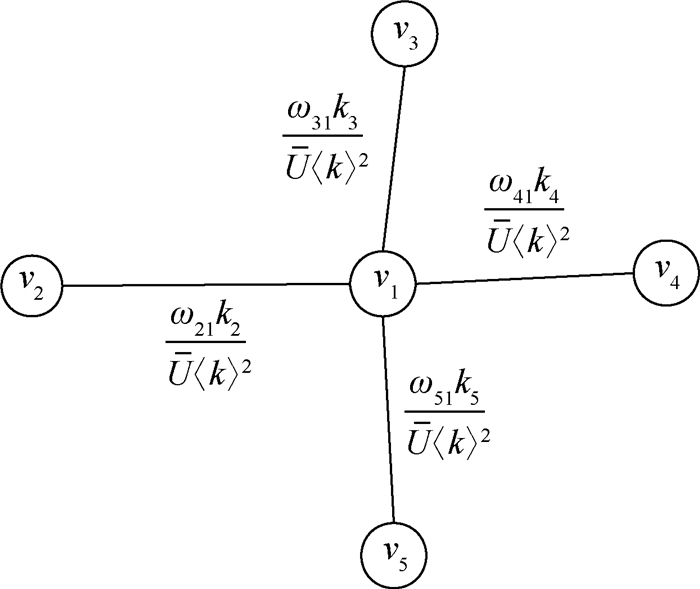
-
摘要:
在水下通信系统中,仅仅考虑节点的强度来描述水下通信系统中各个节点的重要性是片面的,为了更好地对水下通信系统的节点重要性进行评估,提出了节点连通度这一指标对水下通信系统进行描述。对节点连通度的定义和方法进行了说明,并对水下通信系统节点重要性和失效方式进行了计算推导,得到水下通信系统节点信息被获取的概率的计算方法。通过对一个水下通信模型进行仿真,验证了节点连通度指标可以描述水下通信系统的生存性。
Abstract:In the underwater communication system, it is one-sided to describe the importance of each node in the underwater communication system only by considering the strength of the node. In order to better evaluate the importance of the node in the underwater communication system, this paper proposes the node connectivity.This indicator describes the underwater communication system, explains the definition and method of node connectivity, and calculates and derives the importance and failure mode of the underwater communication system node, and obtains the information of the underwater communication system node. The probability calculation method, by simulating an underwater communication model, verifies that the node connectivity index can describe the survivability of the underwater communication system.The underwater communication system is composed of nodes and links. Identify those nodes that play a vital role in the communication information transmission process of the underwater communication system, and accurately assess the importance of the nodes in the underwater communication system. Improving the survivability of the entire communication system has great theoretical guidance and practical application significance. In the underwater communication system, it is one-sided to describe the importance of each node in the underwater communication system by only considering the strength of the node. In order to better evaluate the importance of the node in the underwater communication system, this paper proposes the node connectivity. This index describes the underwater communication system, and by simulating an underwater communication model, it is verified that the node connectivity index can describe the survivability of the underwater communication system.
-
Key words:
- node connectivity /
- node failure /
- intentional attack /
- random failure /
- underwater communication system
-
-
[1] 肖炜, 谭敏生, 丁琳. 复杂网络生存性评估方法研究[J]. 电脑知识与技术: 学术交流, 2010, 6(1): 241-243.XIAO W, TAN M S, DING L. Research on survivability assessment methods for complex networks[J]. Computer Knowledge and Technology: Academic Communication, 2010, 6(1): 241-243(in Chinese). [2] LEE C Y.Analysis of switching networks[EB/OL].(2012-07-04)[2020-05-20]. [3] NRSC.Network reliability steering committee[EB/OL].(2012-08-28)[2020-05-20]. [4] 赵娟. 基于路径的通信网络可靠性评估与分析[D]. 重庆: 中国人民解放军后勤工程学院, 2012.ZHAO J.Reliability assessment and analysis of communication network based on path[D].Chongqing: PLA Logistics Engineering College, 2012(in Chinese). [5] 陈德润. 弹性光网络的多故障生存性虚拟映射方法研究[D]. 重庆: 重庆邮电大学, 2020.CHEN D R.Study on multi-fault survivability virtual mapping for elastic optical networks[D].Chongqing: Chongqing University of Post and Telecommunications, 2020(in Chinese). [6] JONES D A, GREENE B C, PIKUS I M, et al.President's commission on critical infrastructure protection and presidential decision directive 63[M]//VOELLER J G.Wiley Handbook of Science and Technology for Homeland Security.New York: Wiley, 2009. [7] 史赞, 李青. 增强网络生存性的ATM技术[J]. 光通信研究, 1995(3): 14-19.SHI Z, LI Q. ATM technology to enhance network survivability[J]. Optical Communication Research, 1995(3): 14-19(in Chinese). [8] 隆克平, 杨丰瑞, 陈继努. 宽带传输网络的生存性技术及其设计方法的研究[J]. 重庆邮电学院学报, 1997, 9(3): 10-16.LONG K P, YANG F R, CHEN J N. Survivability technology and design method of broadband transmission network[J]. Journal of Chongqing University of Posts and Telecommunications, 1997, 9(3): 10-16(in Chinese). [9] 宋文东, 蔡建新, 孙金伦. 宽带光纤网中一种基于光开关的自愈策略[J]. 南京邮电学院学报, 1998, 18(2): 25-30.SONG W D, CAI J X, SUN J L. A self-healing strategy based on optical switch in broadband fiber network[J]. Journal of Nanjing University of Posts and Telecommunications, 1998, 18(2): 25-30(in Chinese). [10] 王东霞, 窦文华, 周兴铭. ATM自愈网的一种恢复调度策略[J]. 电子学报, 2000, 28(8): 102-103.WANG D X, DOU W H, ZHOU X M. A recovery scheduling strategy for ATM self-healing networks[J]. Acta Electronica Sinica, 2000, 28(8): 102-103(in Chinese). [11] 罗启彬, 邱昆, 张宏斌. 基于WDM技术光传送网的生存性分析[J]. 电子科技大学学报, 2001, 30(4): 335-340.LUO Q B, QIU K, ZHANG H B. Survivability analysis of optical transmission network based on WDM technology[J]. Journal of University of Electronic Science and Technology of China, 2001, 30(4): 335-340(in Chinese). [12] 黎红长. 光纤通信网络的生存性及经济性分析[J]. 广西通信技术, 2001(2): 17-23.LI H C. Survivability and economic analysis of optical fiber communication networks[J]. Guangxi Communication Technology, 2001(2): 17-23(in Chinese). [13] 赵季红, 李增智, 曲桦. WDM环网保护方式的性能评价及设计原则[J]. 计算机工程与应用, 2001(21): 4-8.ZHAO J H, LI Z Z, QU H. Performance evaluation and design principles of WDM ring network protection[J]. Computer Engineering and Application, 2001(21): 4-8(in Chinese). [14] 调联红, 伍翔, 王一超, 等. 一种光纤通信系统可用性的算法及分析[J]. 电子学报, 2001, 29(12): 1712-1716.TIAO L H, WU X, WANG Y C, et al. An algorithm and analysis of the usability of optical fiber communication system[J]. Acta Electronica Sinica, 2001, 29(12): 1712-1716(in Chinese). [15] 高德云, 舒炎泰, 奇兰涛. 全光网及QoS机制研究[J]. 计算机应用, 2002, 22(3): 4-6.GAO D Y, SHU Y T, QI L T. Research on all-optical network and QoS mechanism[J]. Computer Applications, 2002, 22(3): 4-6(in Chinese). [16] 李景聪, 吴德明, 徐安士. IP over WDM光网络及其生存性问题讨论[J]. 光电子激光, 2002, 13(2): 25-30.LI J C, WU D M, XU A S. Discussion on IP over WDM optical network and its survivability[J]. Photoelectron Laser, 2002, 13(2): 25-30(in Chinese). [17] 钱学森, 宋健. 工程控制论[M]. 3版. 北京: 科学出版社, 2011.QIAN X S, SONG J. Engineering cybernetics[M]. 3rd ed. Beijing: Science Press, 2011(in Chinese). [18] LEWIS T G. 网络科学: 原理与应用[M]. 陈向阳, 巨修练, 等, 译. 北京: 机械工业出版社, 2011.LEWIS T G.Network science: Theory and applications[M].CHEN X Y, JU X L, et al, translated.Beijing: China Machine Press, 2011(in Chinese). [19] 王浩. 基于误码率分析的高速数字光纤通信系统可靠性研究[D]. 济南: 山东大学, 2018.WANG H.Reliability research of high-speed digital optical fiber communication system based on bit error rate analysis[D].Jinan: Shandong University, 2018(in Chinese). [20] 陈勇, 胡爱群, 胡骏, 等. 通信网中最重要节点的确定方法[J]. 高技术通讯, 2004, 14(1): 21-24.CHEN Y, HU A Q, HU J, et al. Determination of the most important nodes in communication networks[J]. High Technology Communications, 2004, 14(1): 21-24(in Chinese). [21] BARRAT A, BARTHÉLEMY M, VESPIGNANI A. Weighted evolving networks: Coupling topology and weight dynamics[J]. Physical Review Letters, 2004, 92(22): 228701. doi: 10.1103/PhysRevLett.92.228701 [22] SYDNEY A, SCOGLIO C, YOUSSEF M, et al. Characterising the robustness of complex networks[J]. International Journal of Internet Technology and Secured Transactions, 2010, 2(3-4): 291-320. doi: 10.1504/IJITST.2010.037406 [23] 胡斌, 黎放. 多种攻击策略下无标度网络修复策略[J]. 系统工程与电子技术, 2010, 32(1): 86-89.HU B, LI F. Scale-free network repair strategies under multiple attack strategies[J]. Systems Engineering and Electronics, 2010, 32(1): 86-89(in Chinese). [24] KHOUFI I, MINET P, LAOUITI A, et al. Survey of deployment algorithms in wireless sensor networks: Coverage and connectivity issues and challenges[J]. International Journal of Autonomous and Adaptive Communications Systems, 2017, 10(4): 341-390. doi: 10.1504/IJAACS.2017.088774 -







 下载:
下载: