-
摘要:
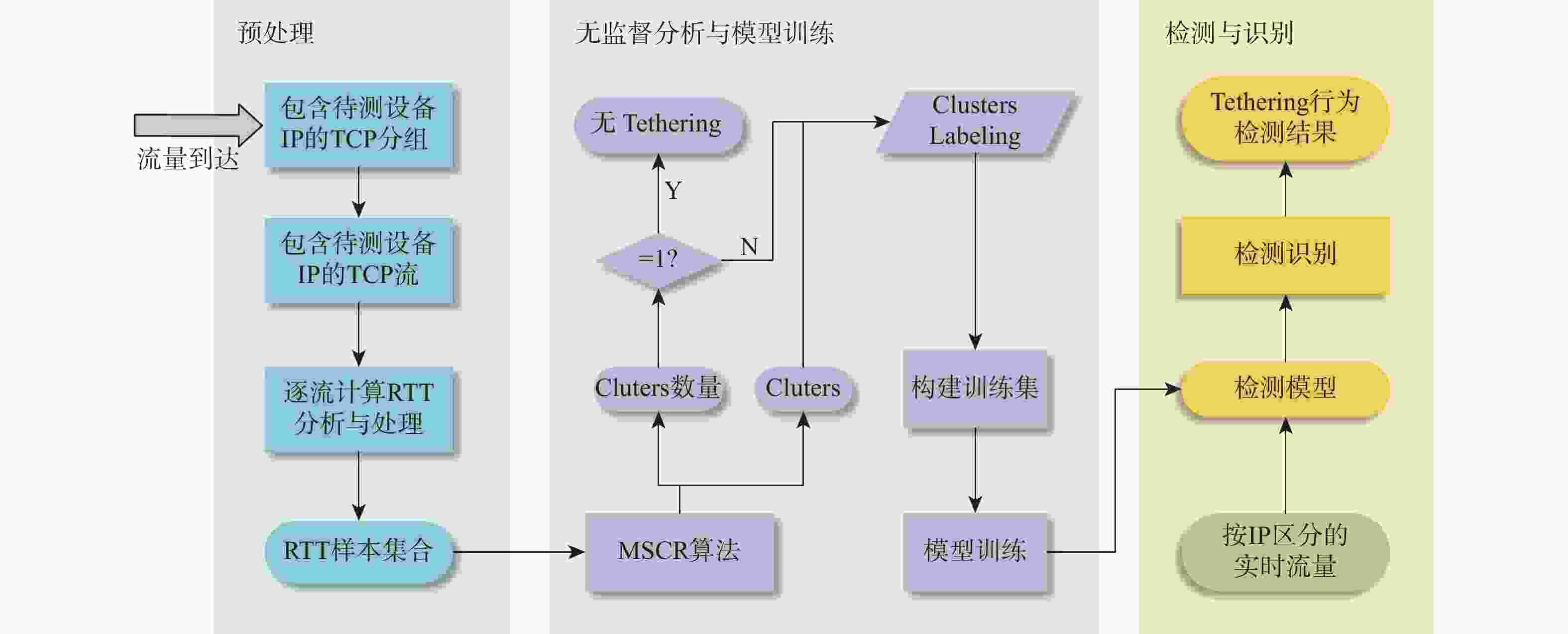
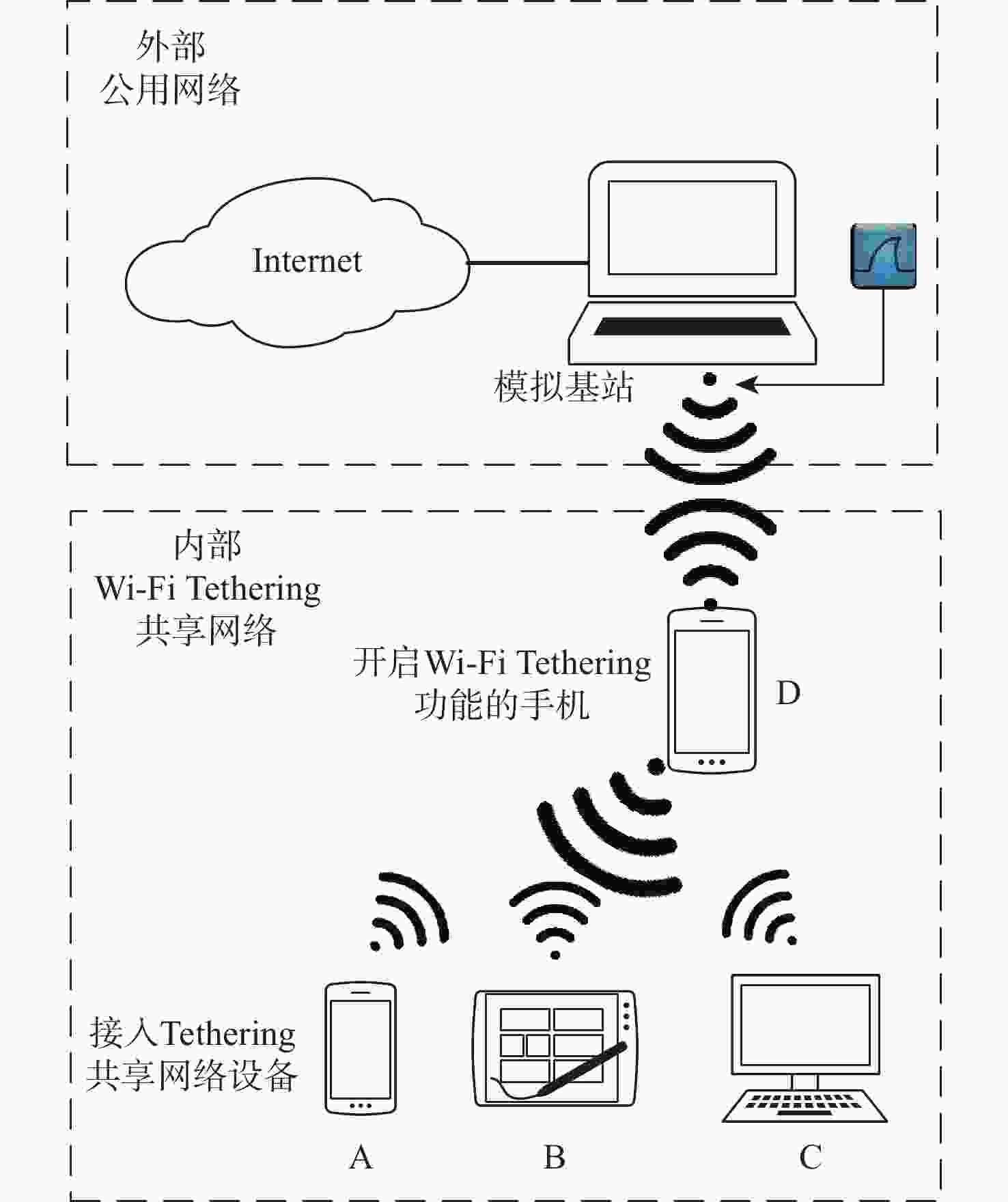
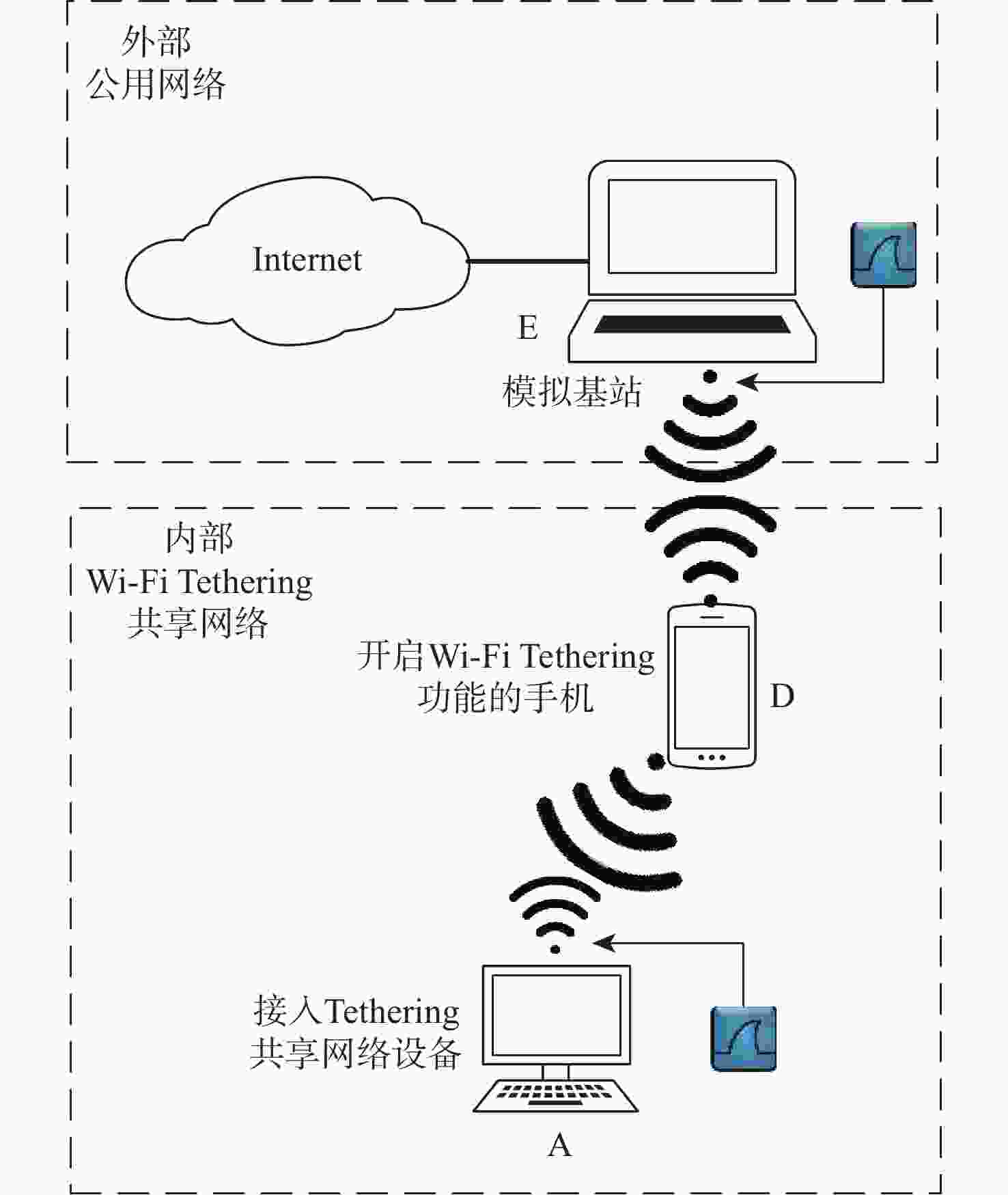
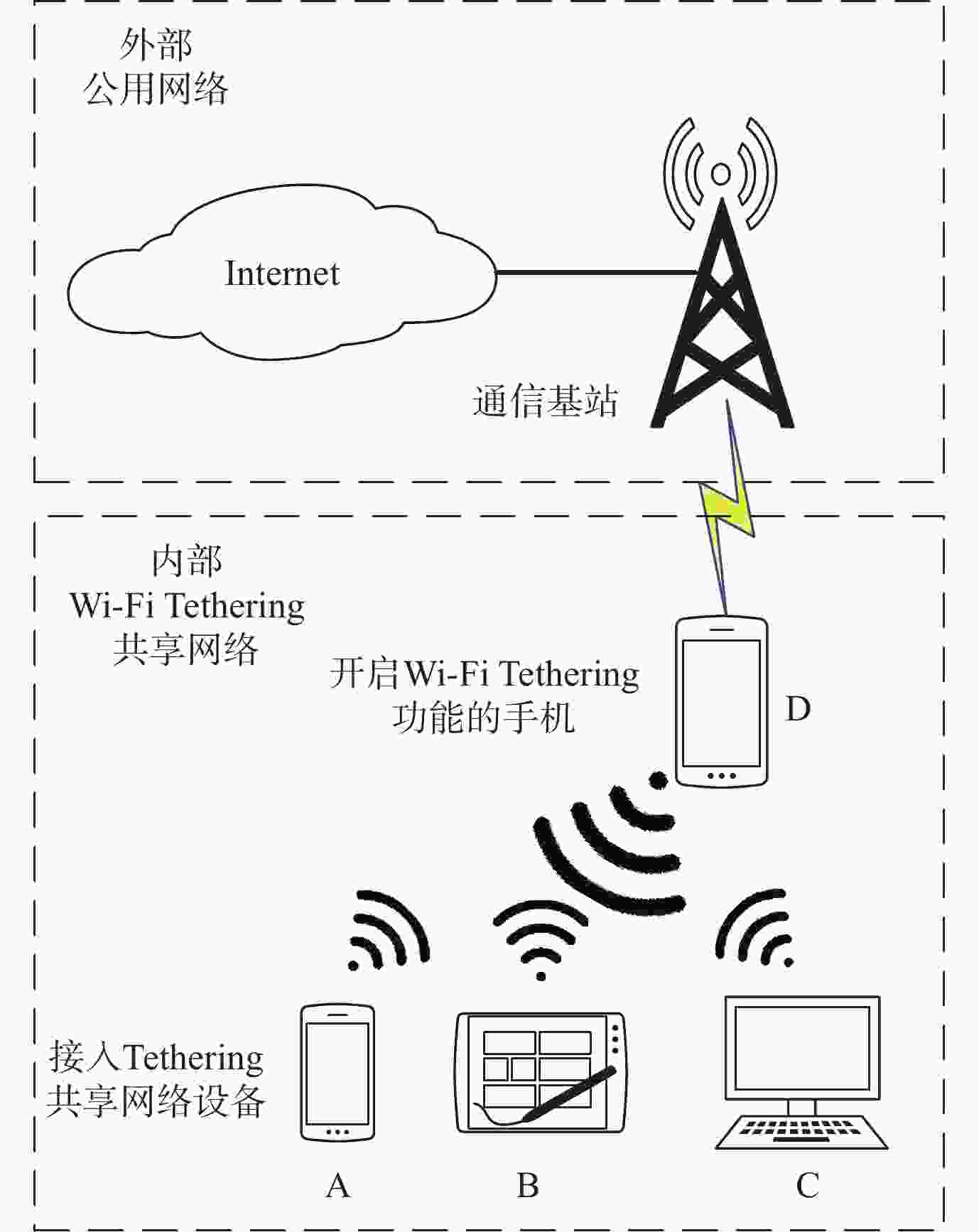
Tethering行为是一种移动设备通过自身传输介质共享其互联网连接服务的行为,其不仅对移动互联网造成运营压力和收益影响,还对移动互联网隐藏其内部网络结构,造成网络安全隐患。由于Tethering存在诸多混淆和规避方法,现有Tethering行为检测技术难以有效检测。鉴于此,分析了移动互联网通信基站中,Tethering行为终端在数据流量的处理、转发等特征,以及移动互联网用户流量中传输控制协议(TCP)流往返时延(RTT)的相关特性,提出一种基于TCP流RTT测量的Tethering检测架构,构建了所提架构的测试网络环境。实验结果表明:所提架构在检测Tethering行为中具有有效性,实现了利用无监督学习和被动监测网络流量对移动互联网中Tethering行为的有效检测,对Tethering行为检测的准确率达到97.50%。
-
关键词:
- Tethering检测 /
- 往返时延 /
- 网络地址转换检测 /
- 无监督学习 /
- 移动互联网
Abstract:Tethering behaviour is the sharing of an Internet connection service with other connected devices by using a mobile smart device as a NAT gateway. It will share the smartphone's data plan, especially the unlimited data plan. So, it can put ISPs under additional pressure to operate mobile Internet and have an impact on their revenue. It can hide the internal network structure from the public network same as Network Address Translation (NAT). It also provides the possibility for illegal devices to access anonymously. Due to many limitations and circumventing methods in tethering detection, the existing NAT detection technology is difficult to detect tethering behavior. In order to process and forward data traffic, we examine the features of tethering behaviors terminal devices in mobile Internet communication base station. We also analyze the relevant characteristics of RTT in TCP flows in mobile Internet traffic. Then, we propose a tethering detection method based on unsupervised analysis of RTT in TCP flows, and construct the test network environment of this method. The experimental results verify the effectiveness of this method in detecting tethering behavior, and realize the effective detection of tethering behavior in mobile Internet by passive network traffic monitoring ,with an accuracy of 97.50%.
-
表 1 实验硬件平台的主要参数
Table 1. Main parameters of experiment hardware platform
序号 设备名称 型号 主要参数 1 模拟基站(PC) Dell Vostro 14-5480 CPU:Core i5-5200U;RAM:4 GB;512 GB HDD;OS:Win 8 Pro Terrans Force X911 CPU:Core i7-4940MX;RAM:32 GB;1TB SSD;OS:Win 10 Pro 2 Tethering设备 Huawei P40 CPU:Kirin 990 5G;RAM:8 GB;OS:Android 10 Mi10 Pro CPU:snapdragon 865;RAM:12 GB;OS:Android 11 Mi11 Ultra CPU:snapdragon 888;RAM:12 GB;OS:Android 11 3 挂载设备(手机) iPhone 6 CPU:Apple A8;OS:ios 12.5.4 iPhone 8 Plus CPU:Apple A11;OS:ios 14.6 Redmi 7 CPU:snapdragon 632;OS:Android 9 Mi10 Pro CPU:snapdragon 865;OS:Android 11 Mi11 Ultra CPU:snapdragon 888;OS:Android 11 Mi9 CPU:snapdragon 855;OS:Android 11 4 挂载设备(PC) ThinkPad X1C 2016 CPU:Core i7-6600U;RAM:8 GB;OS:Win 10 Pro 表 2 实验数据集信息
Table 2. Information of datasets in the experiment
数据集 Tethering模式 手机设备型号 待测设备IP地址 大小/MB 分组个数 DataSet1 无Tethering iphone6 192.168.137.109 1003 1000000 DataSet2 无Tethering P40 192.168.137.157 912 1000000 DataSet3 无Tethering P40 192.168.137.157 412 600000 DataSet4 TetheringD+A P40、iphone6 192.168.137.157 973 1000000 DataSet5 TetheringD+A P40、iphone6 192.168.137.157 910 1000000 DataSet6 TetheringD+A P40、iphone6 192.168.137.157 900 1000000 DataSet7 TetheringD+A P40、iphone6 192.168.137.157 943 1000000 DataSet8 TetheringD+A P40、iphone6 192.168.137.157 466 500000 DataSet9 TetheringD+A P40、iphone6 192.168.137.157 439 500000 DataSet10 TetheringD+A+B P40、iphone6、iphone8 Plus 192.168.137.157 961 1000000 DataSet11 TetheringD+A+B+C P40、iphone6、iphone8 Plus、Redmi7 192.168.137.157 1935 2000000 DataSet12 无Tethering Mi10 Pro 192.168.137.238 984 1000000 DataSet13 无Tethering Mi11 Ultra 192.168.137.142 1024 903103 DataSet14 TetheringD+A Mi10 Pro、Mi11 Ultra 192.168.137.238 1136 1200000 DataSet15 TetheringD+A Mi11 Ultra、Mi10 Pro 192.168.137.142 1218 1400000 DataSet16 TetheringD+A+B+C Mi10 Pro、Mi11 Ultra、Mi9、X1C 192.168.137.238 1157 1200000 DataSet17 TetheringD+A+B+C Mi11 Ultra、Mi10 Pro、Mi9、X1C 192.168.137.142 1372 1500000 DataSet18 TetheringD+A P40、X1C 192.168.137.157 859 909785 DataSet19 无Tethering P40 192.168.137.157 376 403776 表 3 数据集实验结果
Table 3. Experimental results of data sets
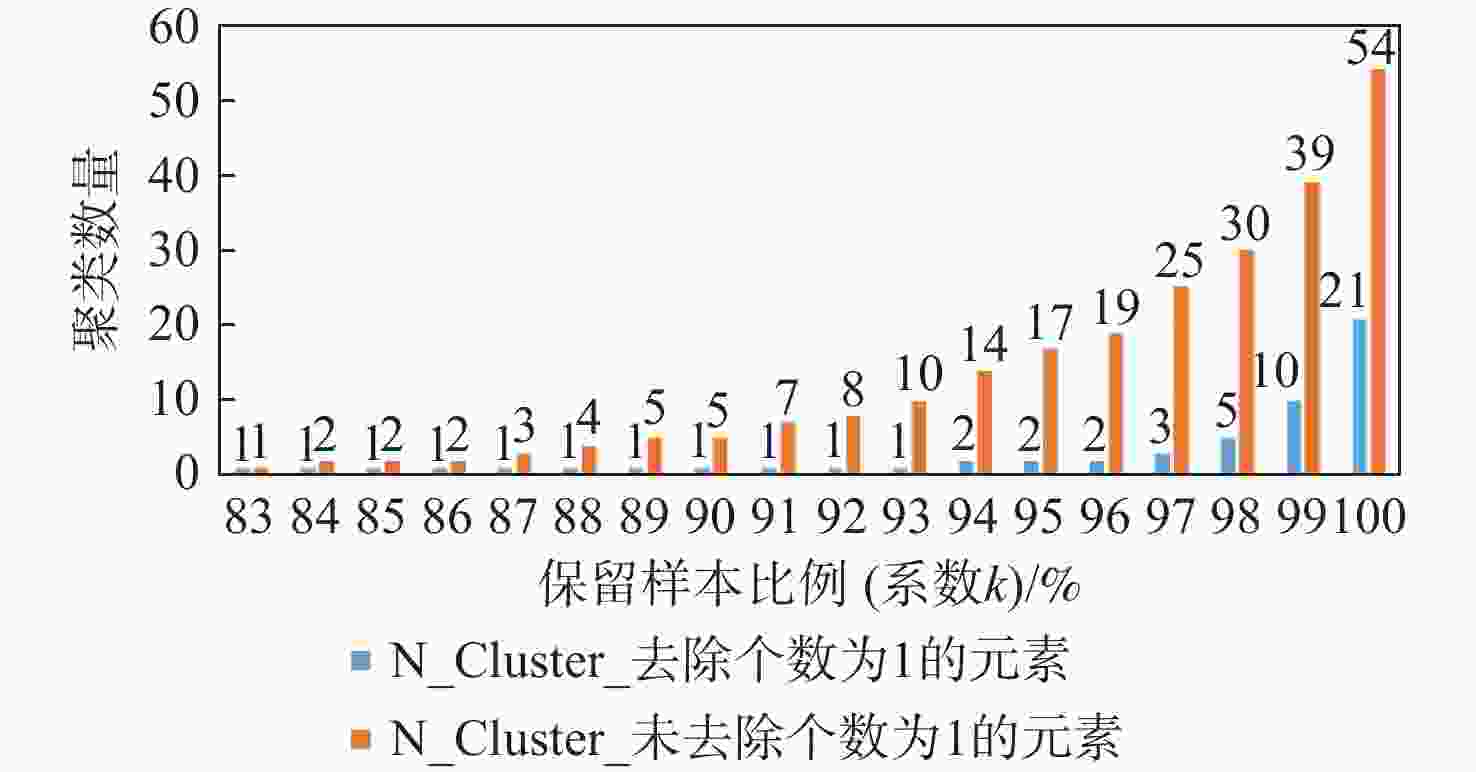
数据集 Tethering模式 RTT数量 n_clusters DataSet1 无Tethering 1176 1 DataSet2 无Tethering 6347 1 DataSet3 无Tethering 7850 1 DataSet4 TetheringD+A 3435 2 DataSet5 TetheringD+A 1979 2 DataSet6 TetheringD+A 2754 2 DataSet7 TetheringD+A 2358 9 DataSet8 TetheringD+A 423 2 DataSet9 TetheringD+A 1820 2 DataSet10 TetheringD+A+B 3251 2 DataSet11 TetheringD+A+B+C 6377 2 DataSet12 无Tethering 2279 1 DataSet13 无Tethering 1877 1 DataSet14 TetheringD+A 5168 4 DataSet15 TetheringD+A 4497 2 DataSet16 TetheringD+A+B+C 4171 7 DataSet17 TetheringD+A+B+C 2606 19 表 4 DataSet18和DataSet19构建测试集分类结果
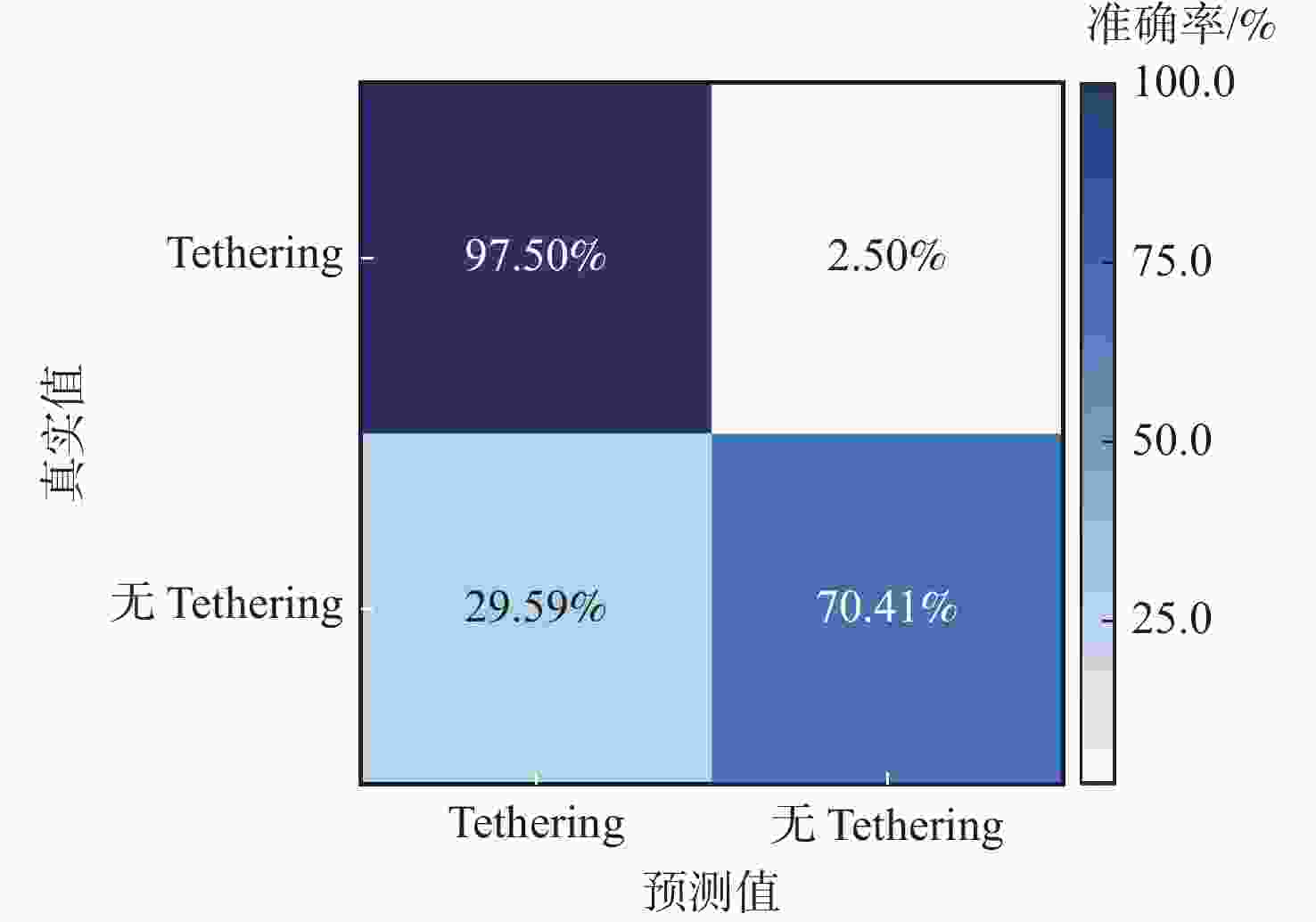
Table 4. Classification results of test dataset built by DataSet18 and DataSet19
标签名称 标签总个数 分类结果 准确率/% Tethering 无Tethering Tethering 4312 4204 108 97.50 无Tethering 3400 1006 2394 70.41 -
[1] WIKI. Tethering[EB/OL]. (2020-03-08) [2021-03-21]. https://en.wikipedia.org/wiki/Tethering. [2] CHOI J. Detection of misconfigured Wi-Fi tethering in managed networks[J/OL]. Preprints, 2020, (2020-03-08) [2021-03-21]. https://www.preprints.org/manuscript/202002.0189/v1. DOI: 10.20944/PREPRINTS202002.0189.V1. [3] We Are Social. Digital 2023: China[EB/OL]. (2021-02-09) [2021-03-21].https://datareportal.com/reports/digital-2023-China. [4] 胡治国, 田春岐, 杜亮, 等. IP网络性能测量研究现状和进展[J]. 软件学报, 2017, 28(1): 105-134.HU Z G, TIAN C Q, DU L, et al. Current research and future perspective on IP network performance measurement[J]. Journal of Software, 2017, 28(1): 105-134(in Chinese). [5] DALAL P, SARKAR M, KOTHARI N, et al. Refining TCP’s RTT dependent mechanism by utilizing link retransmission delay measurement in wireless LAN[J]. International Journal of Communication Systems, 2017, 30(5): 1-20. [6] CISCO. Cisco ASR 5000 ECS Administration Guide StarOS Release 21.18[EB/OL]. (2020-10-05)[2021-03-21]. https://www.cisco.com/c/en/us/td/docs/wireless/asr_5000/21-18_6-12/ECS-Admin/21-18-ECS-Admin/21-17-ECS-Admin_chapter_011000.html#id_39377. [7] STRAKA K, MANES G. Passive detection of nat routers and client counting[C]//Advances in Digital Forensics II: IFIP international Conference on Digital Forensics. Berlin: Springer , 2006: 239-246. [8] MAIER G, SCHNEIDER F, FELDMANN A. NAT usage in residential broadband networks[C]//International Conference on Passive and Active Network Measurement. Berlin: Springer, 2011: 32-41. [9] PARK H, SHIN S, ROH B, et al. Identification of hosts behind a NAT device utilizing multiple fields of IP and TCP[C]//2016 International Conference on Information and Communication Technology Convergence. Piscataway: IEEE Press, 2016: 484-486. [10] ZHANG B, GUAN Y, NIU W, et al. A hybrid packet clustering approach for NAT host analysis[C]//2015 IEEE International Conference on Communication Software and Networks. Piscataway: IEEE Press, 2015: 432-438. [11] ABT S, DIETZ C, BAIER H, et al. Passive remote source NAT detection using behavior statistics derived from netflow[C]//IFIP International Conference on Autonomous Infrastructure, Management and Security. Berlin: Springer, 2013: 148-159. [12] GOKCEN Y, FOROUSHANI V A, HEYWOOD A N Z. Can we identify NAT behavior by analyzing traffic flows?[C]//2014 IEEE Security and Privacy Workshops. Piscataway: IEEE Press, 2014: 132-139. [13] KOMAREK T, GRILL M, PEVNY T. Passive NAT detection using HTTP access logs[C]//2016 IEEE International Workshop on Information Forensics and Security. Piscataway: IEEE Press, 2016: 1-6. [14] SALOMONSSON S. Exploring NAT host counting using network traffic flows[D]. Karlstad : Sweden Karlstad University, 2017: 59-73. [15] KHATOUNI A S, ZHANG L, AZIZ K, et al. Exploring NAT detection and host identification using machine learning[C]//2019 15th International Conference on Network and Service Management. Piscataway: IEEE Press, 2019: 1-8. [16] IBRAHIM M, LIU H, JAWAHAR M, et al. Verification: Accuracy evaluation of Wi-Fi fine time measurements on an open platform [C]//Proceedings of the 24th Annual International Conference on Mobile Computing and Networking. New York: ACM , 2018: 417-427. [17] HAN K, YU S M, KIM S L, et al. Exploiting user mobility for Wi-Fi RTT positioning: A geometric approach[J]. IEEE Internet of Things Journal, 2021, 8(19): 14589-14606. doi: 10.1109/JIOT.2021.3070367 [18] ROY A K, KHAN A K. Privacy preservation with RTT-based detection for wireless mesh networks[J]. IET Information Security, 2020, 14(4): 391-400. doi: 10.1049/iet-ifs.2019.0492 [19] HOU B, HOU C, ZHOU T, et al. Detection and characterization of network anomalies in large-scale RTT time series[J]. IEEE Transactions on Network and Service Management, 2021, 18(1): 793-806. doi: 10.1109/TNSM.2021.3050495 [20] CHENG Y. Mean shift, mode seeking, and clustering[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 1995, 17(8): 790-799. doi: 10.1109/34.400568 [21] COMANICIU D. An algorithm for data-driven bandwidth selection[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2003, 25(2): 281-288. -






 下载:
下载: