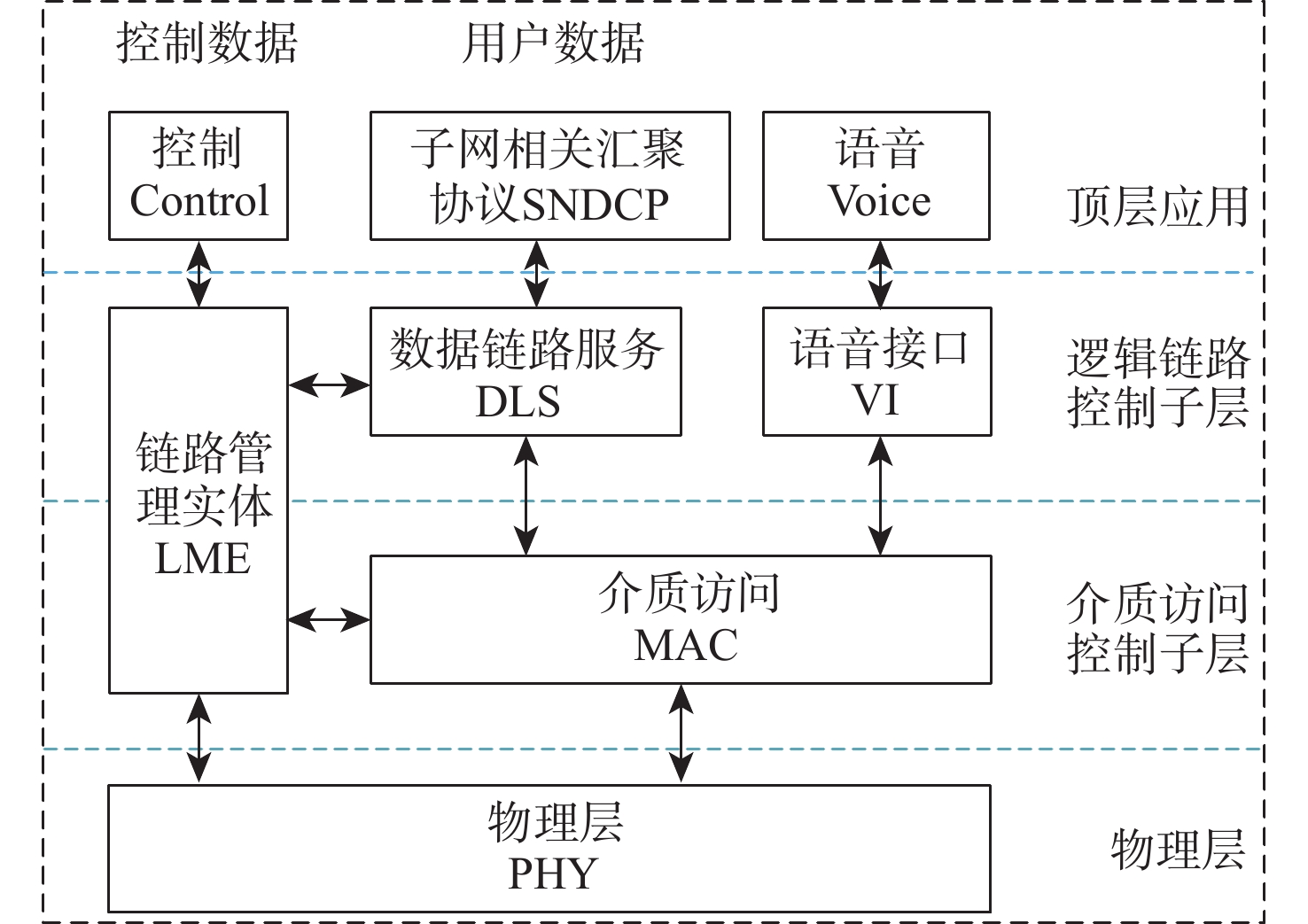
Data security transmission protection mechanism for L-band digital aeronautical communications system based on national cryptographic algorithms
-
摘要:
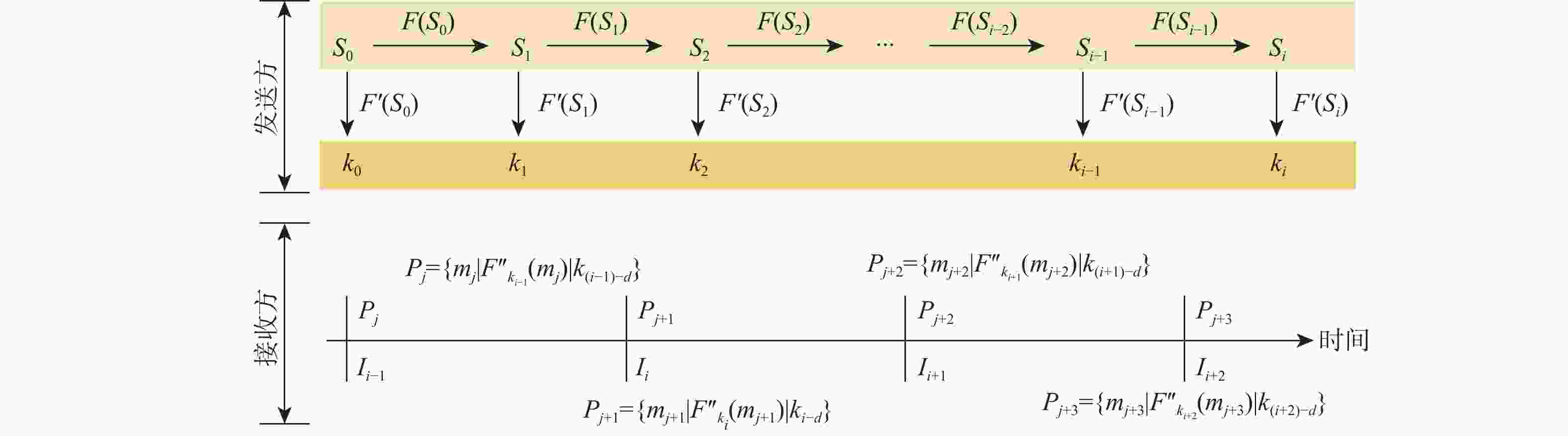
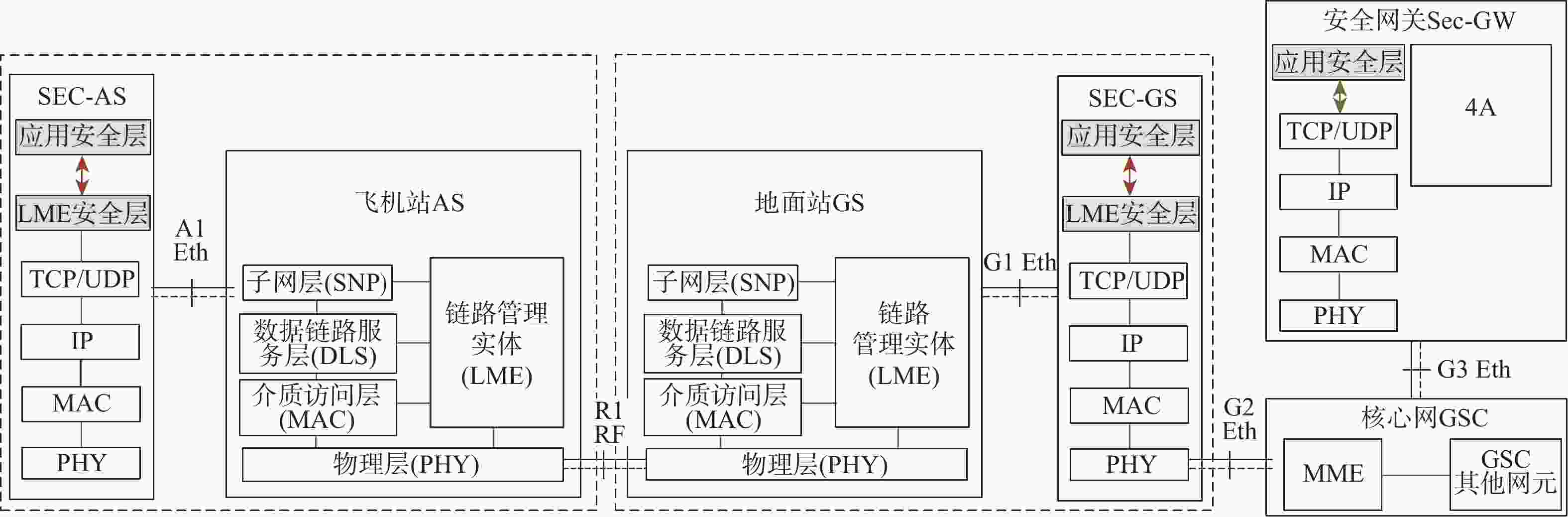
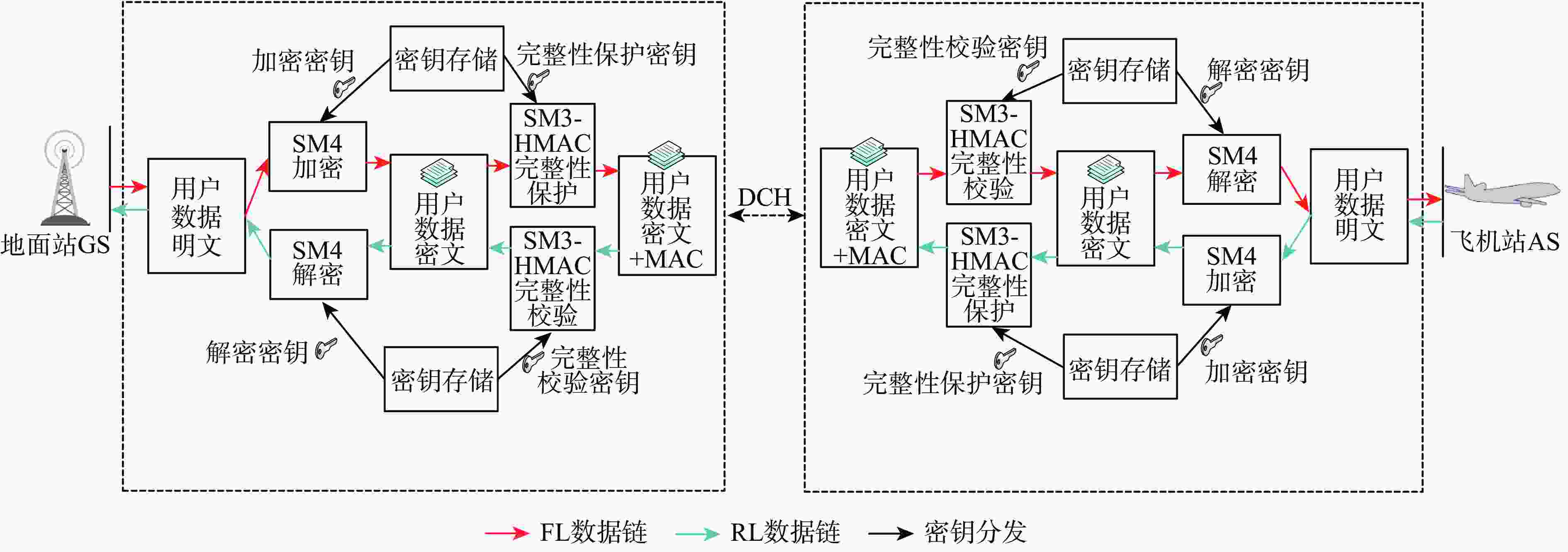
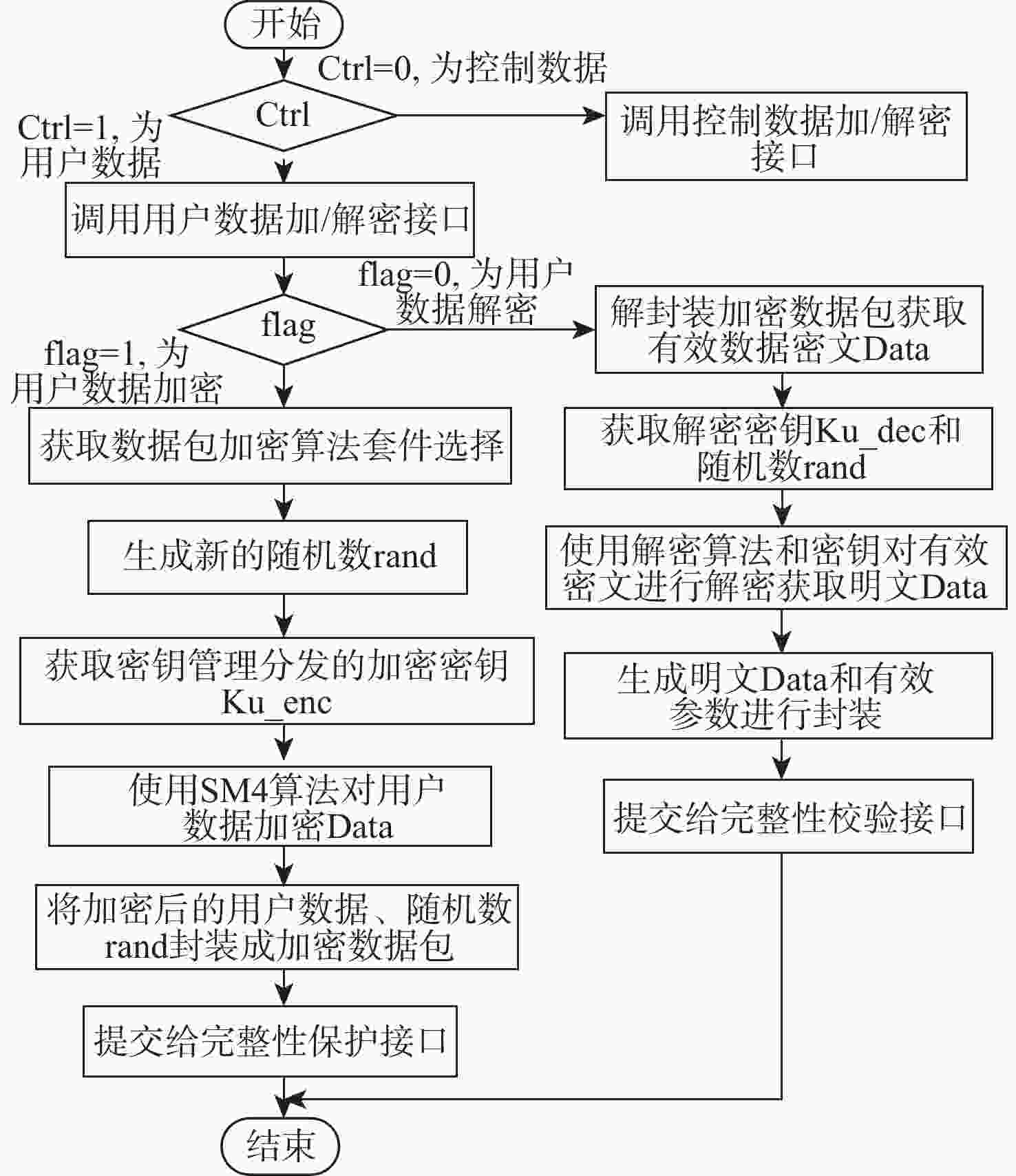
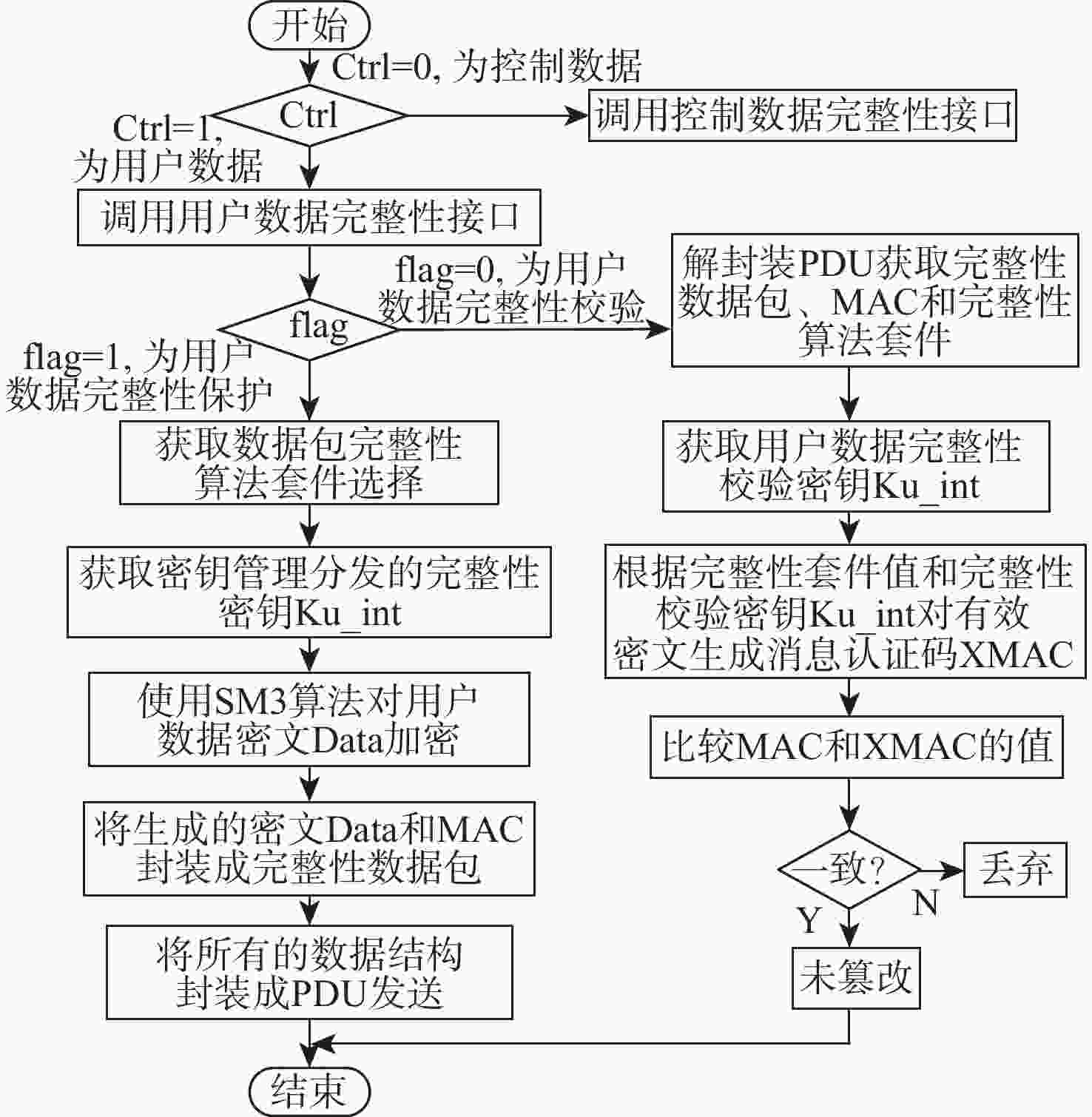
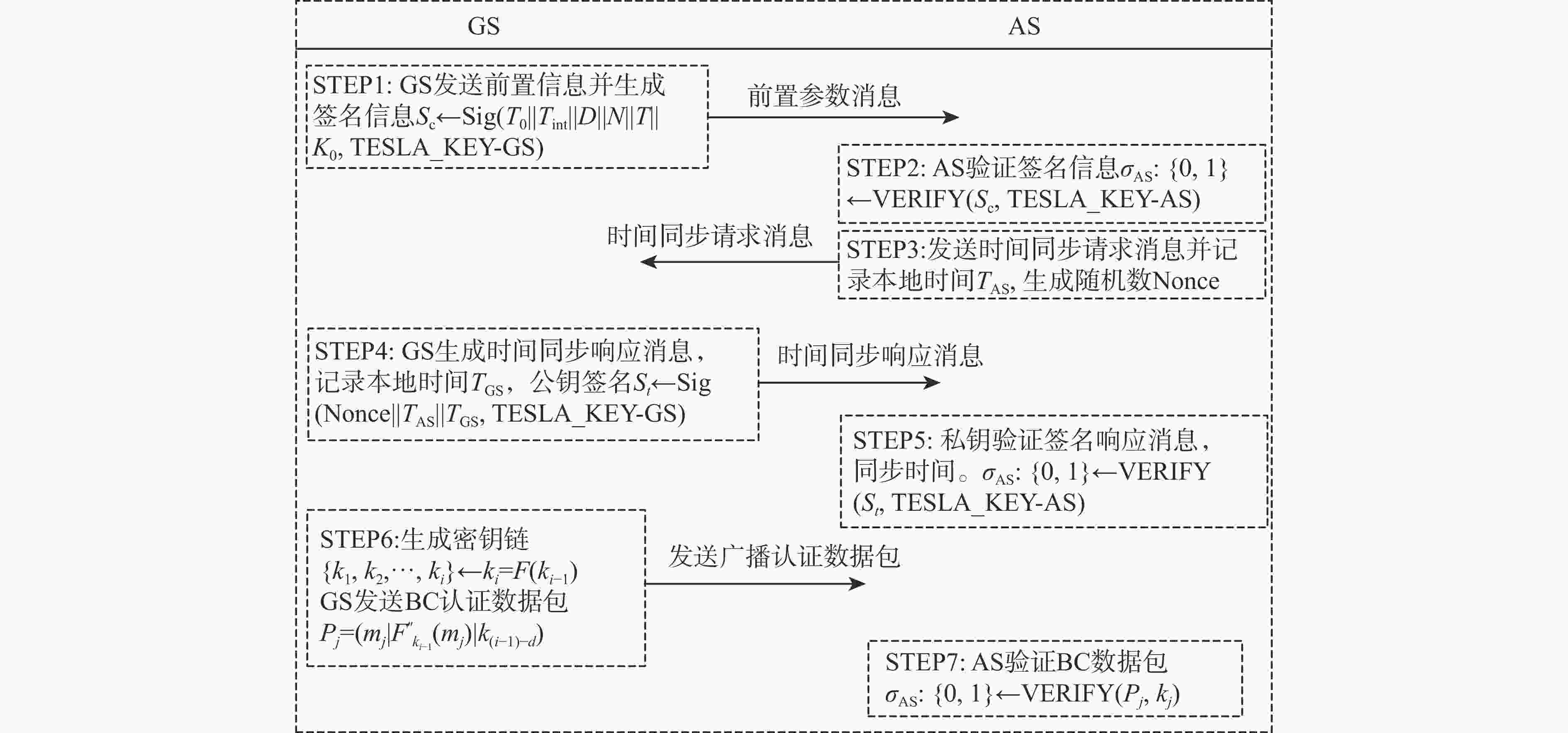
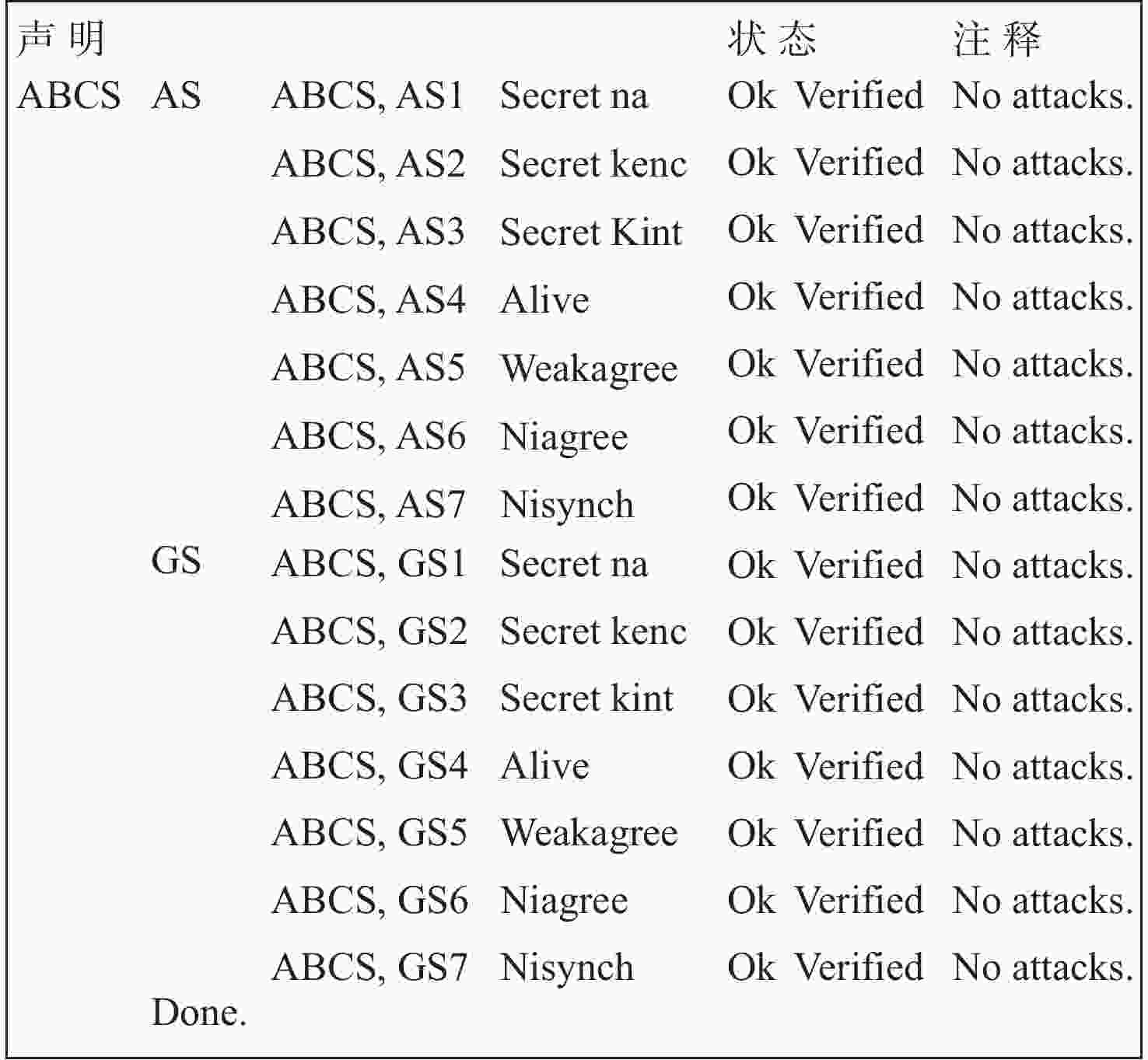
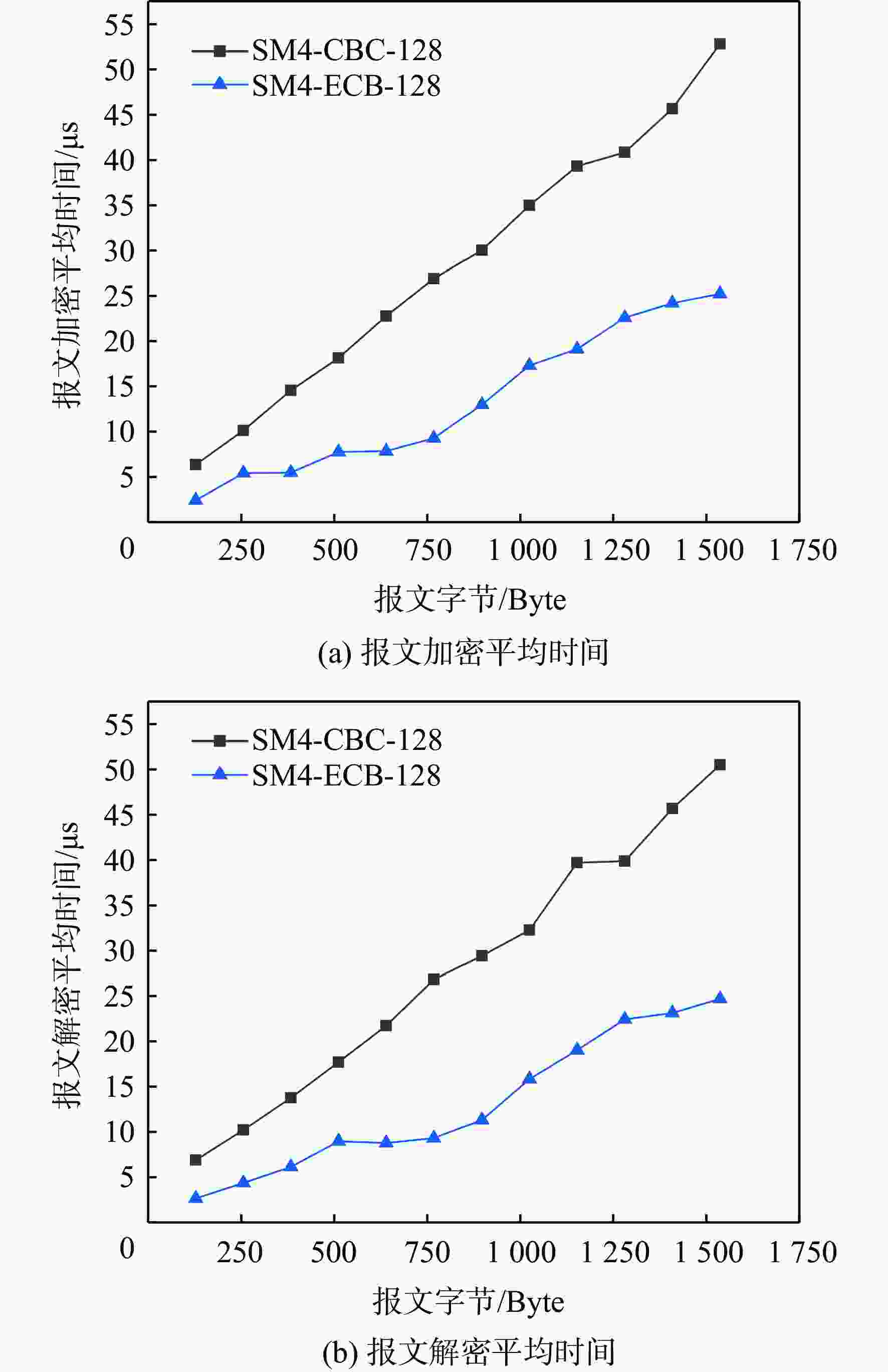
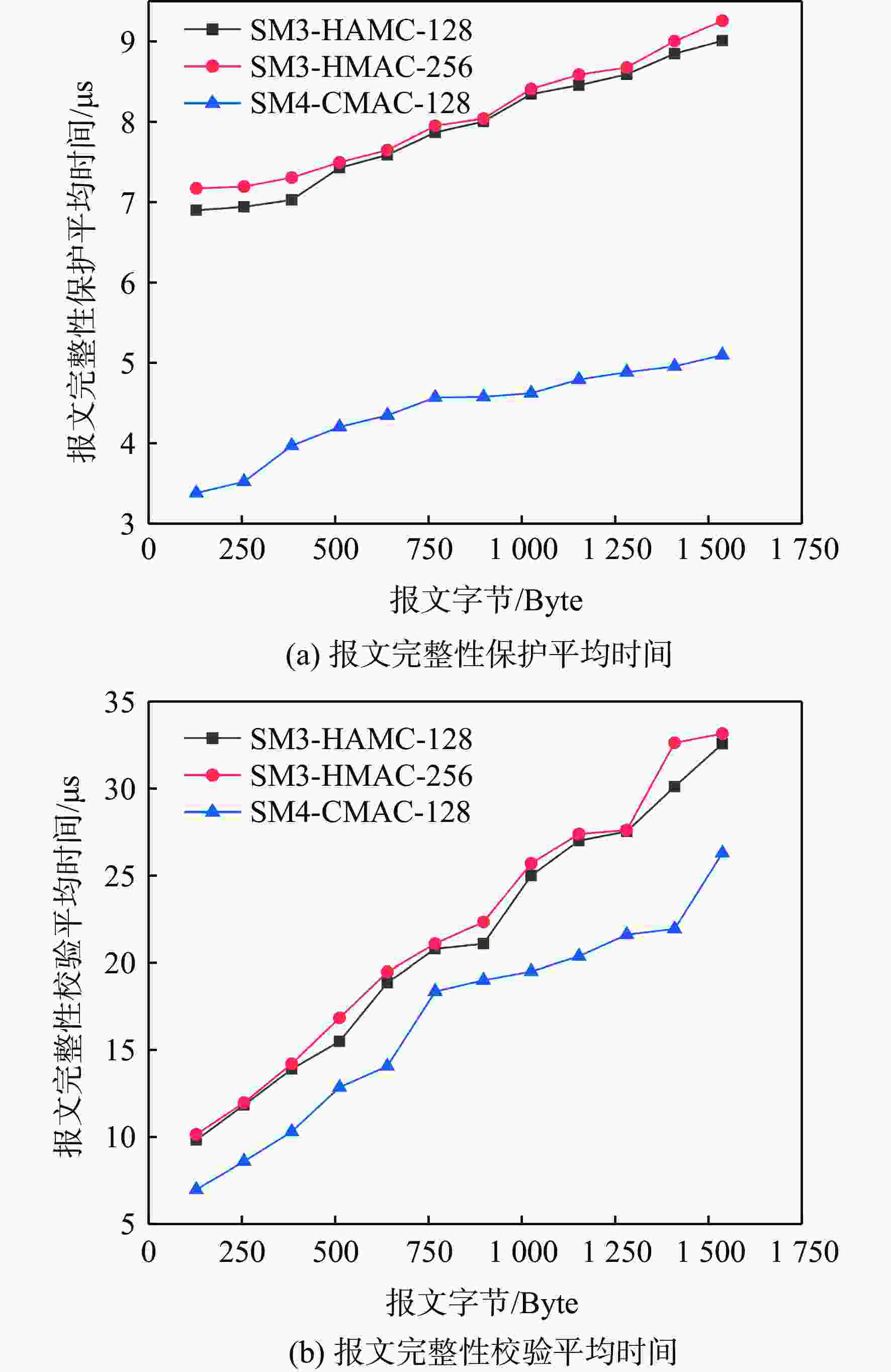
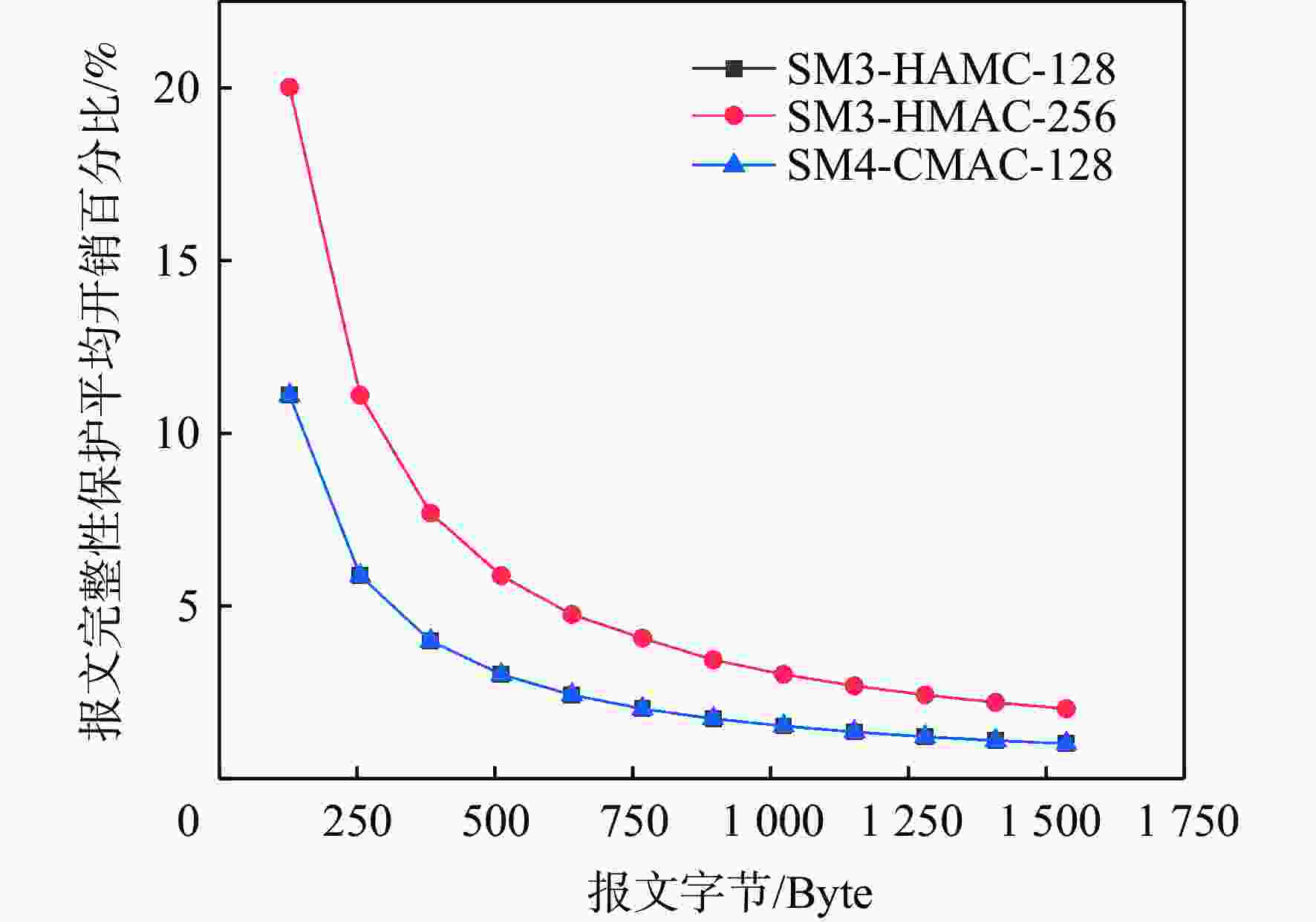
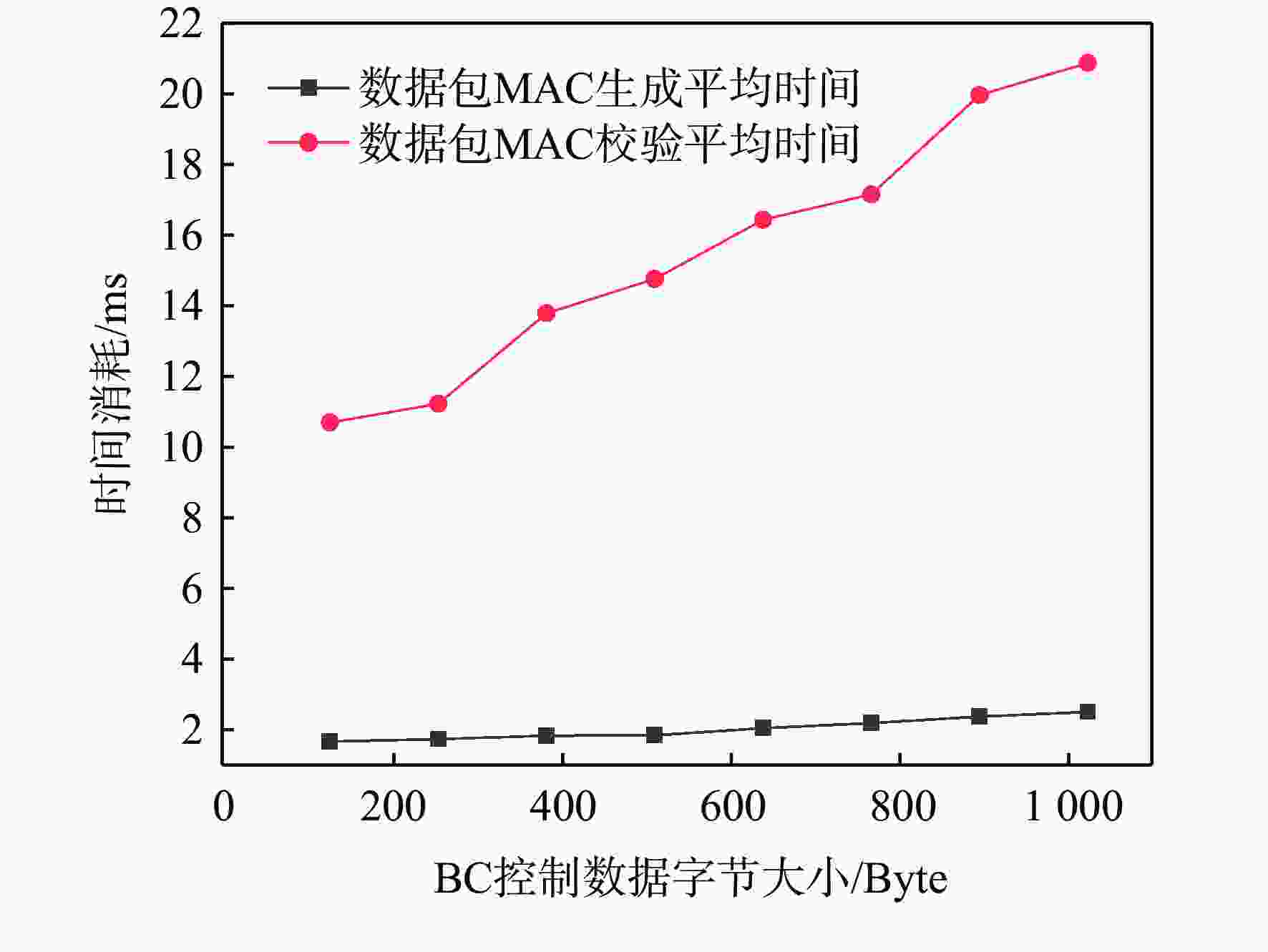
民用航空数字化通信频繁应用在未保护的信道中,极易遭受恶意的网络攻击,因此,在设计航空宽带系统的同时应当考虑数据链路的安全问题。基于此,设计基于L波段数字航空通信系统(LDACS)的安全架构,提出应用于LDACS的数据安全传输技术方案。针对用户数据,基于该报文结构使用国产密码保障用户数据的机密性和完整性;针对控制数据,使用时间效应流丢失容错认证(TESLA)协议实现广播控制(BC)数据的消息认证。实验结果表明:所提方案可以满足空/地之间安全传输报文中完整性报文的平均字节开销小于10%,并且协议的计算和时间开销也可满足该应用场景,从而实现数据端到端的安全传输。
-
关键词:
- 网络攻击 /
- L波段数字航空通信系统 /
- 安全传输 /
- 国密 /
- TESLA协议
Abstract:Due to its widespread use in unprotected channels, digital communication in civil aviation is extremely vulnerable to hostile network assaults. Therefore, when designing an aviation broadband system, data link security issues should be considered. A security architecture based on L-band digital aviation communication system (LDACS) was designed, and a data security transmission technology scheme applied to the LDACS system was proposed. For user data, the confidentiality and integrity of user data are guaranteed by using national cryptographic algorithms based on the user data message structure. For control data, the security authentication of broadcast control (BC) data is achieved by using the timed efficient stream loss tolerance authentication (TESLA) protocol. According to the experimental findings, the average byte overhead of integrity messages in secure transmission messages between air and ground is less than 10%. Additionally, the protocol's computation and time overhead can satisfy the application scenario, resulting in end-to-end secure data transmission.
-
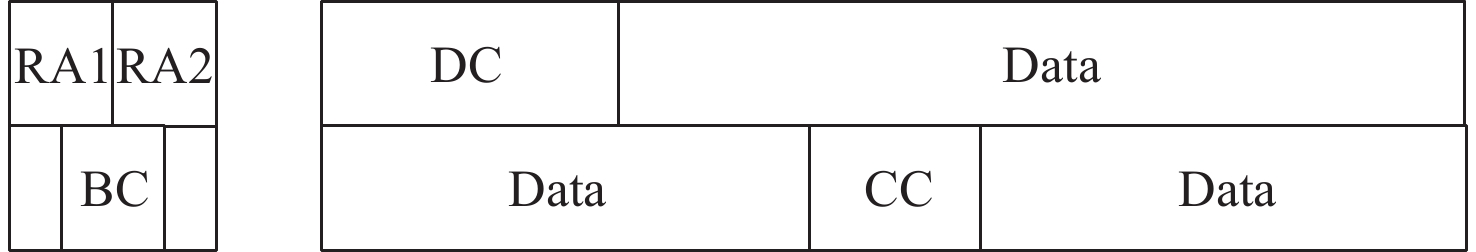
表 1 用户数据报文详细内容
Table 1. User data message details
报文结构 字段说明 报文头 协议类别 数据类型 标志位 源地址 目的地址 报文安全头 安全服务策略及参数 序列号 SN 填充位 Pad 报文控制域 分组标识符 PID 服务类别 SC 子网接入码 SAC 安全数据长度 LEN 用户数据安全加密域 用户数据 Payload 报文尾 校验位CRC 完整性校验码MAC 表 2 机密性加密套件
Table 2. Confidential encryption suite
方案 算法套件 字段值 用户数据机密性 Mode1: None 0x00 Mode2: SM4-ECB-128 0x01 Mode3: SM4-CBC-128 0x02 表 3 完整性加密套件
Table 3. Integrity encryption suite
方案 算法套件 字段值
用户数据
完整性Mode1: 128b tag, 128b key, SM3-HMAC-128 0x00 Mode2: 256b tag, 256b key,SM3-HMAC-256 0x01 Mode3: 128 b tag, 128b key, SM4-128-CMAC 0x02 表 4 不同方案性能比较
Table 4. Performance comparison of different schemes
方案 计算开销 通信开销 文献[30] $ (2n + 2){T_{\mathrm{m}}} + {T_{\mathrm{a}}} + 4{T_{\mathrm{h}}} + 2{T_{\mathrm{r}}} + 2n{T_{{\mathrm{xor}}}} $ $ 2{C_{\mathrm{m}}} + 2n\lambda + 2{C_{\mathrm{r}}} + 2n{C_{\mathrm{h}}} $ 文献[31] $ 2{T_{\mathrm{m}}} + (2n + 2){T_{\mathrm{h}}} + 3{T_{\mathrm{r}}} + 2n{T_{{\mathrm{xor}}}} $ $ 2{C_{\mathrm{m}}} + 2n\lambda + 3{C_{\mathrm{r}}} + 2n{C_{\mathrm{h}}} $ 本文方案 $ (2n + 2){T_{\mathrm{h}}} + 2{T_{\mathrm{r}}} + 2n{T_{{\mathrm{xor}}}} $ $ 2n\lambda + 2{C_{\mathrm{r}}} + 2n{C_{\mathrm{h}}} $ 表 5 TESLA协议密钥信息
Table 5. TESLA protocol key information
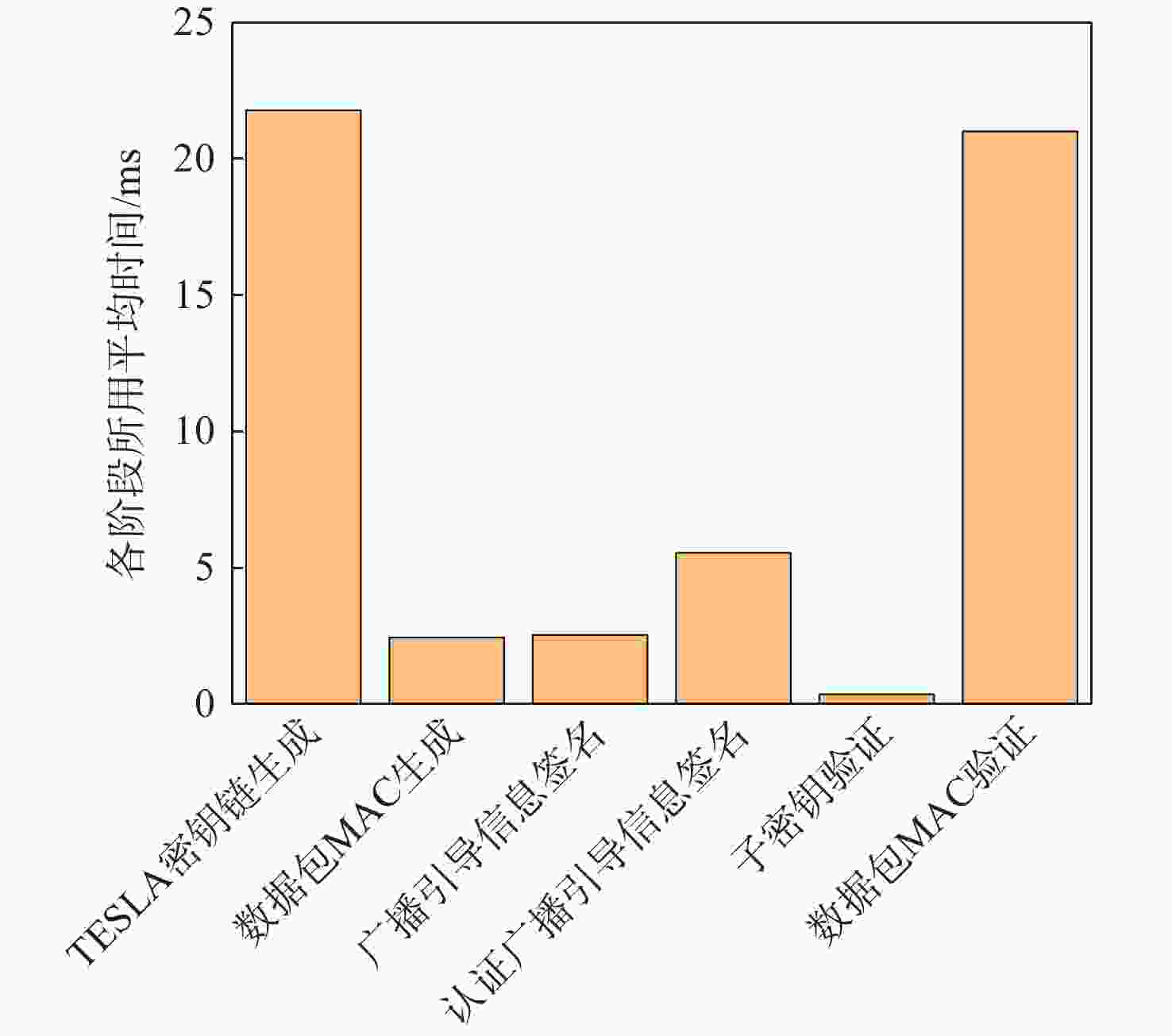
TESLA密钥链 密钥内容 初始密钥 f3c17b80285d265811a1677c13e31877 子密钥1 d76c10cfd422b2df44be6cc67da44991 子密钥2 9b91b5331384b09ebcc423a6c345e145 根密钥 1e1a5bd687d677ffcd8a55bd35baad1e -
[1] NIRAULA M, GRAEFE J, DLOUHY R, et al. ATN/IPS security approach: two-way mutual authentication, data integrity and privacy[C]//Proceedings of the Integrated Communications, Navigation, Surveillance Conference. Piscataway: IEEE Press, 2018: 1A3-1-1A3-17. [2] 牛文生. 基于天地一体化信息网络的智能航空客运系统[J]. 航空学报, 2019, 40(1): 522415.NIU W S. Intelligent air passenger transportation system utilizing integrated space-ground information network[J]. Acta Aeronautica et Astronautica Sinica, 2019, 40(1): 522415(in Chinese). [3] QIN H T, WANG H Y, XIE J L, et al. Development of flight data recorder for general aviation aircraft with real time data transmission[C]//Proceedings of the IEEE 3rd International Conference on Civil Aviation Safety and Information Technology. Piscataway: IEEE Press, 2021: 162-167. [4] 郜林, 王朕. 下一代航空宽带通信B-VHF系统[J]. 航空工程进展, 2018, 9(2): 168-176.GAO L, WANG Z. Research on B-VHF-the next generation system of air-ground broadband communication[J]. Advances in Aeronautical Science and Engineering, 2018, 9(2): 168-176(in Chinese). [5] MORIOKA K, LU X D, NAGANAWA J, et al. Flight tests for expanding aeromacs coverage and air-ground SWIM demonstration[C]//Proceedings of the Integrated Communications Navigation and Surveillance Conference. Piscataway: IEEE Press, 2021: 1-8. [6] 中国民用航空管理局. 中国民航新一代航空宽带通信技术路线图[EB/OL]. (2021-05-14) [2023-03-02]. http://www.caac.gov.cn/XXGK/XXGK/TZTG/202105/P020210518575556219897.pdf.Civil Aviation Administration of China. China civil aviation new generation aviation broadband communication technology roadmap [EB/OL]. (2021-05-14) [2023-03-02]. http://www.caac.gov.cn/XXGK/XXGK/TZTG/202105/P020210518575556219897.pdf. [7] BOSMAN P. SESAR European ATM master plan & SESAR2020[C]//Proceedings of the Integrated Communications, Navigation and Surveillance Conference. Piscataway: IEEE Press, 2017: 1-13. [8] International Civil Aviation Organization. LDACS draft SARPs [EB/OL]. (2020-02-01) [2023-03-02]. https://www.ldacs.com/wp-content/uploads/2018/03/WP05-DCIWG-2-LDACS_Draft_SARPs-Appendix.pdf. [9] BILZHAUSE A, BELGACEM B, MOSTAFA M, et al. Datalink security in the L-band digital aeronautical communications system (LDACS) for air traffic management[J]. IEEE Aerospace and Electronic Systems Magazine, 2017, 32(11): 22-33. doi: 10.1109/MAES.2017.160282 [10] MÄURER N. Paving the way for an IT security architecture for LDACS: a datalink security threat and risk analysis[C]//Proceedings of the Integrated Communications, Navigation, Surveillance Conference. Piscataway: IEEE Press, 2018: 1-27. [11] MÄURER N, BILZHAUSE A. A cybersecurity architecture for the L-band digital aeronautical communications system (LDACS)[C]//Proceedings of the 37th Digital Avionics Systems Conference. Piscataway: IEEE Press, 2018: 1-10. [12] MÄURER N, GRÄUPL T, SCHMITT C. Evaluation of the LDACS cybersecurity implementation[C]//Proceedings of the 38th Digital Avionics Systems Conference. Piscataway: IEEE Press, 2019: 1-10. [13] ROY S, CHANDRA A. On the design of variable filtered-OFDM based LDACS for future generation air-to-ground communication system[J]. IEEE Transactions on Circuits and Systems, 2022, 69(2): 644-648. [14] EPPLE U, SCHNELL M. Overview of legacy systems in L-band and its influence on the future aeronautical communication system LDACS1[J]. IEEE Aerospace and Electronic Systems Magazine, 2014, 29(2): 31-37. doi: 10.1109/MAES.2014.120092 [15] 朱永文, 喻兰辰晖. L波段数字航空通信系统研究[J]. 南京航空航天大学学报, 2022, 54(4): 700-714.ZHU Y W, YU L C H. Overview of L-band digital aeronautical communication system[J]. Journal of Nanjing University of Aeronautics & Astronautics, 2022, 54(4): 700-714(in Chinese). [16] 国家质量监督检验检疫总局, 中国国家标准化管理委员会. 信息安全技术 SM3密码杂凑算法: GB/T 32905—2016[S]. 北京: 中国标准出版社, 2017.General Administration of Quality Supervision, Inspection and Quarantine of the People’s Republic of China, Standardization Administration of the People’s Republic of China. Information security techniques—SM3 cryptographic hash algorithm: GB/T 32905—2016[S]. Beijing: Standards Press of China, 2017(in Chinese). [17] 国家密码管理局. SM4分组密码算法: GM/T 0002—2012[S]. 北京: 中国标准出版社, 2012.National Cryptography Administration. SM4 block cipher algorithm: GM/T 0002—2012[S]. Beijing: Standards Press of China, 2012(in Chinese). [18] CANCELA S, CALLE J D, FERNANDEZ-HERNANDEZ I. CPU consumption analysis of TESLA-based navigation message authentication[C]//Proceedings of the European Navigation Conference. Piscataway: IEEE Press, 2019: 1-6. [19] 3GPP. 3GPP specification status report[EB/OL]. (2022-12-21). [2023-03-02]. https://www.3gpp.org/DynaReport/status-report.htm. [20] HIGHTOWER K. Where airspace, ANSPs, and drones come together[C]//Proceedings of the Integrated Communications, Navigation and Surveillance Conference. Piscataway: IEEE Press, 2017: 1-8. [21] SLIM M, BEN MAHMOUD M S, LARRIEU N, et al. An aeronautical data link security overview[C]//Proceedings of the IEEE/AIAA 28th Digital Avionics Systems Conference. Piscataway: IEEE Press, 2009: 4. A. 4-1-4. A. 4-14. [22] BRESTEAU C, GUIGUI S, BERTHIER P, et al. On the security of aeronautical datalink communications: Problems and solutions[C]//Proceedings of the Integrated Communications, Navigation, Surveillance Conference. Piscataway: IEEE Press, 2018: 1A4-1-1A4-13. [23] MÄURER N, BILZHAUSE A. Paving the way for an it security architecture for LDACS: a datalink security threat and risk analysis[C]//Proceedings of the Integrated Communications, Navigation, Surveillance Conference. Piscataway: IEEE Press, 2018: 1A2-1-1A2-11. [24] SUHAIL HUSSAIN S M, FAROOQ S M, USTUN T S. A method for achieving confidentiality and integrity in IEC 61850 GOOSE messages[J]. IEEE Transactions on Power Delivery, 2020, 35(5): 2565-2567. doi: 10.1109/TPWRD.2020.2990760 [25] ZHOU C P, CHI Z Q, WANG Z D, et al. The Secure transmission method of distribution network messages based on SM3 algorithm[C]//Proceedings of the Power System and Green Energy Conference. Piscataway: IEEE Press, 2022: 586-590. [26] XU L. Secure transmission strategy of network communication layer relay based on satellite transmission[C]//Proceedings of the 2nd International Conference on Information Technology and Computer Application. Piscataway: IEEE Press, 2020: 268-271. [27] MAURER N, SCHMITT C. Towards successful realization of the LDACS cybersecurity architecture: an updated datalink security threat- and risk analysis[C]//Proceedings of the Integrated Communications, Navigation and Surveillance Conference. Piscataway: IEEE Press, 2019: 1-13. [28] NWADIUGWU W P, KIM D S. Ultrawideband network channel models for next-generation wireless avionic system[J]. IEEE Transactions on Aerospace and Electronic Systems, 2020, 56(1): 113-129. doi: 10.1109/TAES.2019.2914538 [29] ALMUZAINI N Z, AHMAD I. Formal analysis of the signal protocol using the scyther tool[C]//Proceedings of the 2nd International Conference on Computer Applications & Information Security . Piscataway: IEEE Press, 2019: 1-6. [30] MAURER N, GRAUPL T, GENTSCH C, et al. A secure cell-attachment procedure of LDACS[C]//Proceedings of the IEEE European Symposium on Security and Privacy Workshops . Piscataway: IEEE Press, 2021: 113-122. [31] LI X W, ZHANG Q Y, XU L X, et al. A compatible and identity privacy-preserving security protocol for ACARS[C]//Proceedings of the IEEE International Conference on Trust, Security and Privacy in Computing and Communications. Piscataway: IEEE Press, 2022: 1048-1053. -






 下载:
下载: