拒绝服务攻击,心血漏洞,网页攻击,渗透攻击,僵尸网络 表 2 仿真参数
Table 2. Simulation parameters
参数 数值 仿真区域/(m×m) 1 000×1 000 节点数量 50 节点移动模型 随机路径模型 信道容量/(Mbit·s-1) 5 最大移动速度/(m·s-1) 20 攻击节点比例/% 10、20、30 路由协议类型 AODV 采样周期/s 15 表 3 UAV_set数据集相关信息
Table 3. Relevant information of UAV_set dataset
流量类别 数量 正常 2 000 窃听攻击 500 DDoS攻击 700 黑洞攻击 110 表 4 不同方法的实验结果比较
Table 4. Comparison of experimental results among different methods
方法 准确率 误报率 WSN-DS NSL-KDD CICIDS2017 UAV_set WSN-DS NSL-KDD CICIDS2017 UAV_set IF 0.457 0.916 0.735 0.855 0.368 0.145 0.235 0.124 LOF 0.435 0.536 0.669 0.892 0.134 0.127 0.168 0.125 RF 0.886 0.919 0.894 0.884 0.101 0.074 0.096 0.244 MCD 0.610 0.716 0.793 0.863 0.190 0.126 0.122 0.223 OCSVM 0.605 0.880 0.793 0.783 0.201 0.174 0.155 0.117 VAE 0.887 0.916 0.956 0.922 0.027 0.016 0.017 0.022 DAGMM 0.968 0.987 0.992 0.995 0.028 0.044 0.024 0.010 ATGCN 0.988 0.998 0.996 0.997 0.019 0.007 0.016 0.009 -
[1] 何道敬, 杜晓, 乔银荣, 等.无人机信息安全研究综述[J].计算机学报, 2019, 42(5):150-168.HE D J, DU X, QIAO Y R, et al.A survey on cyber security of unmanned aerial vehicles[J].Chinese Journal of Computers, 2019, 42(5):150-168(in Chinese). [2] JAWHAR I, MOHAMED N, AL-JAROODI J, et al.Communication and networking of UAV-based systems:Classification and associated architectures[J].Journal of Network and Computer Applications, 2017, 84:93-108. doi: 10.1016/j.jnca.2017.02.008 [3] KUMAR N, KUMAR U.Anomaly-based network intrusion detection: An outlier detection techniques[C]//International Conference on Soft Computing and Pattern Recognition.Berlin: Springer, 2016: 262-269. [4] ZIMEK A, FILZMOSER P.There and back again:Outlier detection between statistical reasoning and data mining algorithms[J].Wiley Interdisciplinary Reviews:Data Mining and Knowledge Discovery, 2018, 8(6):e1280. doi: 10.1002/widm.1280 [5] DIVYA K, KUMARAN N S.Survey on outlier detection techniques using categorical data[J].International Research Journal of Engineering and Technology, 2016, 3(12):899-904. [6] DESHMUKH M M K, KAPSE A.A survey on outlier detection technique in streaming data using data clustering approach[J].International Journal of Engineering and Computer Science, 2016, 5(1):15453-15456. [7] JIANG F, LIU G, DU J, et al.Initialization of K-modes clustering using outlier detection techniques[J].Information Sciences, 2016, 332:167-183. doi: 10.1016/j.ins.2015.11.005 [8] CHEN J, SATHE S, AGGARWAL C, et al.Outlier detection with autoencoder ensembles[C]//Proceedings of the 2017 SIAM International Conference on Data Mining, 2017: 90-98. [9] KWON D, KIM H, KIM J, et al.A survey of deep learning-based network anomaly detection[J].Cluster Computing, 2019, 22:949-961. doi: 10.1007/s10586-017-1117-8 [10] ZONG B, SONG Q, MIN M R, et al.Deep autoencoding Gaussian mixture model for unsupervised anomaly detection[C]//ICLR, 2018: 1-19. [11] DOMINGUES R, FILIPPONE M, MICHIARDI P, et al.A comparative evaluation of outlier detection algorithms:Experiments and analyses[J].Pattern Recognition, 2018, 74:406-421. doi: 10.1016/j.patcog.2017.09.037 [12] CHAWLA A, LEE B, FALLON S, et al.Host based intrusion detection system with combined CNN/RNN model[C]//Joint European Conference on Machine Learning and Knowledge Discovery in Databases.Berlin: Springer, 2018: 149-158. [13] SHONE N, NGOC T N, PHAI V D, et al.A deep learning approach to network intrusion detection[J].IEEE Transactions on Emerging Topics in Computational Intelligence, 2018, 2(1):41-50. doi: 10.1109/TETCI.2017.2772792 [14] TAN X, SU S, ZUO Z, et al.Intrusion detection of UAVs based on the deep belief network optimized by PSO[J].Sensors, 2019, 19(24):5529. doi: 10.3390/s19245529 [15] KIM G, YI H, LEE J, et al.LSTM-based system-call language modeling and robust ensemble method for designing host-based intrusion detection systems[EB/OL].(2016-11-06)[2020-03-01]. [16] WANG W, SHENG Y, WANG J, et al.HAST-IDS:Learning hierarchical spatial-temporal features using deep neural networks to improve intrusion detection[J].IEEE Access, 2017, 6:1792-1806. [17] ZHANG Z, CUI P, ZHU W.Deep learning on graphs: A survey[EB/OL].(2018-12-11)[2020-03-01]. [18] ZHENG J, LI D.GCN-TC: Combining trace graph with statistical features for network traffic classification[C]//IEEE International Conference on Communications.Piscataway: IEEE Press, 2019: 1-6. [19] HSU D.Anomaly detection on graph time series[EB/OL].(2017-08-09)[2020-03-01]. [20] ZHAO L, SONG Y, ZHANG C, et al.T-GCN:A temporal graph convolutional network for traffic prediction[J].IEEE Transactions on Intelligent Transportation Systems, 2020, 21(9):3848-3858. doi: 10.1109/TITS.2019.2935152 [21] DEY R, SALEMT F M.Gate-variants of gated recurrent unit (GRU) neural networks[C]//IEEE 60th International Midwest Symposium on Circuits and Systems.Piscataway: IEEE Press, 2017: 1597-1600. [22] LEE J B, ROSSI R A, KIM S, et al.Attention models in graphs:A survey[J].ACM Transactions on Knowledge Discovery from Data (TKDD), 2019, 13(6):1-25. [23] TAVALLAEE M, BAGHERI E, LU W, et al.A detailed analysis of the KDD CUP 99 data set[C]//IEEE Symposium on Computational Intelligence for Security and Defense Applications.Piscataway: IEEE Press, 2009: 1-6. [24] SHARAFALDIN I, LASHKARI A H, GHORBANI A A.Toward generating a new intrusion detection dataset and intrusion traffic characterization[C]//Proceedings of the 4th International Conference on Information Systems Security and Privacy, 2018: 108-116. [25] ALMOMANI I, AL-KASASBEH B, AL-AKHRAS M.WSN-DS:A dataset for intrusion detection systems in wireless sensor networks[J].Journal of Sensors, 2016, 2016:1-16. [26] 张冰涛, 王小鹏, 王履程, 等.基于图论的MANET入侵检测方法[J].电子与信息学报, 2018, 40(6):1446-1452.ZHANG B T, WANG X P, WANG L C, et al.Intrusion detection method for MANET based on graph theory[J].Journal of Electronics and Information Technology, 2018, 40(6):1446-1452(in Chinese). [27] SUN L, VERSTEEG S, BOZTAS S, et al.Detecting anomalous user behavior using an extended isolation forest algorithm: An enterprise case study[EB/OL].(2016-09-21)[2020-03-01]. [28] 杨晓晖, 张圣昌.基于多粒度级联孤立森林算法的异常检测模型[J].通信学报, 2019, 40(8):133-142.YANG X H, ZHANG S C.Anomaly detection model based on multi-grained cascade isolation forest algorithm[J].Journal on Communications, 2019, 40(8):133-142(in Chinese). [29] BHARAMBE A, RAVINDRAN R, SUCHDEV R, et al.A robust anomaly detection system[C]//2014 International Conference on Advances in Engineering & Technology Research.Piscataway: IEEE Press, 2014: 1-7. [30] SHANG W, ZENG P, WAN M, et al.Intrusion detection algorithm based on OCSVM in industrial control system[J].Security and Communication Networks, 2016, 9(10):1040-1049. doi: 10.1002/sec.1398 [31] LOPEZ-MARTIN M, CARRO B, SANCHEZ-ESGUEVILLAS A, et al.Conditional variational autoencoder for prediction and feature recovery applied to intrusion detection in iot[J].Sensors, 2017, 17(9):1967. doi: 10.3390/s17091967 [32] ZHANG Y, SZABO C, SHENG Q Z.Cleaning environmental sensing data streams based on individual sensor reliability[C]//International Conference on Web Information Systems Engineering.Berlin: Springer, 2014: 405-414. 期刊类型引用(24)
1. 闫培玲,刘俊娟. 基于布谷鸟算法的实验室网络入侵数据检测. 计算机仿真. 2025(03): 448-451+456 .  百度学术
百度学术2. 于继江. 基于机器学习与DBN网络的网络入侵检测方法研究. 微型电脑应用. 2024(01): 184-187 .  百度学术
百度学术3. 顾正祥. 基于Agent人工智能的异构网络多重覆盖节点入侵检测系统设计. 计算机测量与控制. 2024(05): 17-23+30 .  百度学术
百度学术4. 聂萌瑶,刘鑫. 正则化极限学习下细粒度网络入侵检测仿真. 计算机仿真. 2024(05): 419-423 .  百度学术
百度学术5. 张婧,范海燕,丁鲁彬,刘凯华,陈杰. 基于麻雀搜索算法的电力数据中心网络入侵安全检测方法. 电气自动化. 2024(06): 103-105 .  百度学术
百度学术6. 王蕊. 基于深度神经网络的多模态数据分类与识别技术研究. 中国宽带. 2024(06): 61-63 .  百度学术
百度学术7. 强丽丽,郭磊. 基于均衡化样本类别的图书馆网络入侵自动检测研究. 自动化与仪器仪表. 2023(01): 48-52 .  百度学术
百度学术8. 李梦歌,王海珍. 基于LSTM-DNN模型的入侵检测方法. 高师理科学刊. 2023(01): 38-41 .  百度学术
百度学术9. 应贤儿,陈馨儿,孙乐瑶,李俊蓉,刘建华,朱子豪,蒋峻泽,黄文豪. 基于图神经网络的病毒传播网络入侵检测研究. 工业控制计算机. 2023(05): 104-105+108 .  百度学术
百度学术10. 钱鑫. 基于改进机器学习的无人机网络入侵自动感知系统设计. 自动化与仪器仪表. 2023(08): 1-4+9 .  百度学术
百度学术11. 周浩. 基于区块链的复杂网络近邻入侵风险检测算法. 成都工业学院学报. 2023(05): 60-64 .  百度学术
百度学术12. 蔡娟,兰娅勋,刘源. 基于GBDT优化算法的局域网入侵定位与检测研究. 计算机测量与控制. 2023(10): 90-96 .  百度学术
百度学术13. 吴延慧,杨凌凤. 开放实验室内部网络非法入侵准确检测仿真. 计算机仿真. 2023(09): 411-415 .  百度学术
百度学术14. 薛峪峰,马晓琴,罗红郊,田光欣. 海量冗余数据冲击下网络入侵检测方法. 电子设计工程. 2023(22): 167-170+175 .  百度学术
百度学术15. 左娟娟,陈宇民,朱红杰,彭文英,黄桂雪. 基于深度置信网络的电力系统网络入侵检测方法. 电子设计工程. 2023(24): 85-89 .  百度学术
百度学术16. 谭荣华,王俊,舒建文. 基于改进时间卷积网络的局域网异常预测仿真. 计算机仿真. 2023(12): 465-469 .  百度学术
百度学术17. 王巍,谷壬倩,彭力,赵继军,魏忠诚,常存喜. 基于无人机的物联网空基中继鲁棒优化. 物联网学报. 2022(01): 101-112 .  百度学术
百度学术18. 张静,苏蓓蓓,黄星杰,尚智婕,赵金梦. TCP/IP数据包匹配技术在企业黑客入侵检测中的应用. 企业科技与发展. 2022(01): 82-84 .  百度学术
百度学术19. 谭韶生,夏旭. 数据挖掘的船舶通信网络非法入侵智能检测方法. 舰船科学技术. 2022(17): 144-147 .  百度学术
百度学术20. 郭艳华. 基于大数据技术的实时网络信息安全监测. 长江信息通信. 2022(12): 14-16 .  百度学术
百度学术21. 谭秦红,田应信. 基于人工智能的通信网络入侵检测系统设计. 长江信息通信. 2022(12): 189-191 .  百度学术
百度学术22. 张彦晖,吕娜,刘鹏飞,陈卓. 基于卷积注意力门控循环网络的加密流量分类方法. 信号处理. 2021(07): 1180-1188 .  百度学术
百度学术23. 张格菲,李春宇,刘金坤,屈音璇. 基于YOLOv5的毫米波图像目标检测方法研究. 宇航计测技术. 2021(05): 41-45 .  百度学术
百度学术24. 杨顶,邓明君,徐丽萍. 基于时空信息融合学习的路段行程车速短时预测. 计算机工程. 2021(12): 78-86 .  百度学术
百度学术其他类型引用(3)
-








 下载:
下载:





 下载:
下载:

 百度学术
百度学术